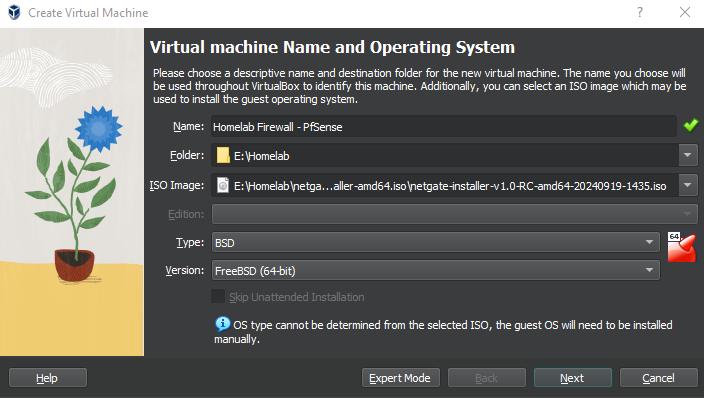
Deploying a pfSense VM for Our VirtualBox-Based Cyber Lab
In this module, we’ll set up a pfSense firewall virtual machine in VirtualBox to segment and secure the networks within our home lab.
This page is part of a broader series on creating a cybersecurity lab with VirtualBox. Click here - ADD LINK LATER to return to the main project description page.
Downloading pfSense
pfSense serves as the NAT router and firewall for the lab environment, so it must be the first virtual machine to start. Once pfSense is up and running, you can launch the rest of your VMs.
Whether you're building a lab in the cloud (GCP, AWS, Azure, ...) or on-premises, it's essential to design your network upfront. Be sure to account for future scalability, as redesigning the network later is far more challenging than planning it properly from the start. Refer to the diagram in the click here - ADD LINK LATER.
Recently, Netgate began requiring users to create an account and provide personal information to download pfSense CE ISO images—a change we're not particularly excited about. While this appears to be a measure to prevent misuse of pfSense Plus by third-party vendors, we'll show you how to download the ISO in a way that respects your privacy.
Head to Netgate PfSense's download page
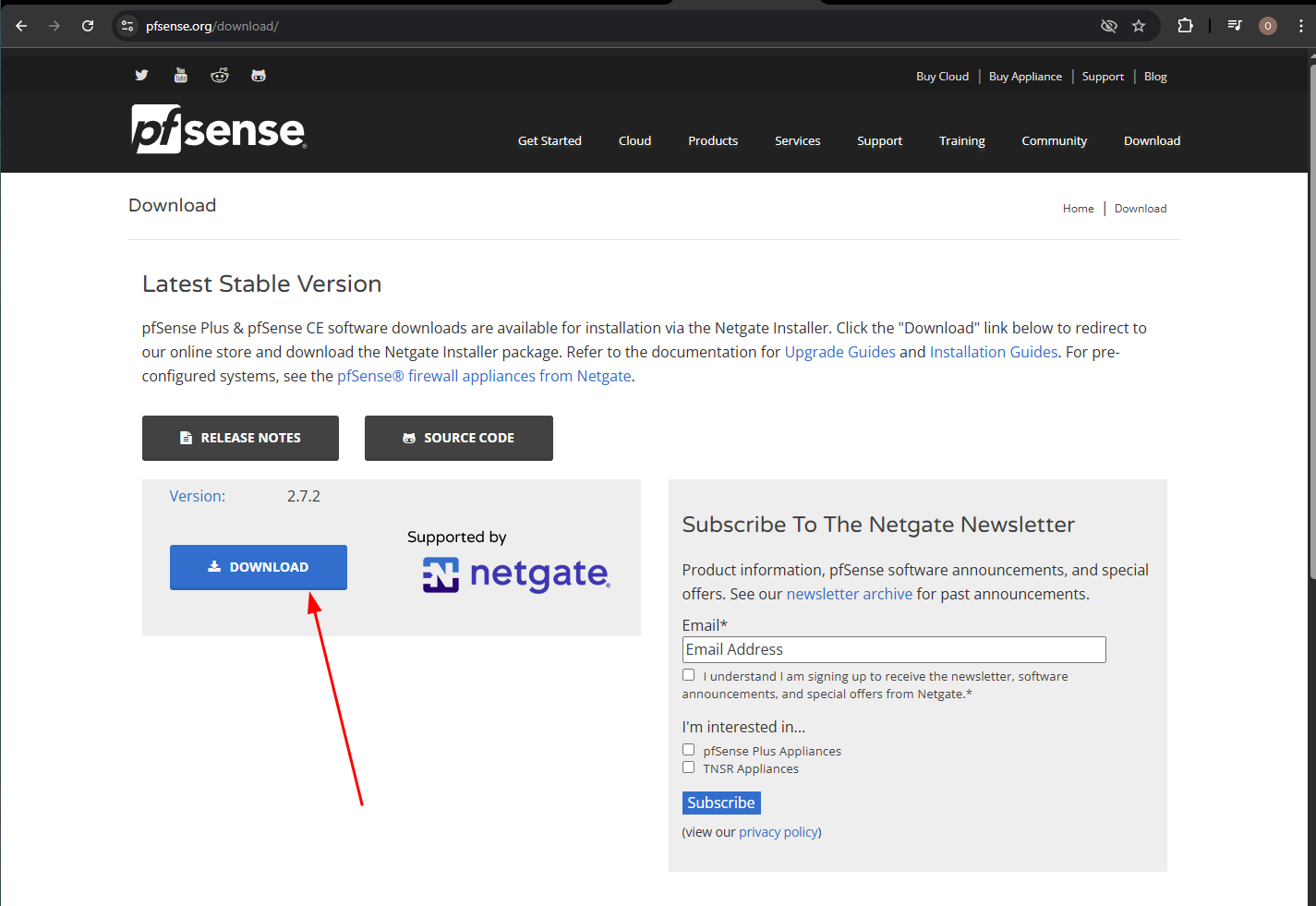

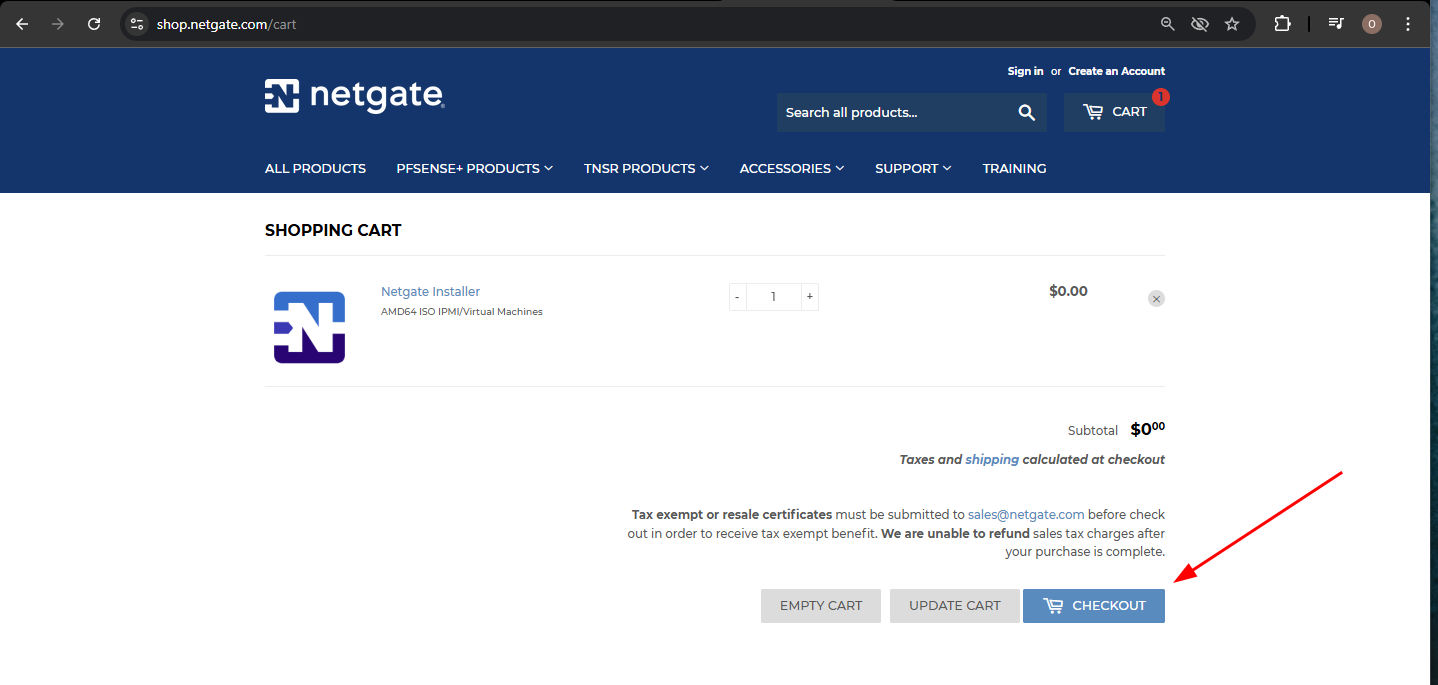
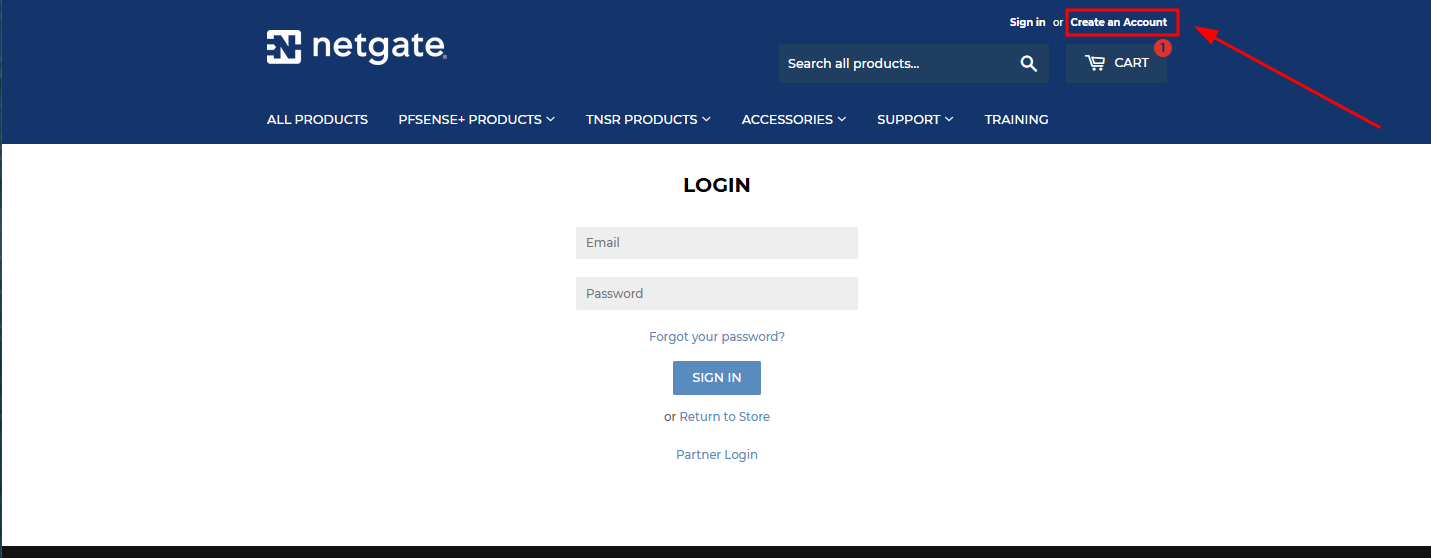
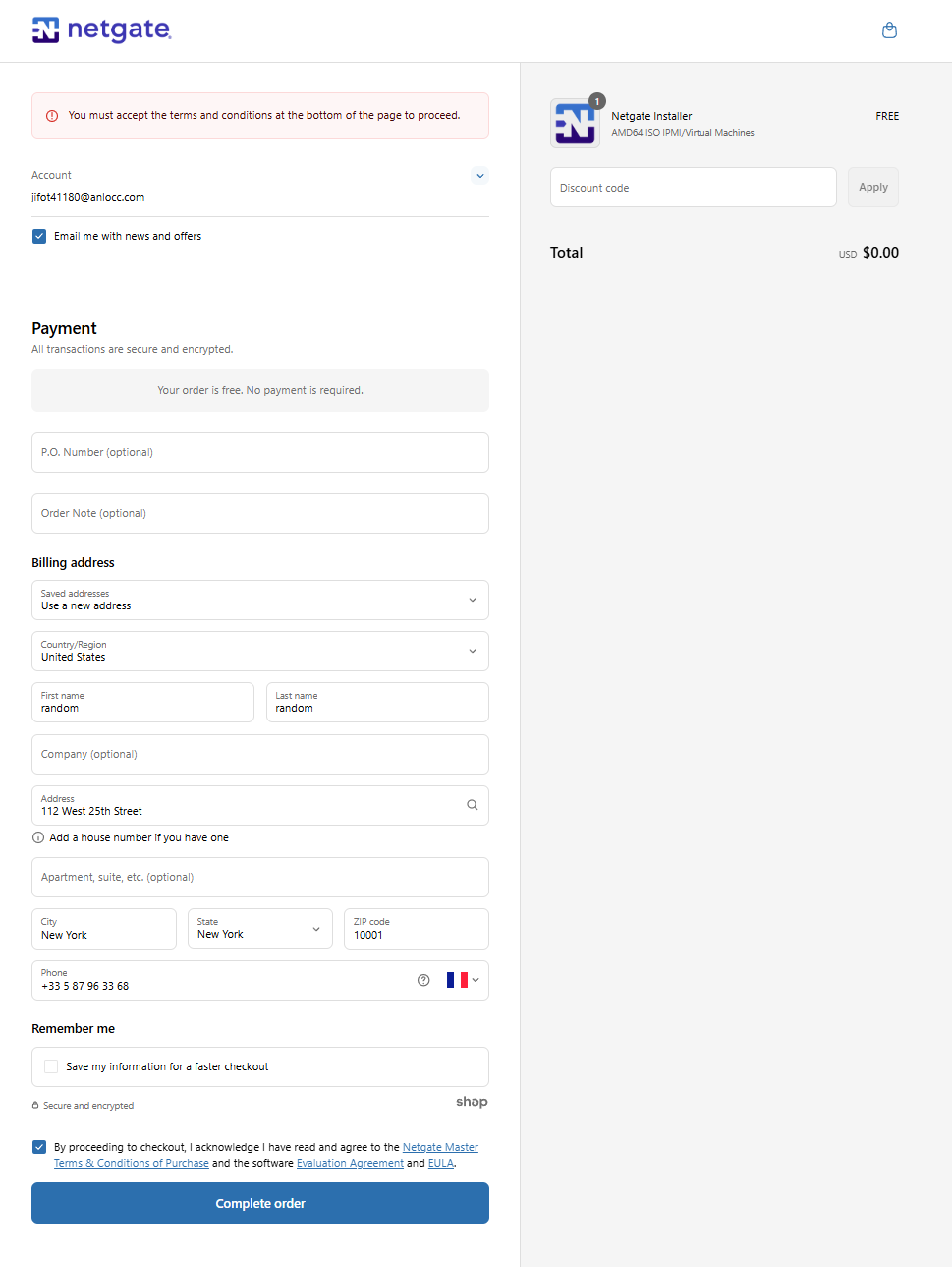
For the registration, you can use some free temporary mail services like Temp Mail
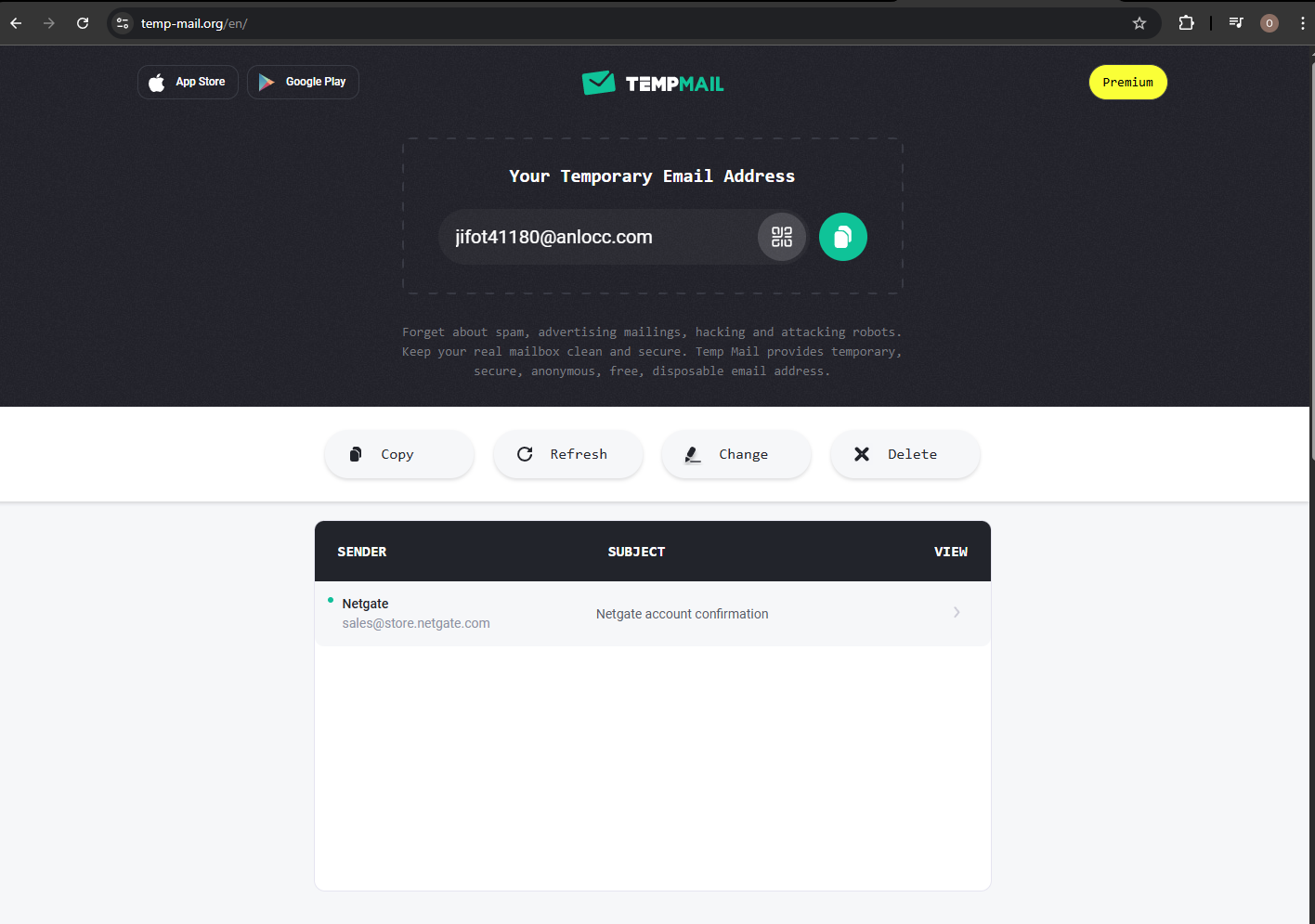
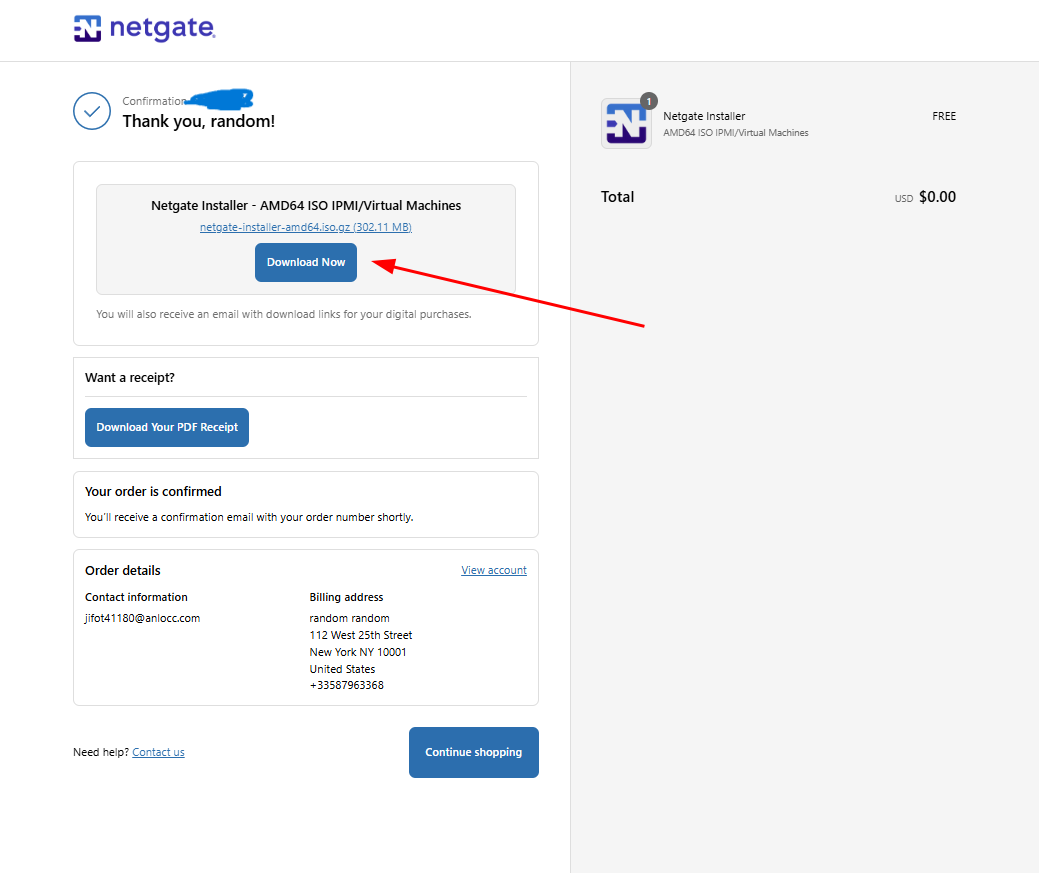
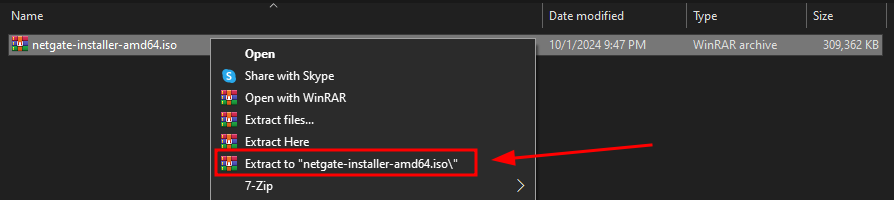
Once the ISO Image downloaded, you can you use a tool like Winrar to extract it.
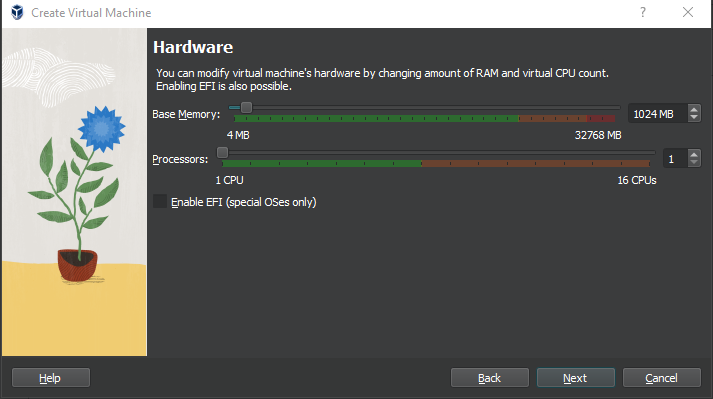
Depending on your infrastructure, pfSense doesn't require extensive resources, but it's always a good idea to allocate a reasonable amount to ensure smooth performance.
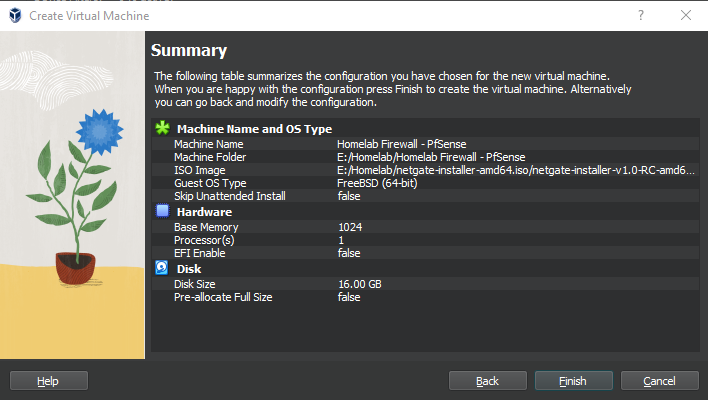
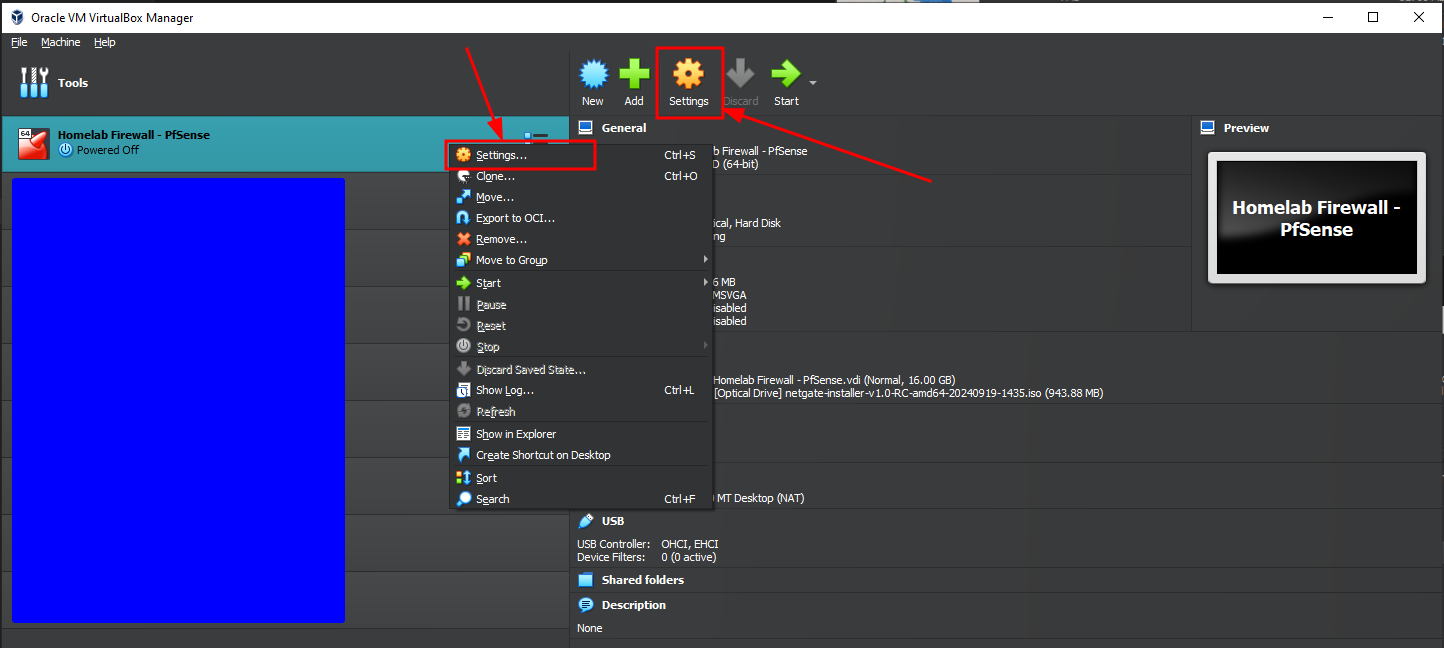

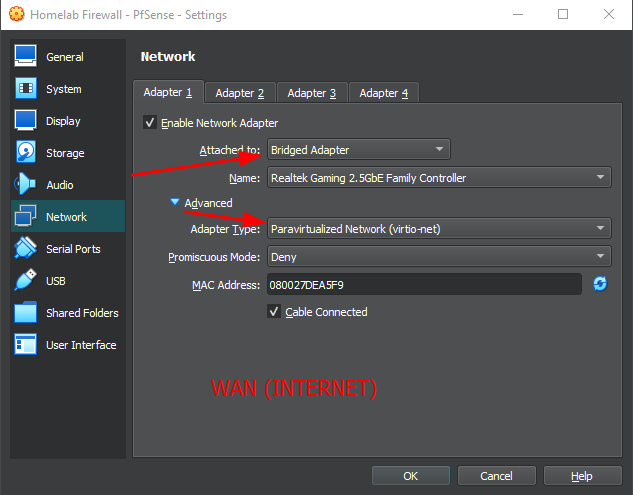
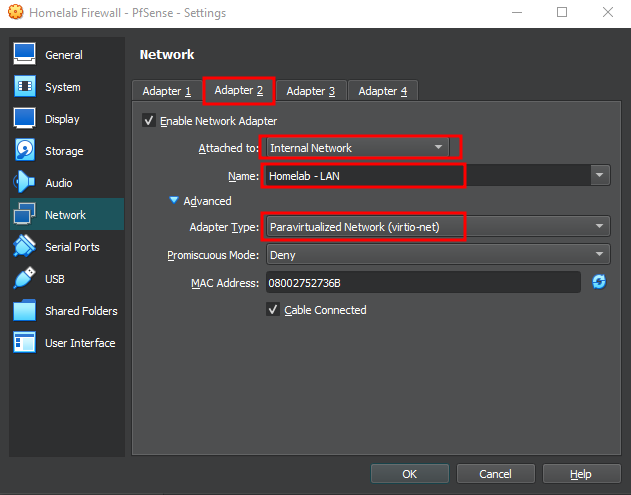
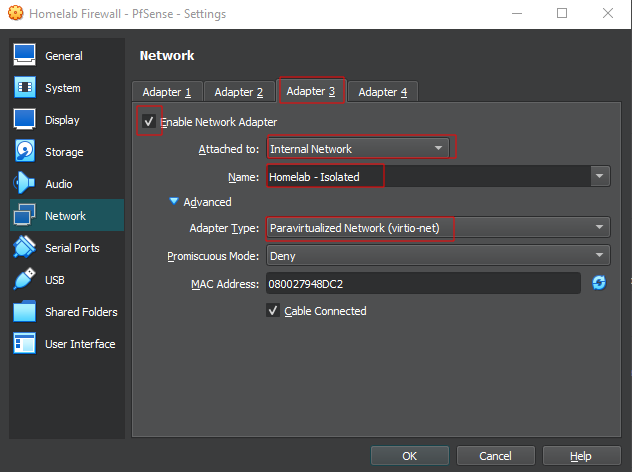
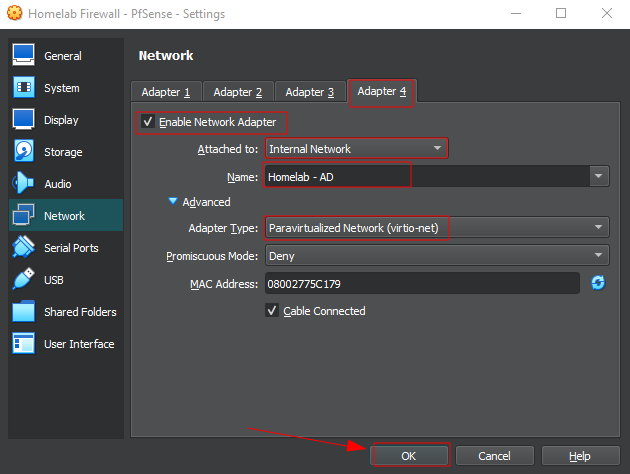
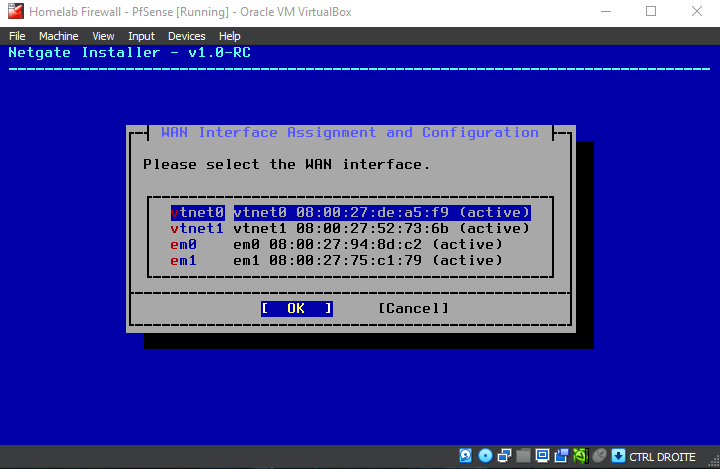
Setting up Network Interfaces on the VM
One of the most important steps ! Configuring the network interfaces.
For this lab, we will be using a paravirtualized network adapters (virtio-net) in VirtualBox (also available in other hypervisors) What is it you ask ?
- Virtio is a virtualization standard for network and disk device drivers.
- It's designed to provide high-performance I/O between guest and host by reducing overhead.
Advantages of Virtio-Net (Paravirtualized)
-
Performance
- Virtio drivers are lighter and closer to the hypervisor’s abstraction, so data flows with much less CPU usage.
- Higher throughput and lower latency compared to emulated NICs.
-
Lower Overhead
- Emulated NICs (like Intel PRO/1000) try to mimic real hardware, which adds unnecessary CPU cycles.
- Virtio bypasses this by exposing a virtual interface optimized for virtualization.
-
Better Packet Handling
- More efficient in terms of packet I/O, useful when simulating large volumes of network traffic (e.g., Snort, Zeek, packet captures).
-
Realism in Labs
- If you're testing logging, detection, or IDS systems, virtio gives you closer-to-realistic traffic flow without dropping packets due to CPU limitations.
-
Lower Disk & Memory Impact
- Less stress on system resources compared to traditional emulated devices.
If you're using a guest OS that doesn't support virtio drivers out of the box (e.g., older versions of Windows), you might have issues. In that case, you’d need to install the virtio drivers manually during OS setup.
In our lab, since we are simulating attack/detection chains with tools like ELK or Suricata, virtio-net is perfect. It makes sure our lab isn’t bottlenecked by networking performance, especially when sending logs or simulating attacks across multiple machines.
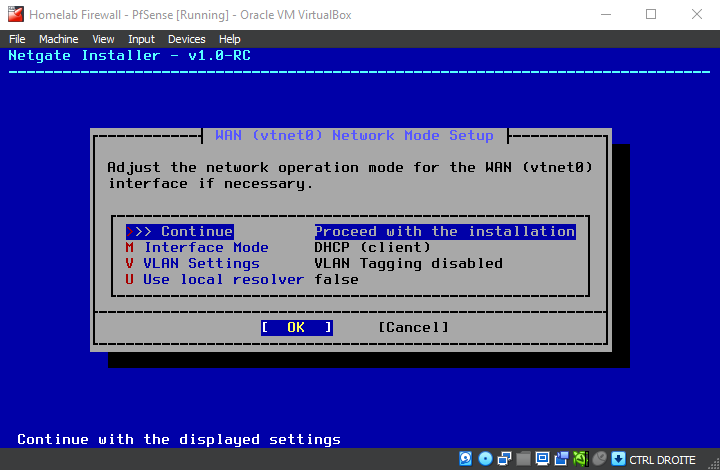
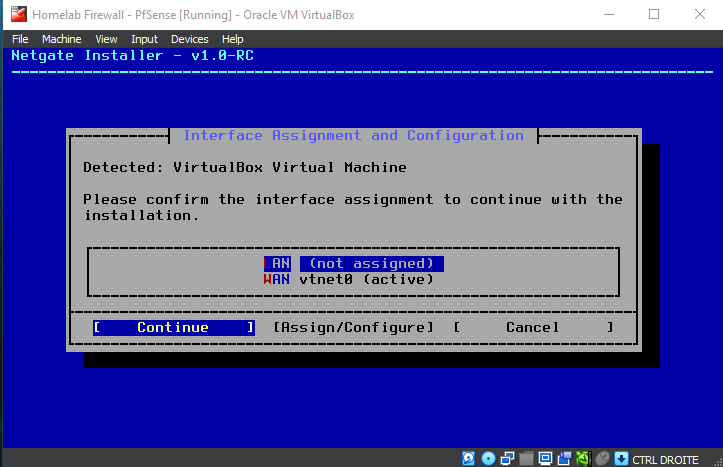
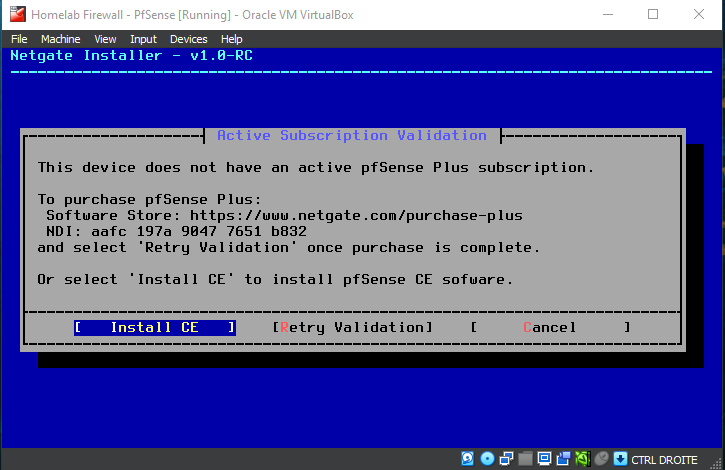
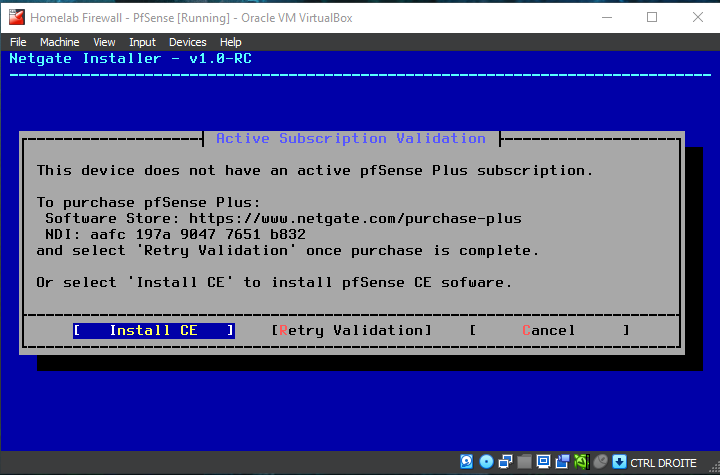
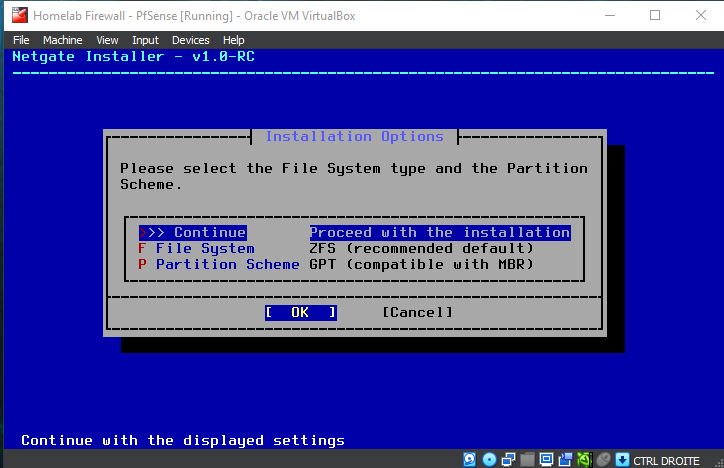
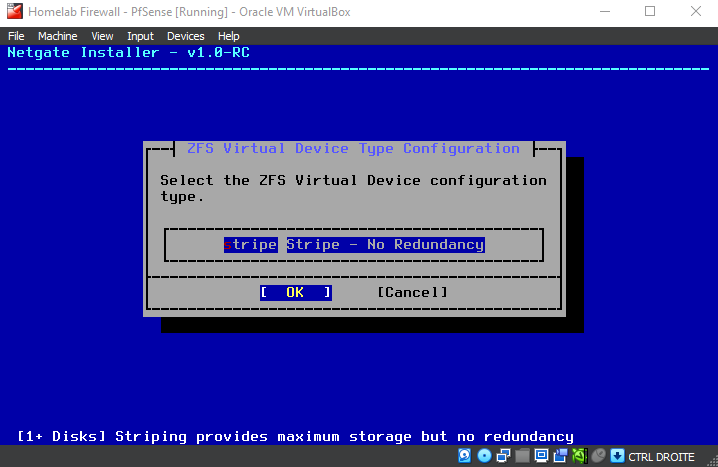
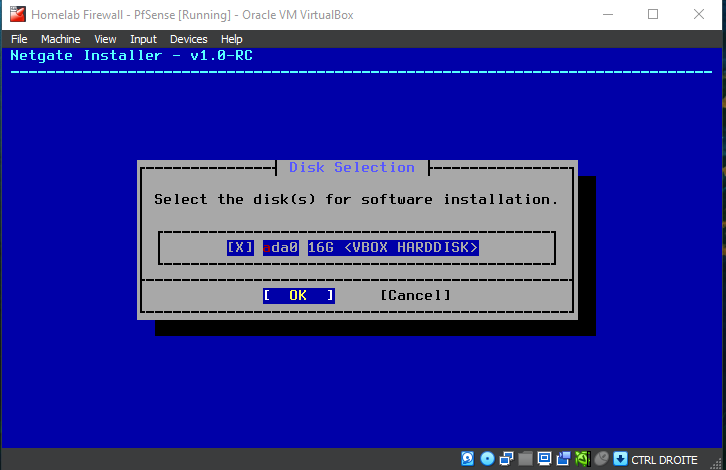
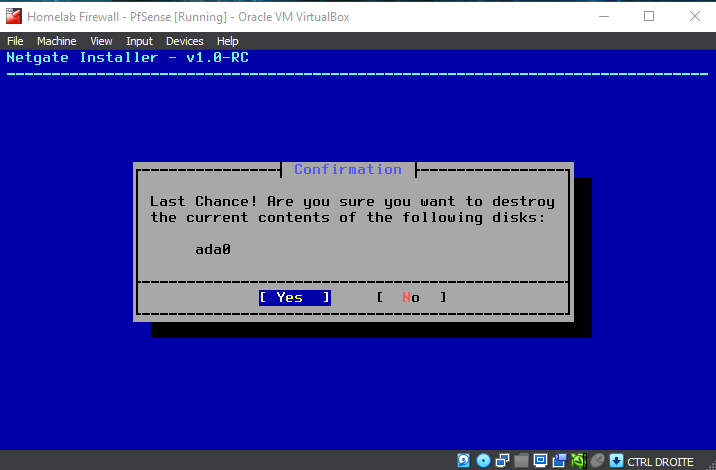
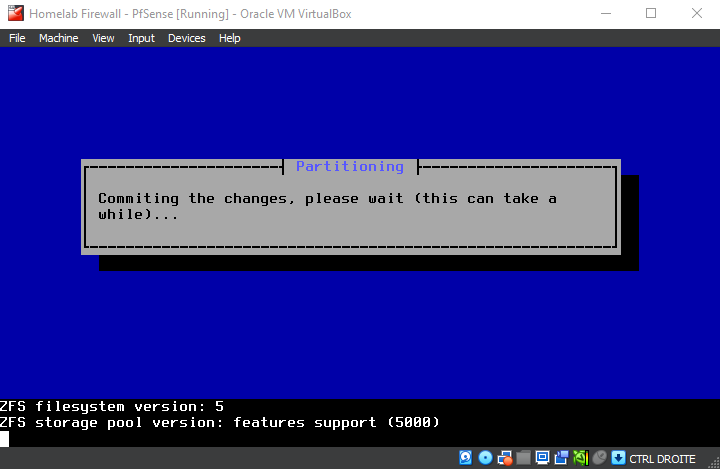
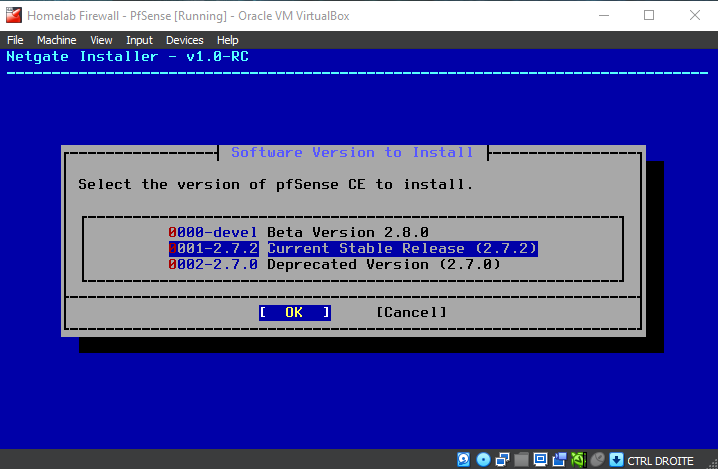
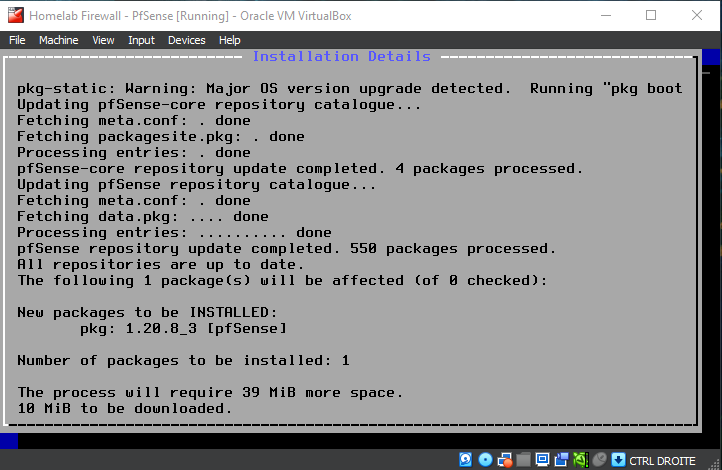
Be patient while the installer downloads core files and completes the installation...
should VLANs be set up now ? No
respecting the interface on the vm's adapters we set earlier